[Internal Network] Forward Slack DM Workflow Results
Overview
Enabling Slack DM Notifications allows approvers in the workflow to approve or reject within Slack. If QueryPie is located within the internal network, opening inbound communication from the Slack service IP ranges is necessary to receive approval/rejection results. However, since Slack does not disclose its IP ranges, direct reception is hard to achieve.
As a result, a resource capable of serving as a reverse proxy to receive and deliver workflow approval/rejection results from Slack in the middle of inbound communication between Slack and QueryPie is needed. As a workaround, we introduce the use of Okta's workflows, which relatively disclose its allowed IP ranges, to route requests and deliver them. Through this method, you can complete the workflow processing between Slack and QueryPie without requiring separate operational resources.
Reference Link: YouTube
You should verify the IP range of the corresponding tenant by referring to the Okta IP range allowlist within thehttps://help.okta.com/en-us/content/topics/security/ip-address-allow-listing.htm page. Preemptive inbound traffic exceptions should be allowed accordingly.
To implement the following measures, a subscription to the Okta IAM service is required, and access to the Okta Workflows service must be available. [Even if you are not subscribed to the Okta Workflows license, if you have at least a Universal Directory (UD) + Single Sign-On (SSO) licenses, you can activate Okta Workflows through a case opening and utilize up to 5 flows for free.]
Setting Up Okta Workflows
To configure these settings, users need to have permission to access the Okta Workflows console. Okta Super Administrator privileges are required, and users must be assigned to the Okta Workflows application to access it.
You can download pre-built Okta workflow templates in advance through the link provided below.
querypieWorkflowsRequestForwardFlow.flow
Okta/QueryPie/querypieWorkflowsRequestForwardFlow.flow
Click on Workflow > Workflows console within the Okta Administrator Console. (Accessible only by Okta Super Administrators.)
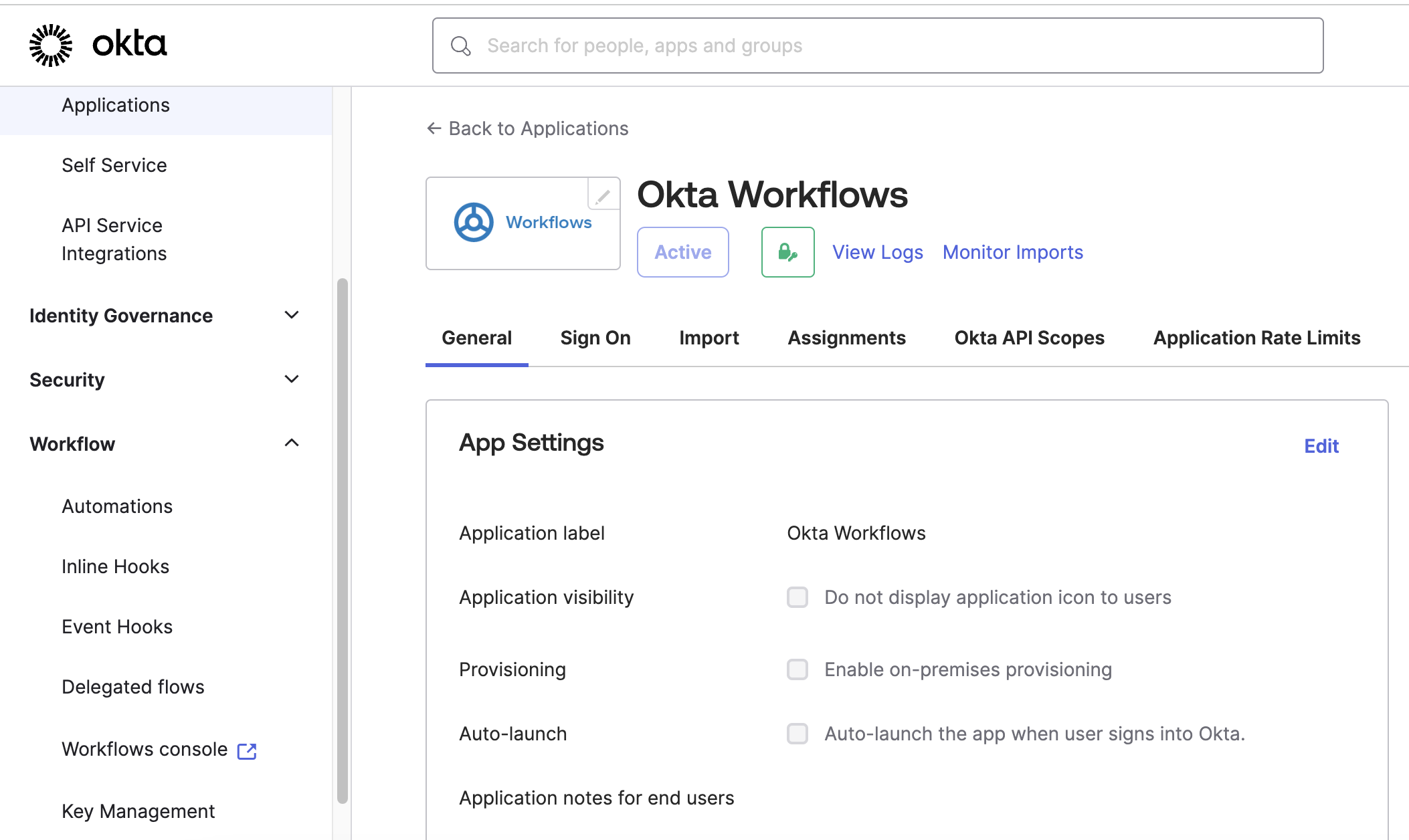
Workflow > Workflows console
Navigate to the Flows tab and within the Folder menu on the left side, click on the
⋮>↓ Importbutton.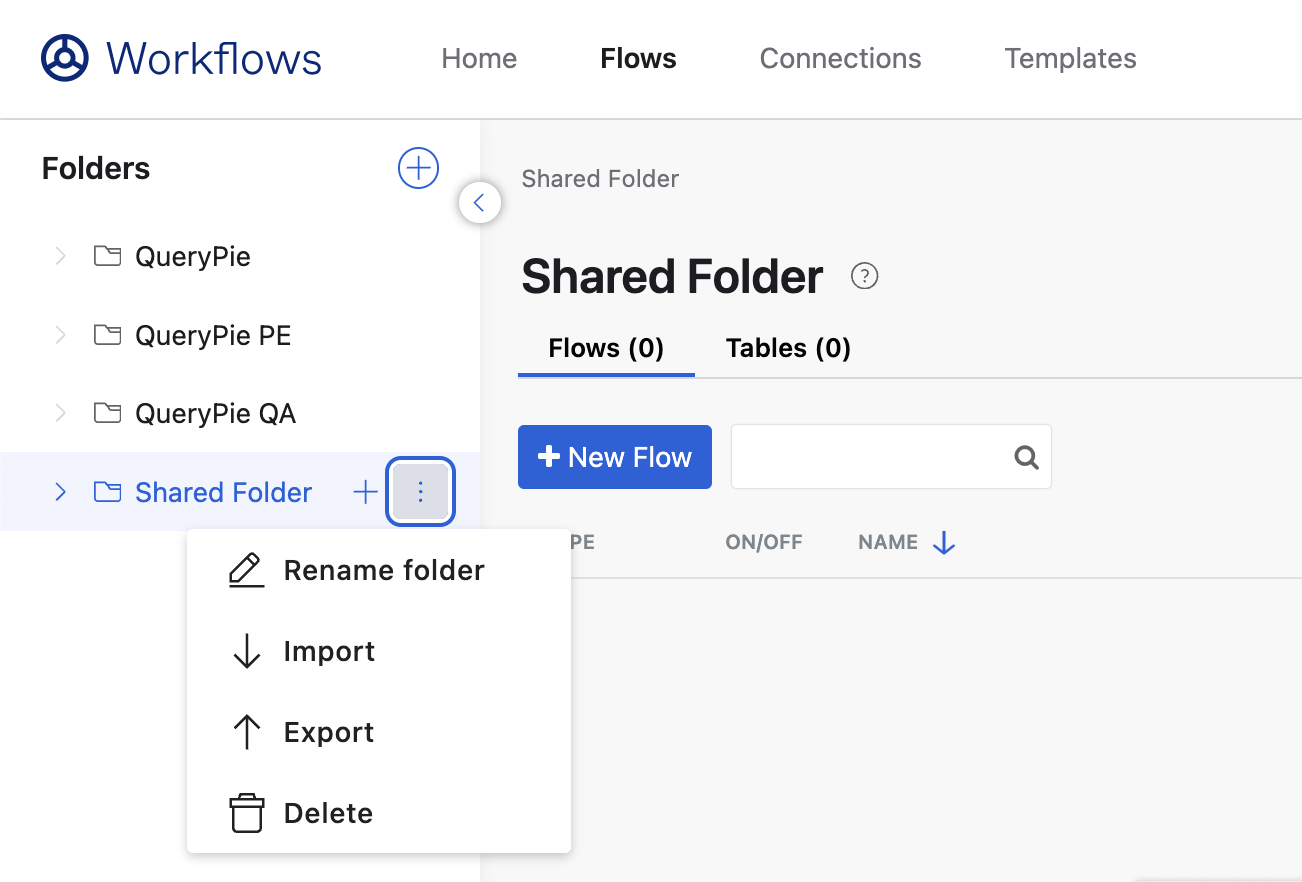
Flows > ⋮ > ↓ Import
Drag and drop the downloaded workflow file to create the flow immediately.
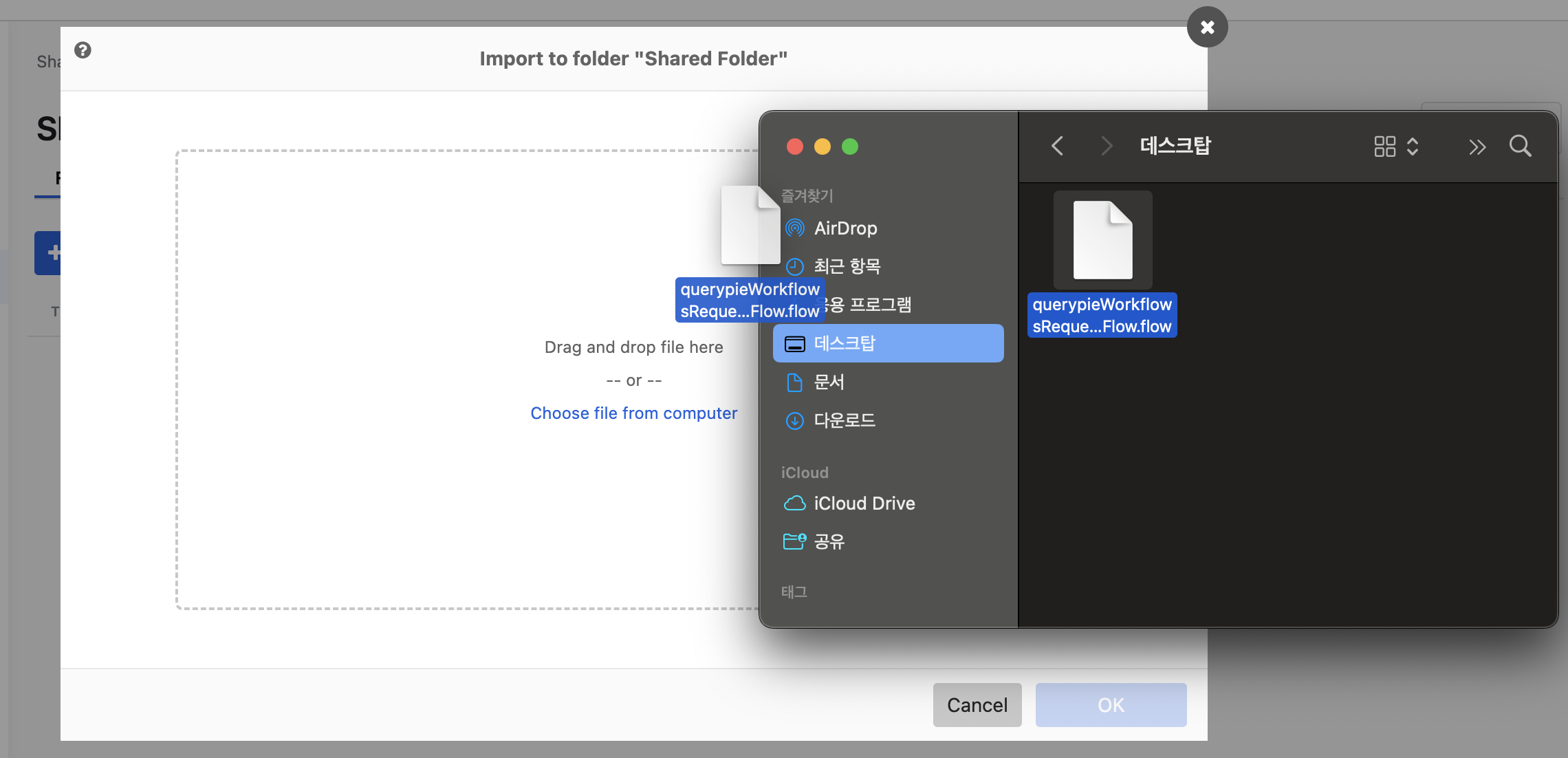
Import to folder “{{target folder}}“
Click on the created workflow to enter its details.
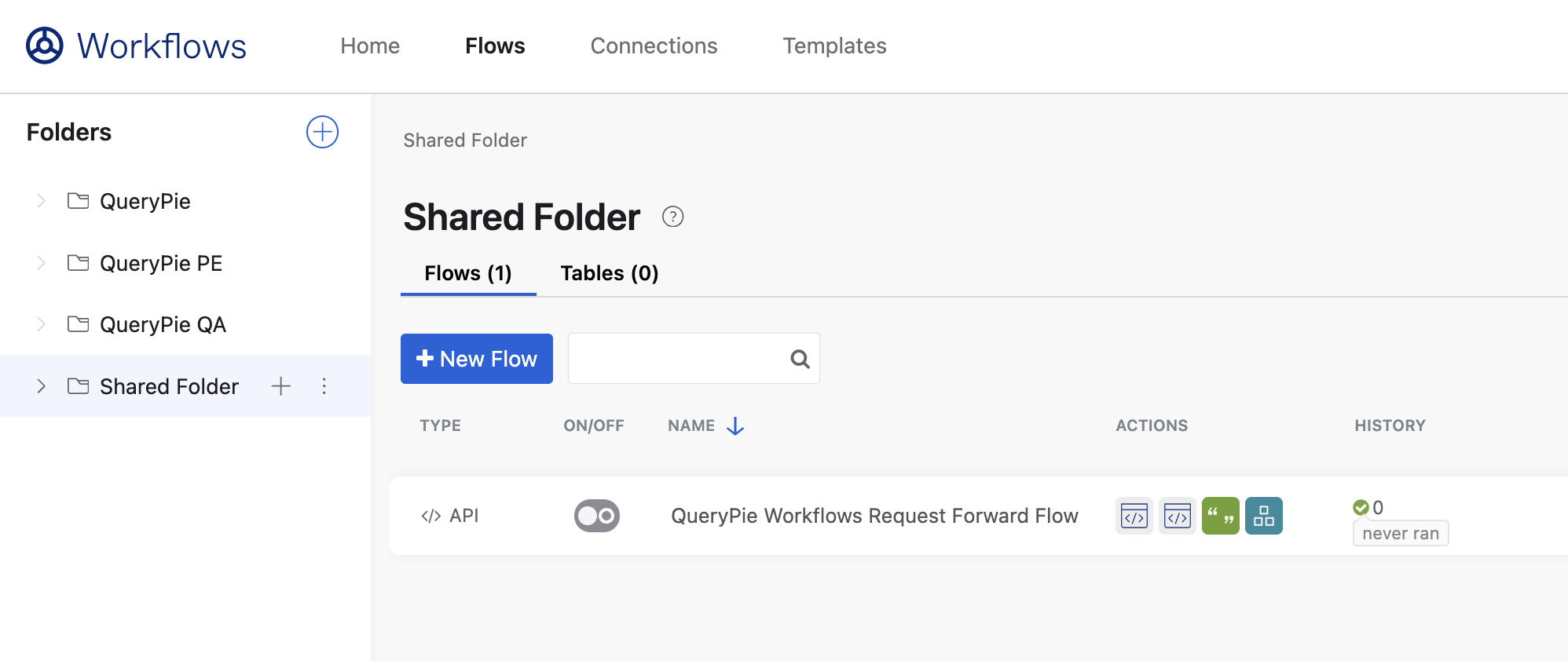
Flows > Folders > target folder
Within the
Composecard in the middle of the workflow template, update the URL string with the correct QueryPie domain address.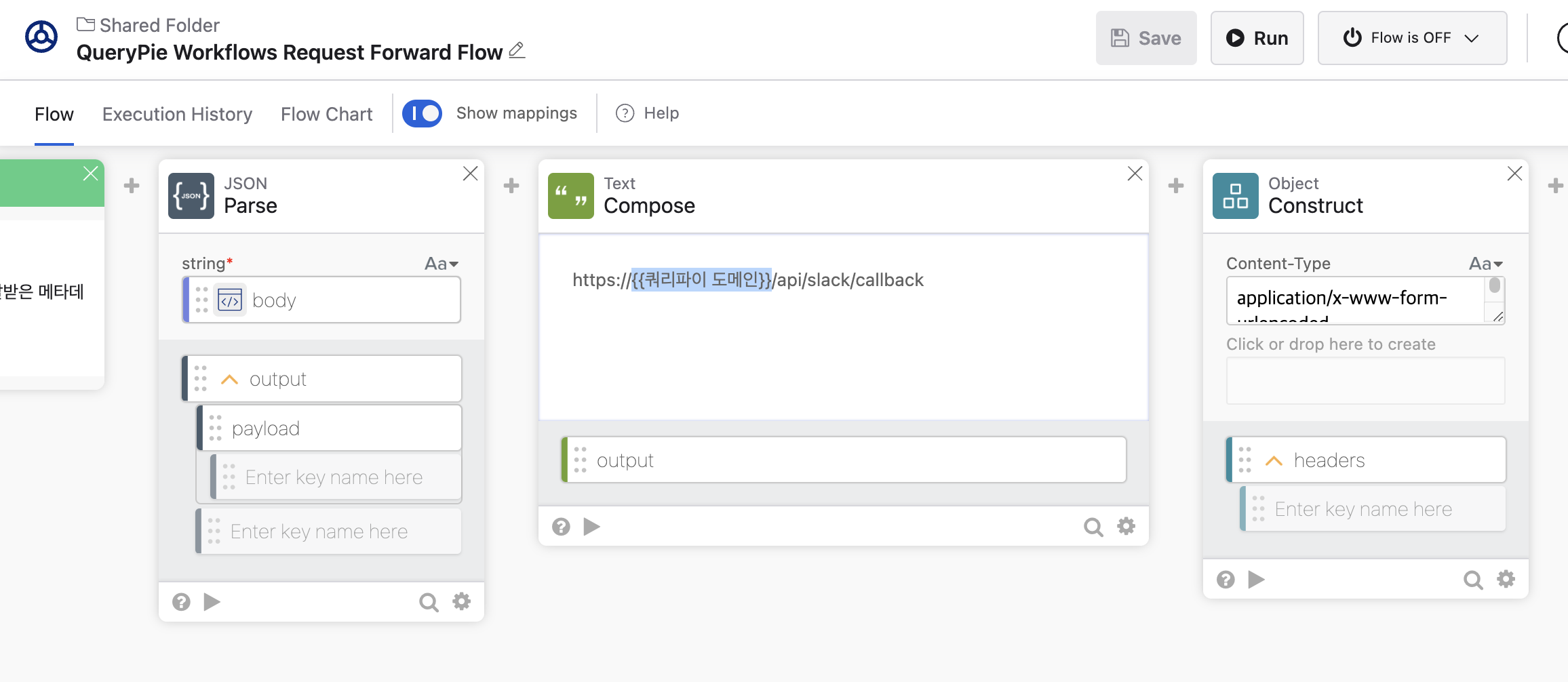
https://{{querypie domain}}/api/slack/callback
Click on the 'Unknown Connection' at the top of the
Postcard on the far right, then click on+New connection. Then on a separate browser tab, proceed to the QueryPie page.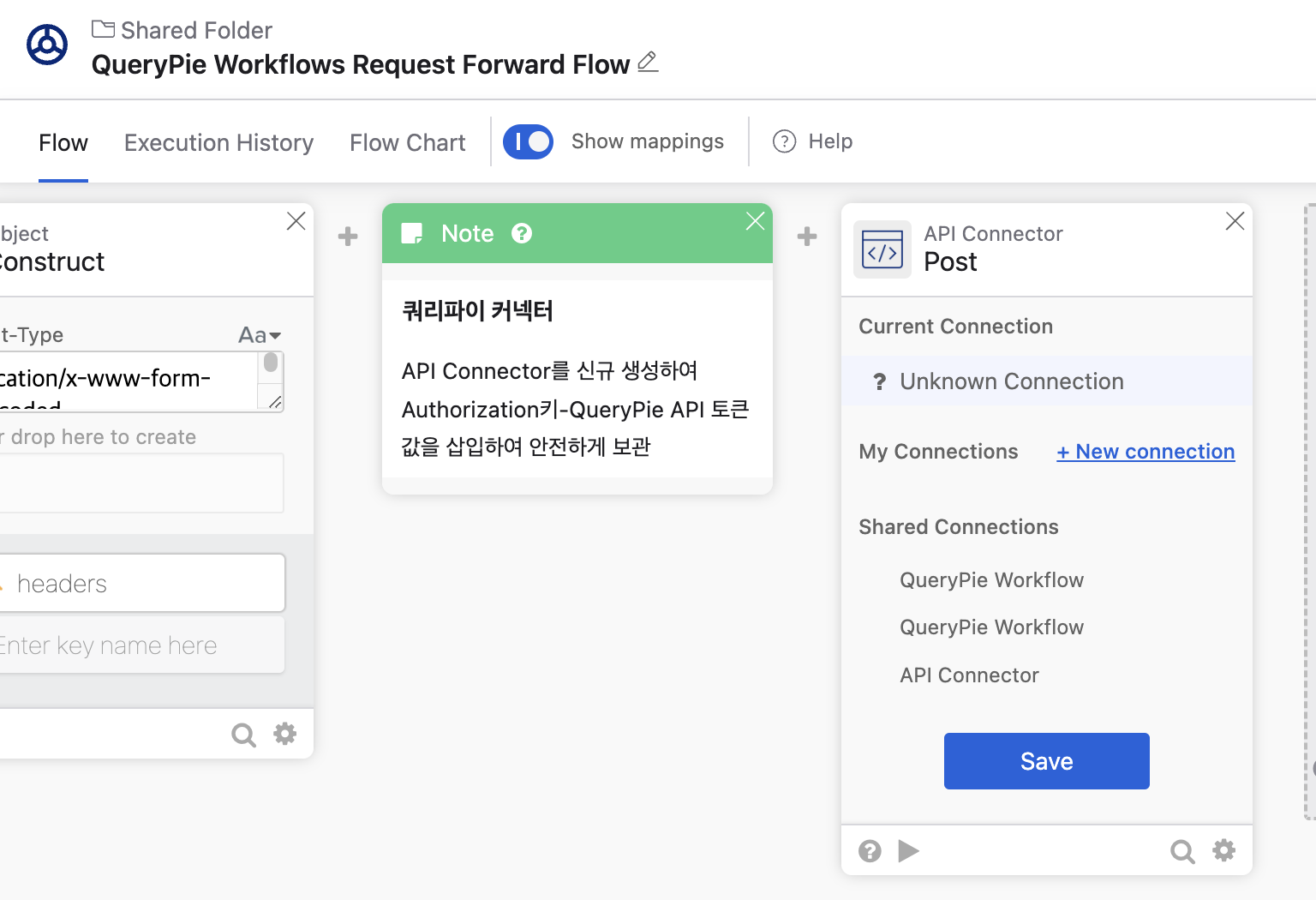
Post > Unknown Connection >
+ New connectionNavigate to QueryPie > Settings > General Settings > System > API Token, click on
+ Create API Tokento generate a token, then copy the token value. (Accessible by Owner and Approval Admin)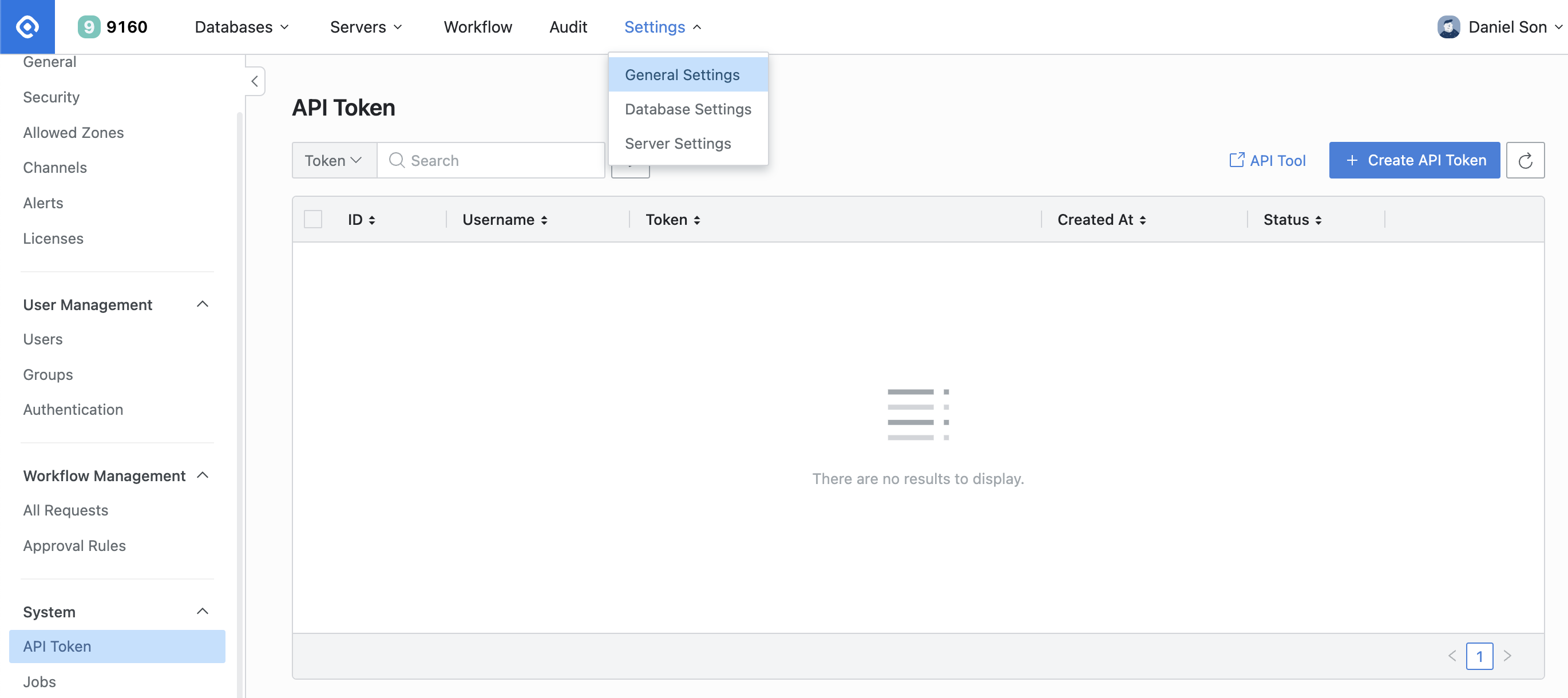
Settings > General Settings > System > API Token >
+ Create API TokenReturn to the Okta Workflows screen and fill in the following values, then click the
Createbutton.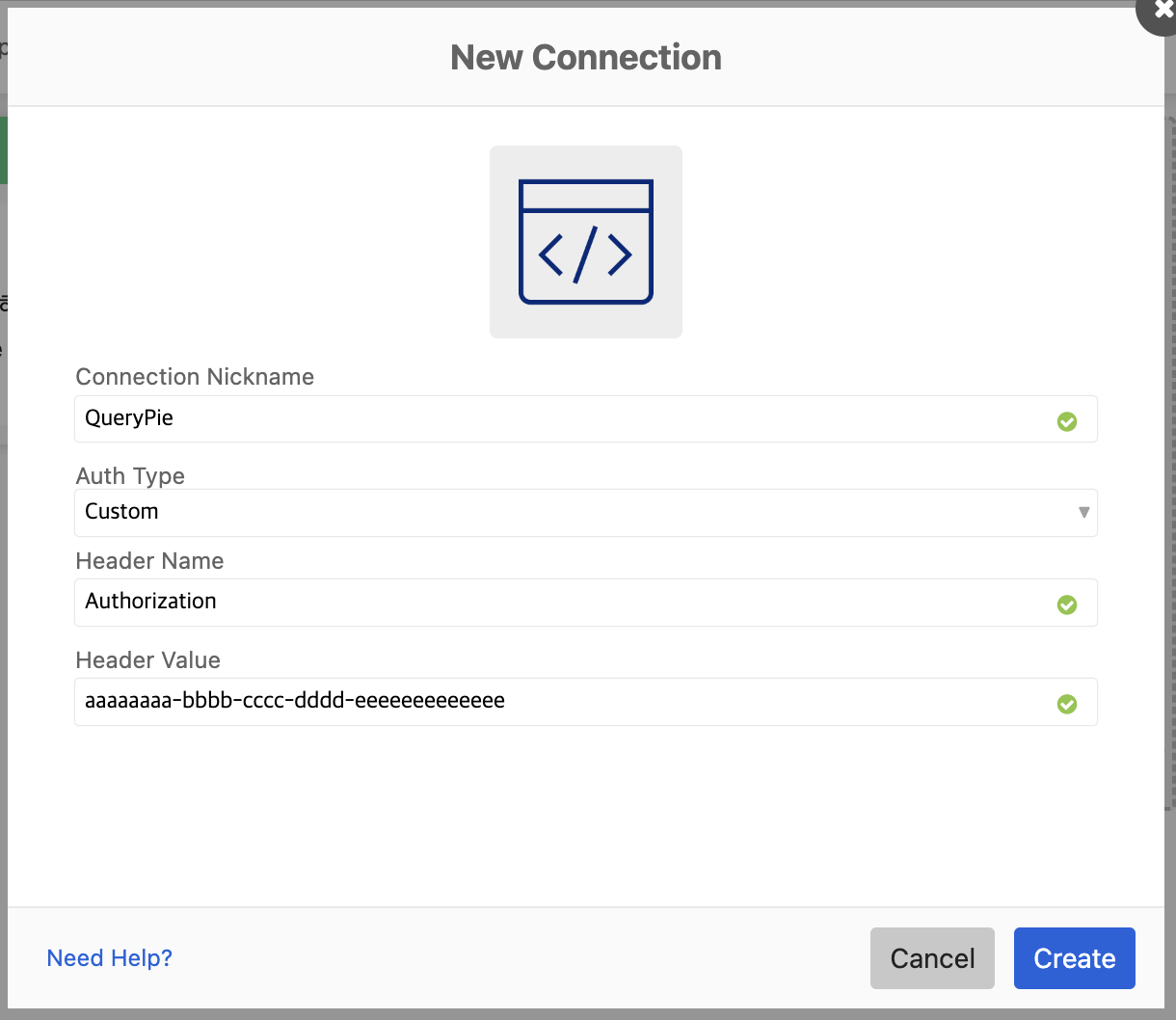
Post > Unknown Connection >
+ New connectionConnection Nickname : Enter an easily identifiable connector name (e.g., QueryPie).
Auth Type : Custom
Header Name : Authorization
Header Value : Paste the API Token value copied from QueryPie.
Click on the
⏻ Flow is OFFbutton in the top right corner of the flow, then activate theFlow is OFFtoggle at the bottom.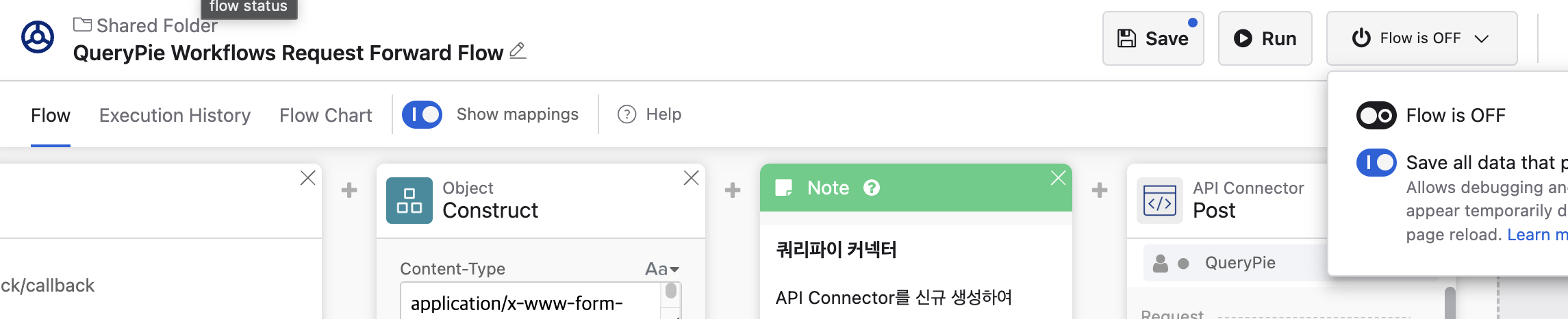
⏻ Flow is OFFClick the
Savebutton to save and activate the flow.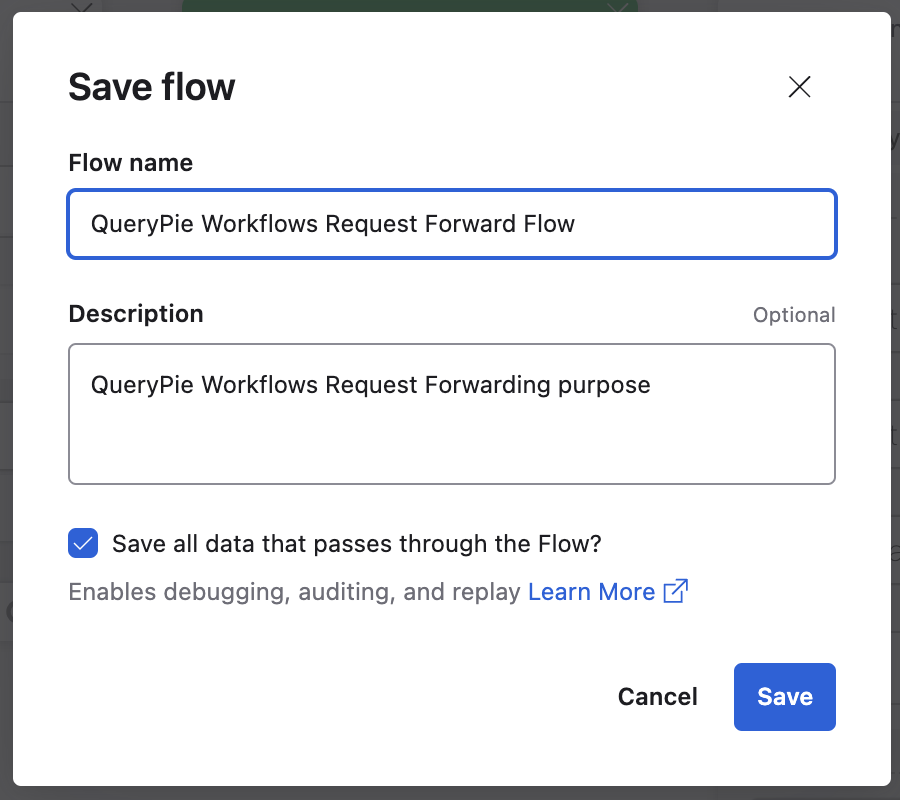
Click on the
</>button at the bottom of the API Endpoint card on the far left of the flow.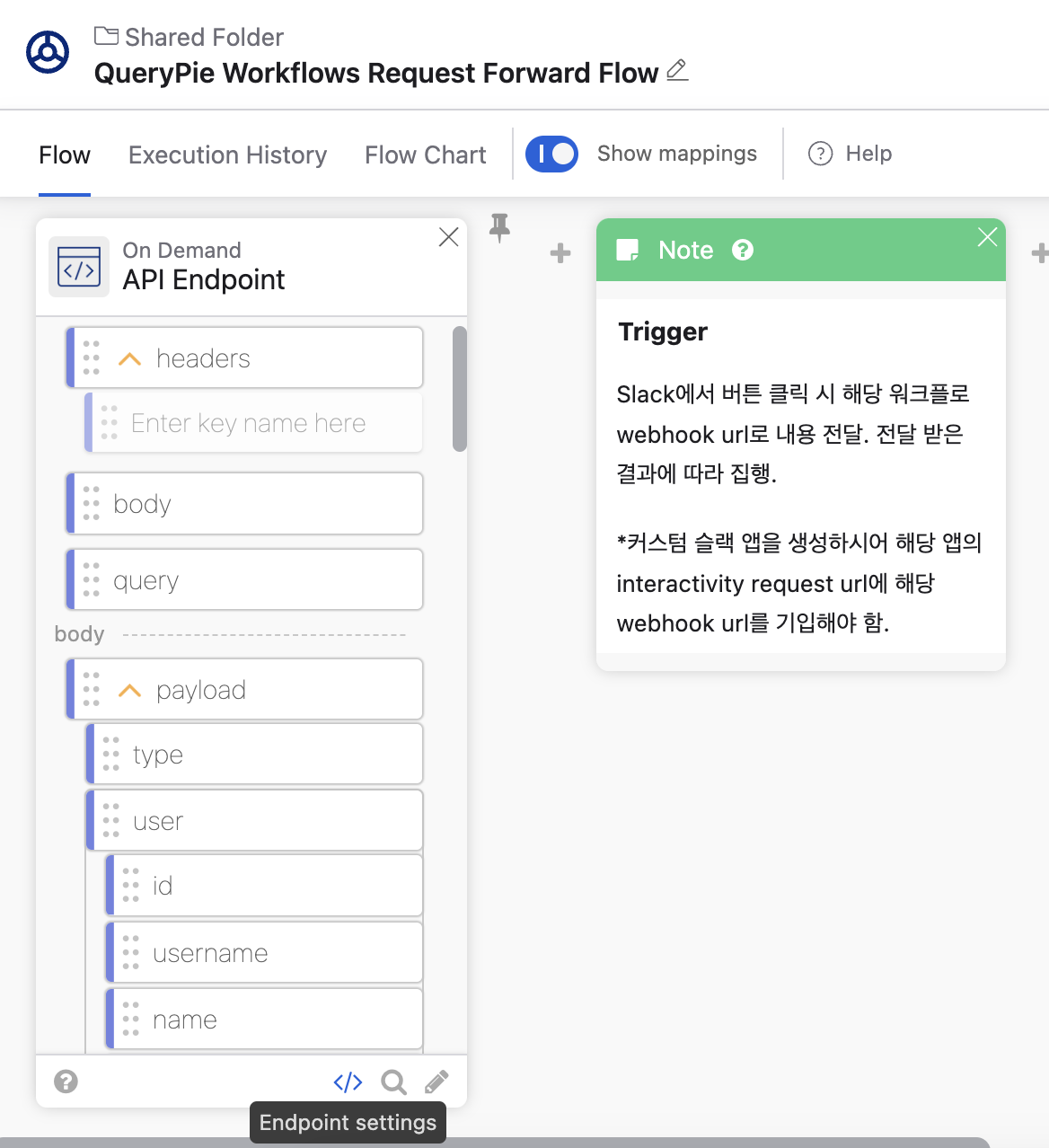
API Endpoint >
</>Press the copy button to copy the Invoke URL address to be reflected in the Slack App.
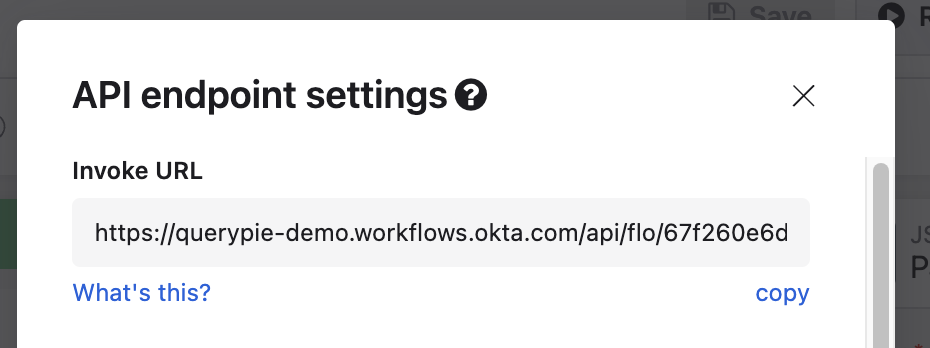
API endpoint settings > Invoke URL >
copy
Reconfiguring Slack App
Go to https://api.slack.com/apps and click on the QueryPie app that was previously created.
Navigate to Features > Interactivity & Shortcuts, then replace the Request URL address at the bottom of Interactivity with the Invoke URL address copied from the Okta workflow, previously located at
{QueryPie URL}/api/slack/callback. Click theSave Changesbutton at the bottom to save the configuration changes.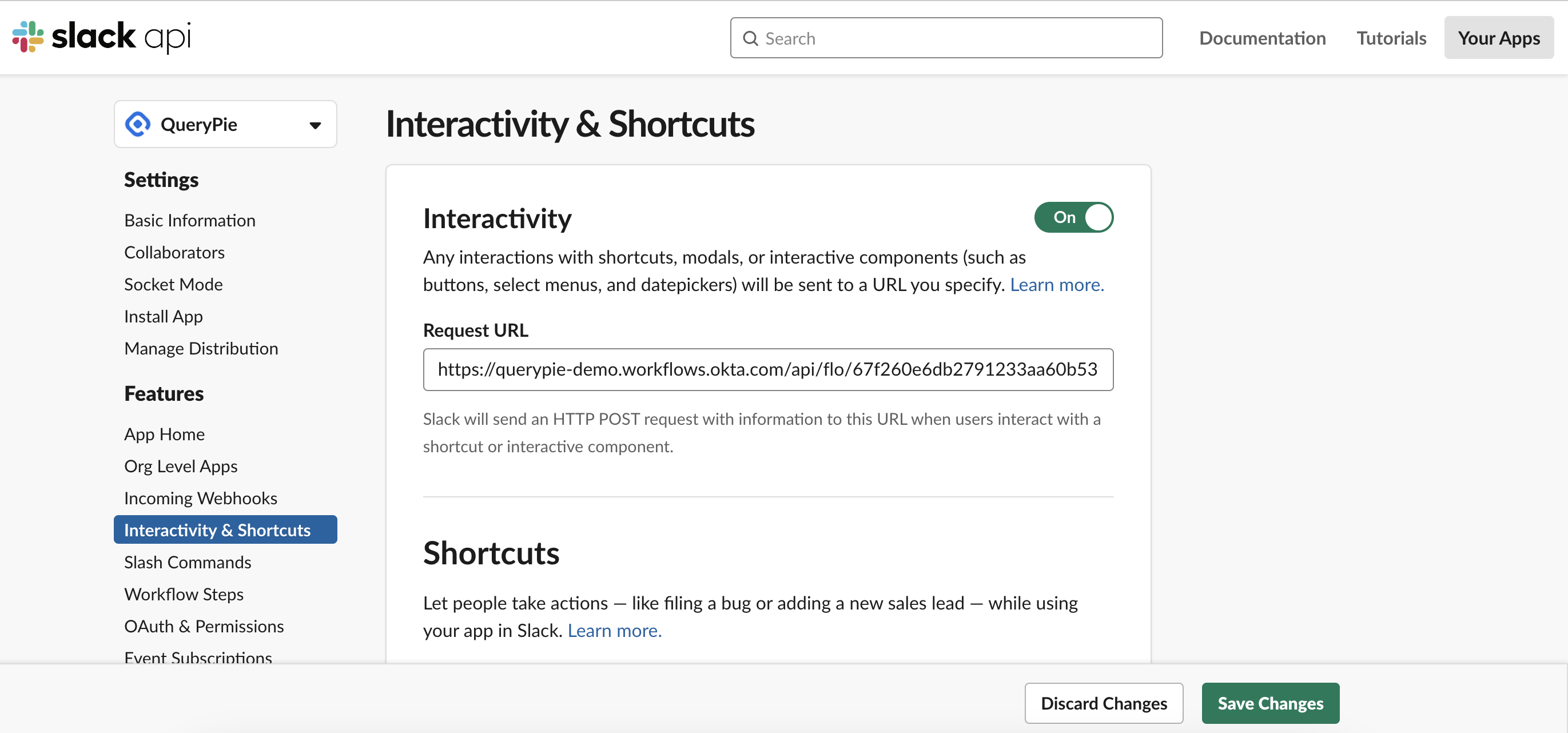
Afterward, when the approver in Slack attempts to approve/reject the workflow again, you should be able to confirm that the process reaches QueryPie through Okta workflow and is successfully processed, depending on the result.
%201.png)