Access Control
Overview
QueryPie supports granting and revoking access permissions for Kubernetes clusters managed by your organization to users and groups. Access Control represents the final step in implementing and applying Kubernetes access permissions.
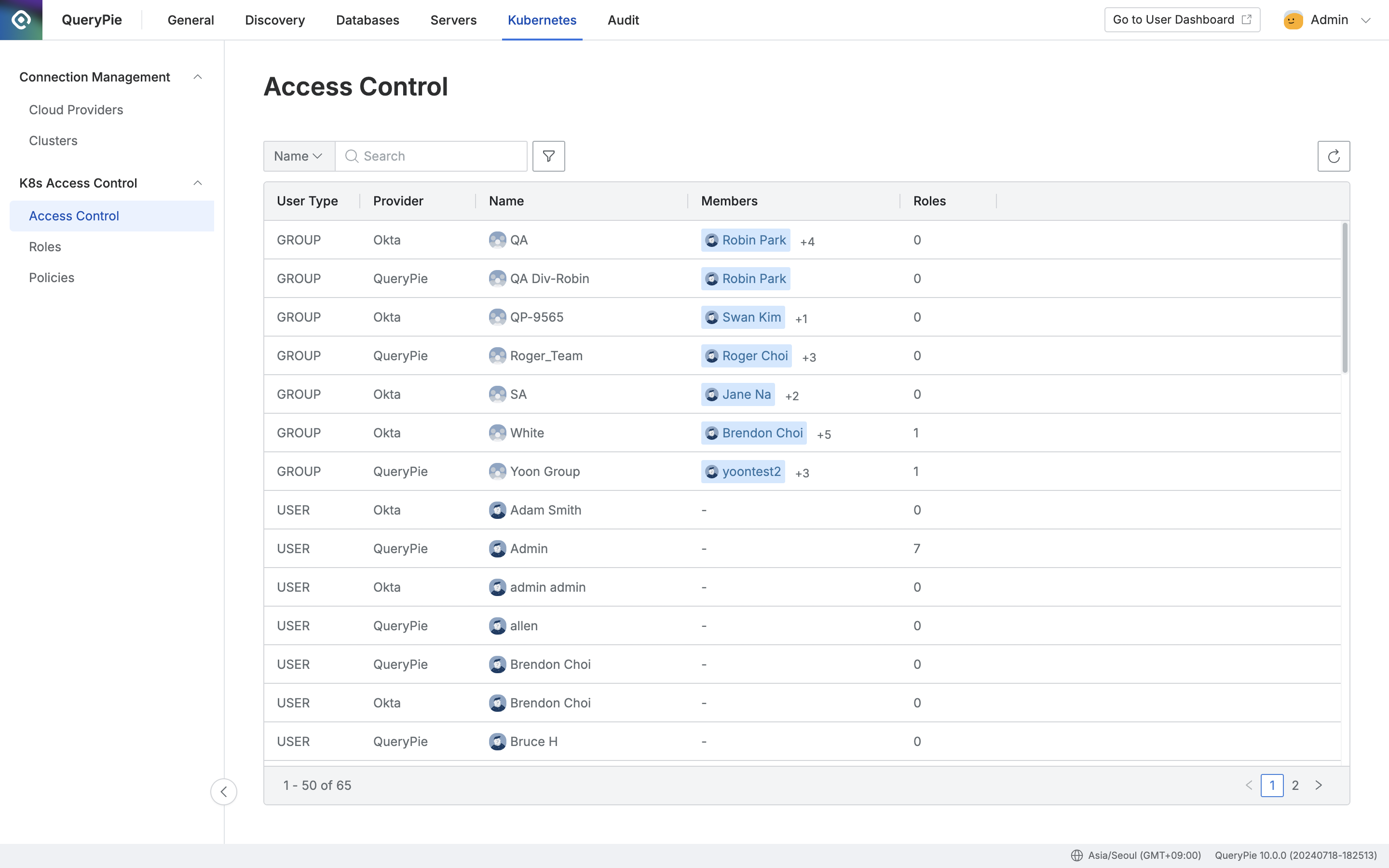
Administrator > Kubernetes > K8s Access Control > Access Control
Viewing Access Control Status
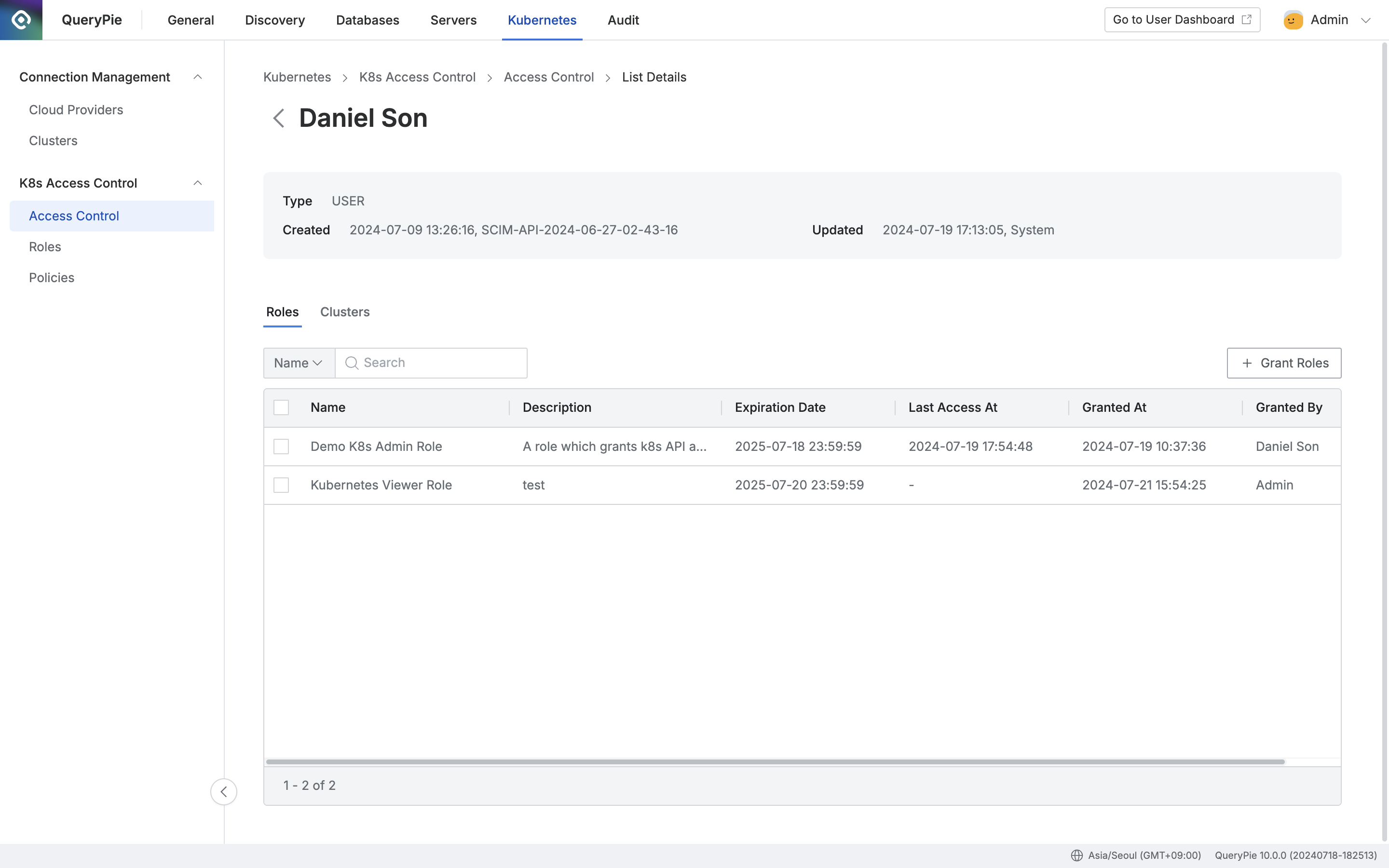
Administrator > Kubernetes > K8s Access Control > Access Control > List Details
Navigate to the Administrator > Kubernetes > K8s Access Control > Access Control menu.
You can search for users or groups by name using the search bar at the top left of the table.
You can click the filter button next to the search field to filter by user type and/or auth provider.
You can refresh the list of users/groups by clicking the refresh button at the top right of the table.
The table provides the following column information for each user/group:
User Type: The type of user or group.
Provider: The provider associated with the user or group.
Name: The name of the user or group.
Members: The list of members within a group.
Roles: The number of roles granted to the user or group.
Clicking on any row in the Access Control list will display detailed information about that user/group.
Roles
This tab is displayed by default and shows the list of assigned roles.
You can search for roles by name using the search bar.
The table provides the following column information for each role:
Name : Role name
Description : Detailed description of the role
Expiration Date : Expiration date of the granted role
Last Access At : The last time this role was accessed
Granted At : Date and time when the role was granted
Granted By : Administrator who granted the role
Clicking on any row will open a drawer with detailed information about that role.
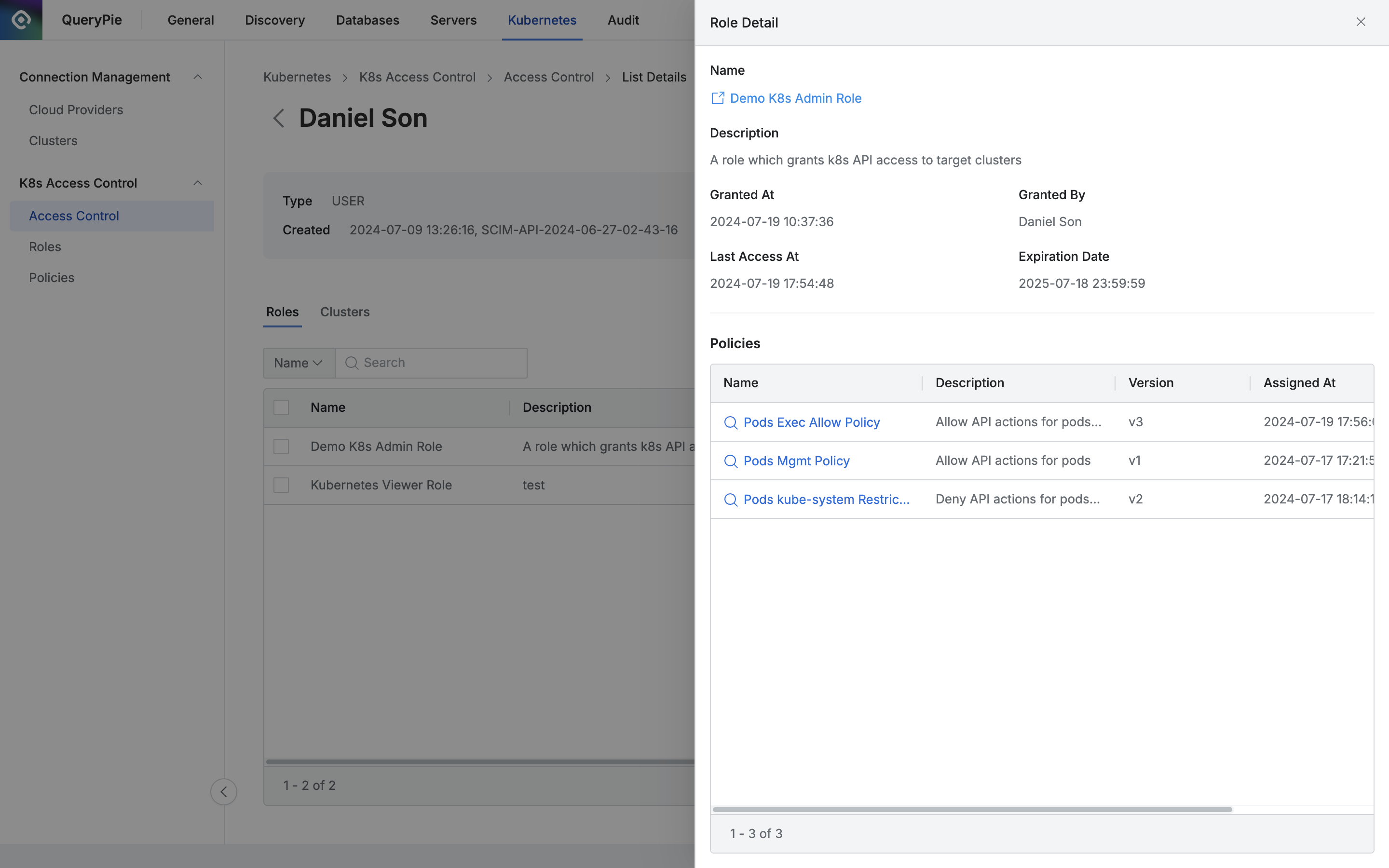
The top section displays basic information as follows:
Name : Role name (with a link to open the role details page in a new window)
Description : Detailed description of the role
Granted At : Date and time when the role was granted
Granted By : Administrator who granted the role
Last Access At : The last time this role was accessed
Expiration Date : Expiration date of the granted role
The bottom section lists policies assigned to the role, with the following details:
Name : Policy name (with a link to view policy details)
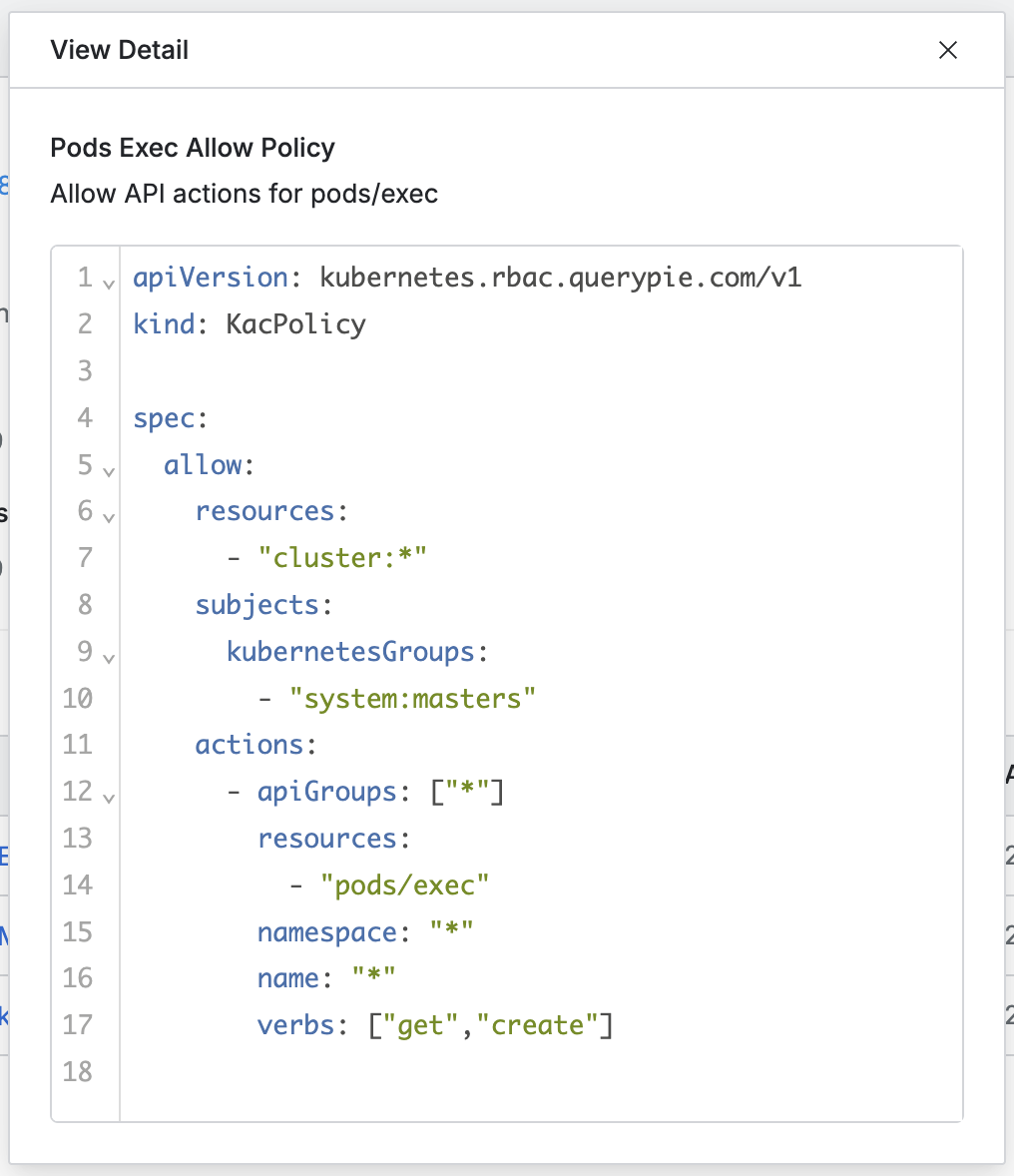
Description : Detailed description of the policy
Version : Policy version
Assigned At : Date and time when the policy was assigned
Assigned By : Administrator who assigned the policy
Clusters
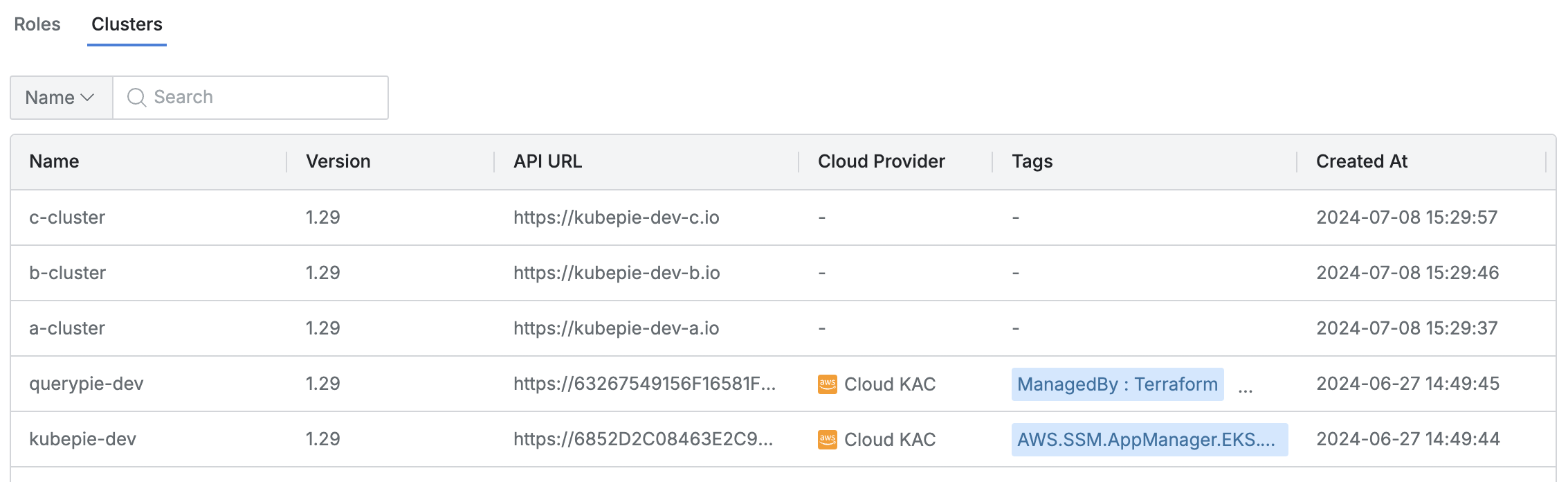
Lists Kubernetes clusters accessible via the assigned roles.
You can search for clusters by name and role name.
The table provides the following column information for each cluster:
Name : Cluster name
Version : Kubernetes version
API URL : API URL of the cluster
Cloud Provider : Connected platform (hyphenated for manual clusters)
Tags : List of tags attached to the cluster
Role : List of related roles
Created At : Date and time when the cluster was initially created
Updated At : Date and time when the cluster was last modified
Handling of Granted Roles Upon Expiration Date
When a role assigned to a user or group reaches its expiration date, the following actions occur:
The expired role is automatically removed from the Roles tab in the Access Control details page.
Any clusters accessible due to the expired role are automatically removed from the Clusters tab in the Access Control details page.
A "Role Revoked" log entry is created in the Audit > Kubernetes > Kubernetes Role History. The "Action By" field for this log entry is marked as "System".