[Okta] Provisioning Integration Steps
This guide provides instructions on how to implement SCIM integration between QueryPie and Okta using the App Integration Wizard (AIW). The SCIM functionality of this product is built according to the SCIM 2.0 standard based on RFC 7643. Therefore, when integrating with third-party Identity Providers, please follow this guide to collect the necessary information from QueryPie for integration.
Prerequisites
A subscription to the Lifecycle Management (LCM) license for the Okta IAM service is required.
Access to the Okta Admin Console to create an app and assign users/groups to the app.
Minimum Required Permissions
User
Edit users' application assignments
Group
Edit groups' application assignments
Application
Manage applications
Onhttps://help.okta.com/en-us/content/topics/security/ip-address-allow-listing.htm,Refer to the Okta IP range allowlist to identify the IP range for your Okta tenant and allow exceptions for inbound traffic.
The QueryPie product must be installed along with the license.
An account with QueryPie Owner or System Admin role permissions is required.
Enable Provisioning step must be completed first.
Integration Steps
Once the prerequisites are complete, follow these steps to perform the SCIM integration.
Creating a Custom SCIM App in Okta
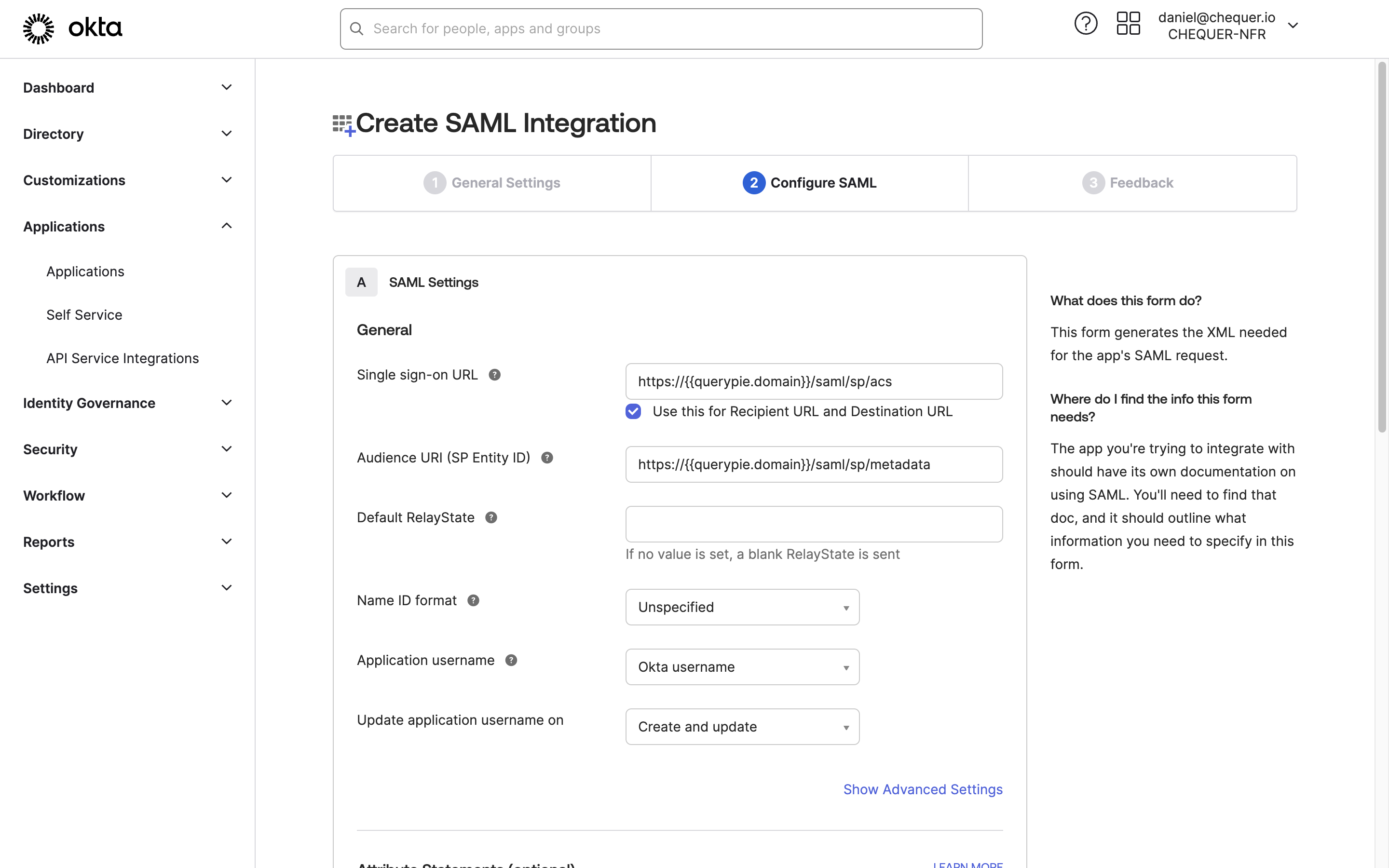
Okta Admin Console > Applications > Applications > Create App Integration > SAML 2.0 > Configure SAML
Log in to the Okta service with an admin account.
Click the
Adminbutton in the upper right corner to access the admin console.In the Okta admin page, navigate to Applications > Applications from the left panel.
Click the
Create App Integrationbutton.For a custom SCIM integration, select the SAML 2.0 option as the sign-in method, then click Next.
In the General Settings step, fill in the General Settings as needed and click the
Nextbutton at the bottom.App name : Enter an identifiable application name.
App logo : Upload a logo for user identification.
In the Configure SAML step, fill in the SAML Settings as needed and click the
Nextbutton at the bottom.Single sign-on URL : https://{{querypie.domain}}/saml/sp/acs
Audience URI (SP Entity ID) : https://{{querypie.domain}}/saml/sp/metadata
Attribute Statements (optional) : Enter the necessary attributes for the QueryPie URL as follows:
Name: firstName
Name format: Unspecified
Value: user.firstNameName: lastName
Name format: Unspecified
Value: user.lastNameName: email
Name format: Unspecified
Value: user.emailName: loginId
Name format: Unspecified
Value: user.login
In the Feedback step, select
I'm an Okta customer adding an internal app, then click theFinishbutton at the bottom.After creating the application, go to the General tab at the top and click the
Editbutton next to App Settings.Select SCIM for the Provisioning field, then click the
Savebutton.Complete the SSO integration by following the Setting Up QueryPie Application Integration Information in Okta and Setting Up Okta Integration and Synchronization in QueryPie sections in Okta Integration guide before proceeding to the next steps.
Okta-QueryPie Provisioning Integration
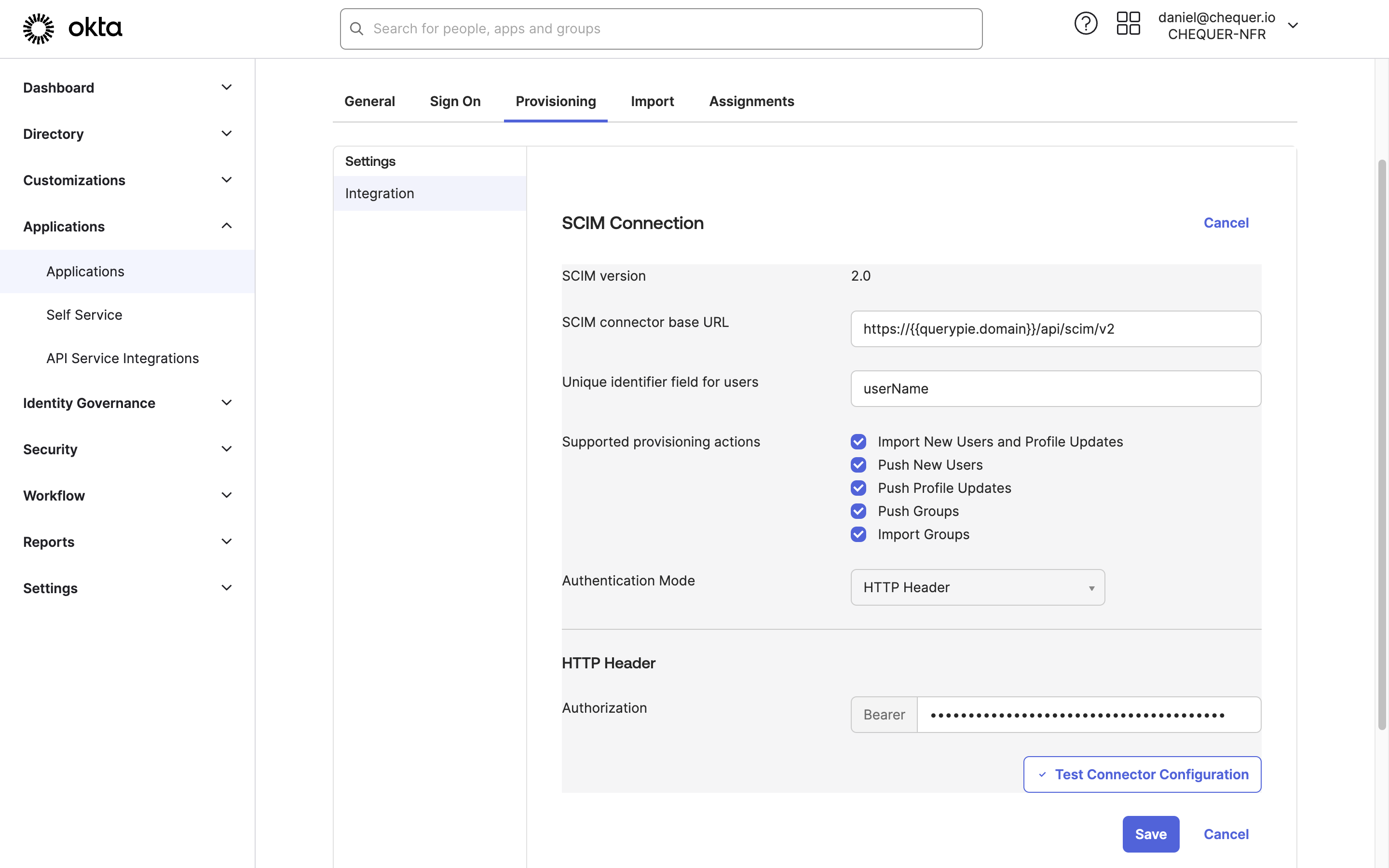
Okta Admin Console > Applications > Applications > Custom SCIM App > Provisioning > Integration
Complete the Enable Provisioning step first.
Go to the Provisioning tab of the SCIM App created in Okta.
Click the
Editbutton next to SCIM Connection and fill in the following values:SCIM connector base URL : Enter the SCIM Endpoint value obtained from QueryPie.
Unique identifier field for users : “userName”
Support provisioning action :
- Import New Users and Profile Updates
- Push New Users
- Push Profile Updates
- Push Groups
- Import Groups
Authentication Mode : “HTTP Header”
HTTP Header > Authorization : Insert the SCIM-specific access token generated from QueryPie.
Click the
Test Connector Configurationbutton to perform a connection test.If a popup appears with the message “Connector configured successfully”, click the
Closebutton.
Click the
Savebutton at the bottom to save the connection settings.
Enabling and Checking SCIM API
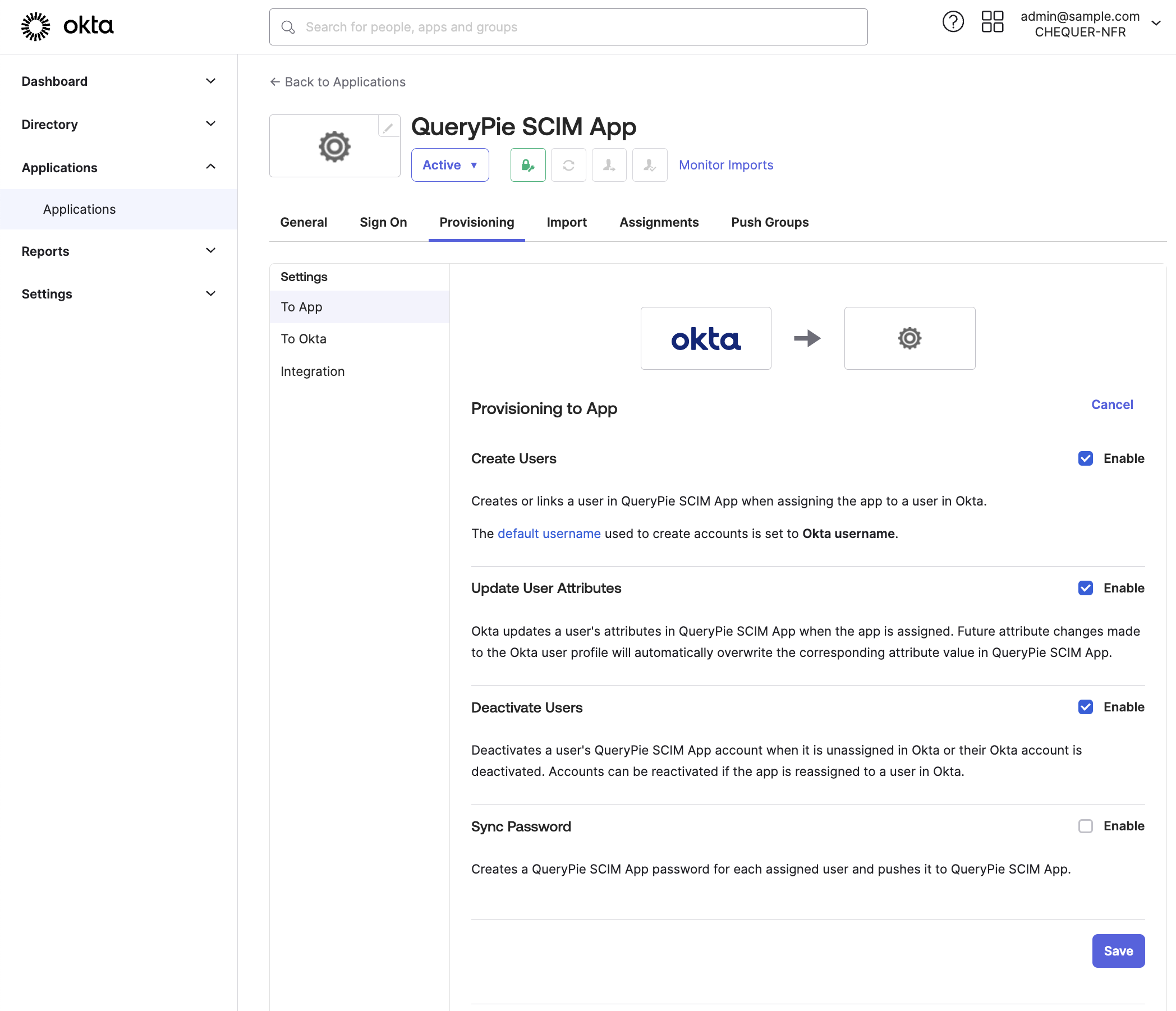
Okta Admin Console > Applications > Applications > Custom SCIM App > Provisioning > To App
Go to the To App screen of the Provisioning tab of the SCIM App created in Okta.
Click the
Editbutton next to Provisioning to App.Enable the following settings by checking their boxes, then click
Save:Create Users : Adds users to the app when they are assigned.
Update User Attributes : Updates the app when user profile updates occur.
Deactivate Users : Deactivates users in the app when they are deactivated.
Click the
Go to Profile Editorbutton under QueryPie SCIM App Attribute Mappings.Click the
Mappingsbutton under Attributes.In the popup, go to the tab labeled “Okta User to {Custom App Name}” among the two tabs at the top.
Map the items according to your custom settings and click the
Save Mappingsbutton at the bottom.Click the
Apply updates nowbutton at the bottom.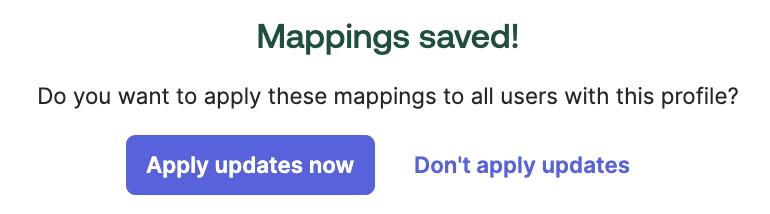
Syncing Additional Attributes
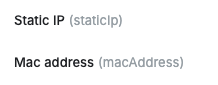
Some attributes like
staticIpandmacAddressin the QueryPie profile are not imported separately during SCIM Integration. These attributes include:secondEmail
mobilePhone
postalAddress (Map this as “formatted” according to the SCIM schema.)
staticIp (QueryPie-specific custom attribute)
macAddress (QueryPie-specific custom attribute)
If these attribute details need to be synced as well, you can add custom attributes in the IdP like Okta and map them for synchronization. [Okta Example]
Go to SCIM App > Provisioning tab > To App and click
Go to Profile Editorat the bottom.
Click the
Add Attributebutton.
Add the attributes needed for synchronization.
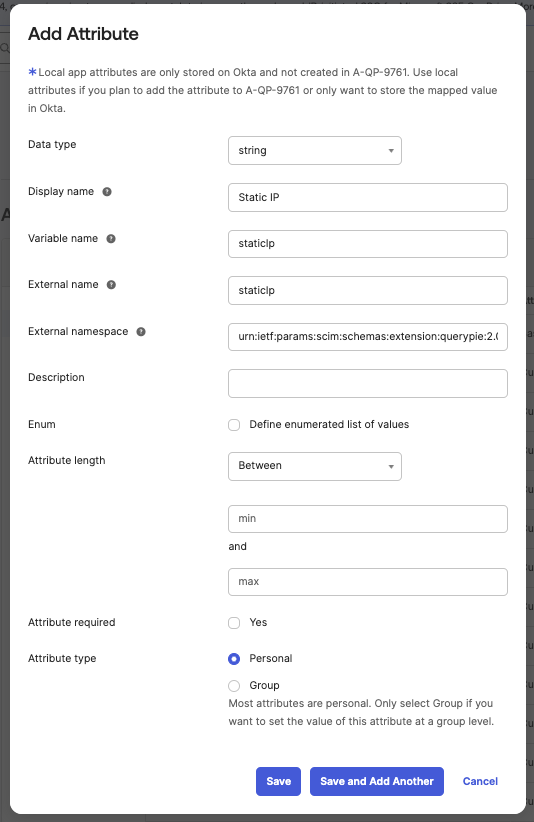
Data type : Select string, as in QueryPie.
Display name : Enter the name to be displayed in Okta.
Variable name & External name : Enter the variable name for the custom attribute to be synced.
You can verify the variable name in parentheses in the QueryPie user profile.
External namespace : Enter this information.
CODEurn:ietf:params:scim:schemas:extension:querypie:2.0:UserClick
SaveorSave and Add Anotherto save.Then click the
Mappingsbutton.
In the prompt, select the second tab (Okta → {APP}) at the top.

Map the newly created Custom Attribute to the appropriate attribute in the IdP and click
Save Mappingsto save the settings.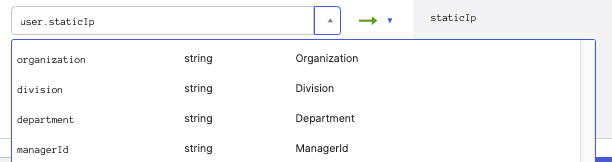
Assign users to the app afterward.
Checking User Provisioning
Return to the SCIM app and assign users through the
Assignbutton options in the Assignments tab.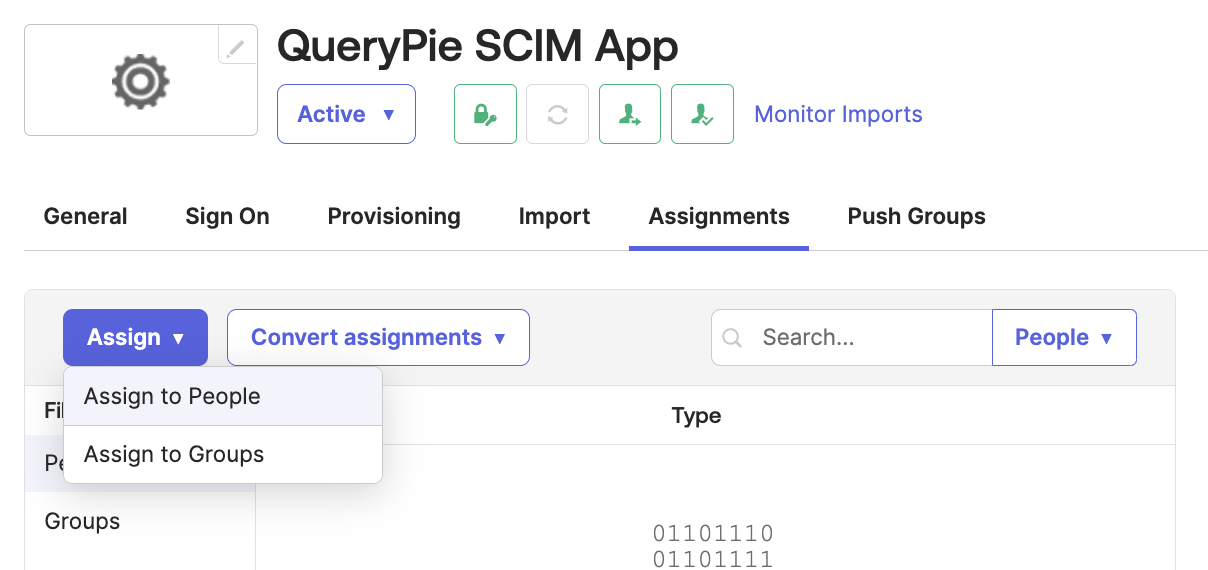
Okta Admin Console > Applications > Applications > Custom SCIM App > Assignments
Assign to People : Assign individual users.
Assign to Groups : Assign groups of users.
Return to the QueryPie app and navigate to the Administrator > General > User Management > Users menu to verify that users have been pushed correctly.
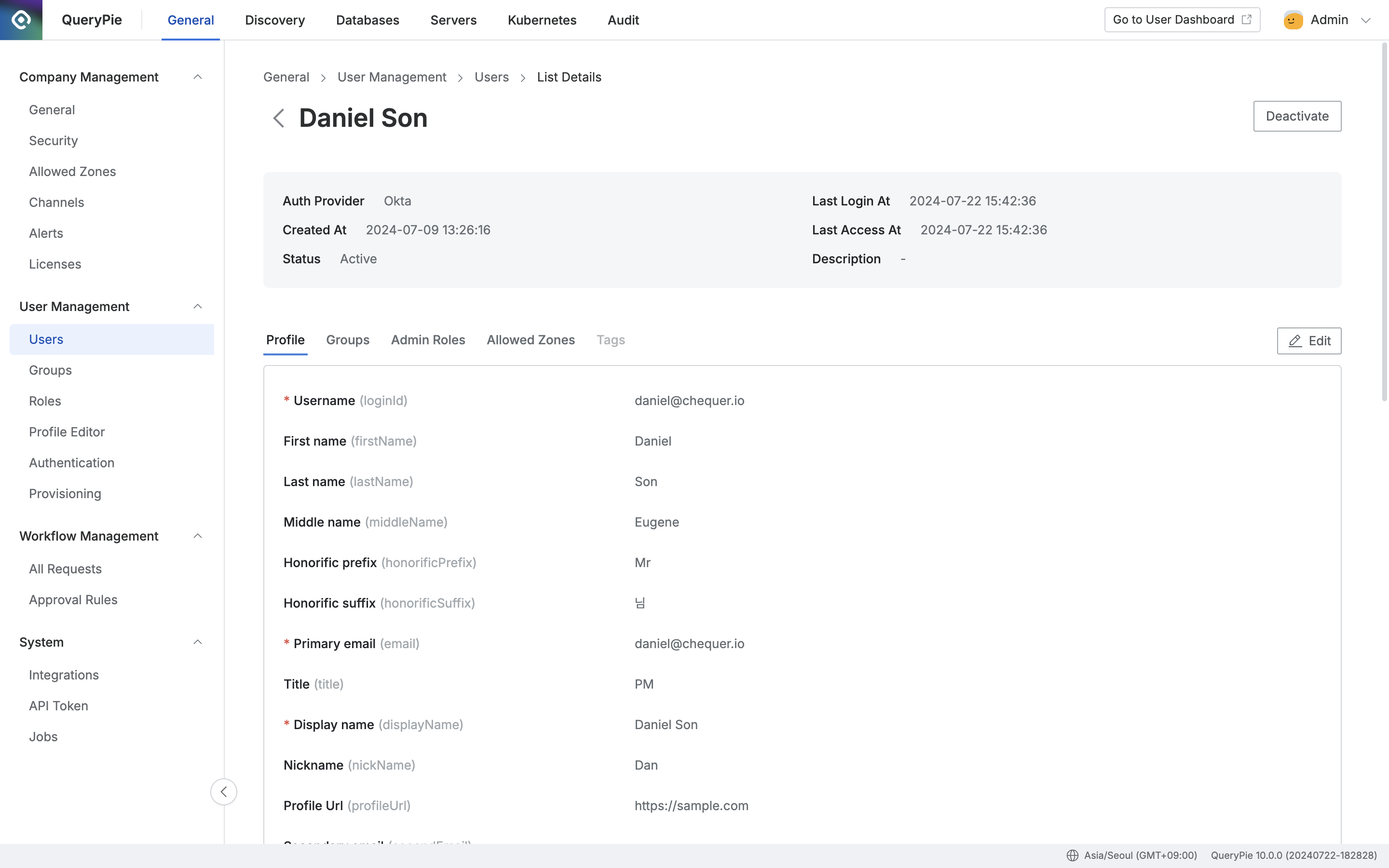
Administrator > General > User Management > Users > List Details
Checking Group Provisioning
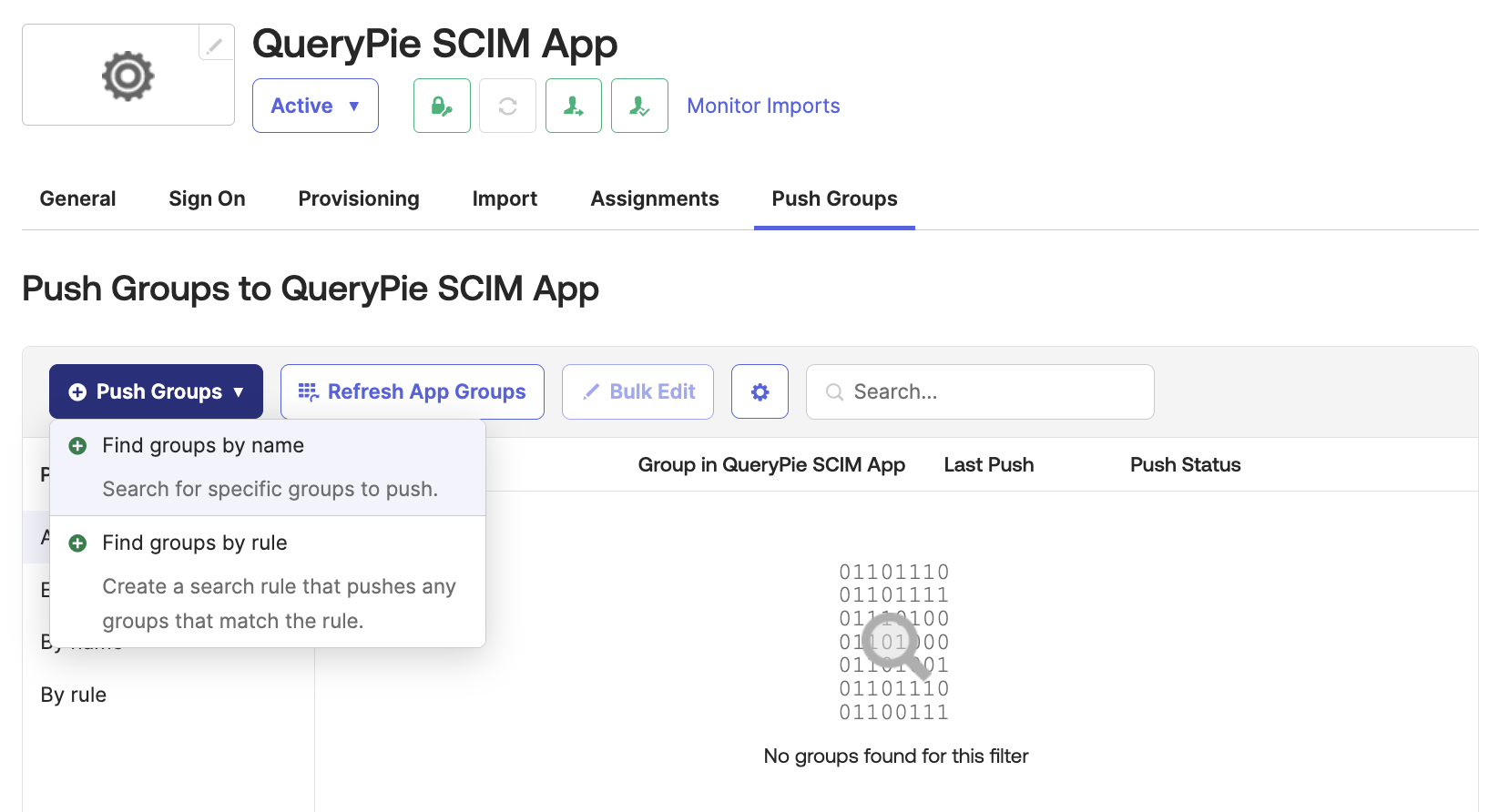
Okta Admin Console > Applications > Applications > Custom SCIM App > Push Groups
Return to the SCIM app and assign groups through the
Push Groupsbutton options in the Push Groups tab.Find groups by name : Search for and assign groups by their names.
Find groups by rule : Define a search rule and assign groups that meet the criteria.
Return to the QueryPie app and navigate to Administrator > General > User Management > Groups to verify that groups have been pushed correctly.
If the Auth Provider created by the IdP, such as Okta, is not QueryPie, it is recommended to unlink and delete the group in the IdP. Deleting groups in QueryPie could disrupt the management flow in the IdP, making it difficult to push the deleted group name back into the product.