QueryPie Overview
This article pertains to QueryPie Enterprise version 10.2.0.
QueryPie: Unified Access Control & Audit for Infrastructure
Due to the recent increase in cyber threats leading to frequent data breaches and growing regulations concerning privacy protection, more companies are considering adopting security solutions. QueryPie offers an optimized solution for both on-premises and various cloud environments, providing a comprehensive security solution that includes database, system, and container access control as well as auditing.
QueryPie is a powerful security solution that reduces time and costs while enhancing management stability through automation of security operations and easy integration with various platforms. It also supports user and administrator-friendly features that improve operational efficiency. Manage your scattered assets and permissions centrally with QueryPie.
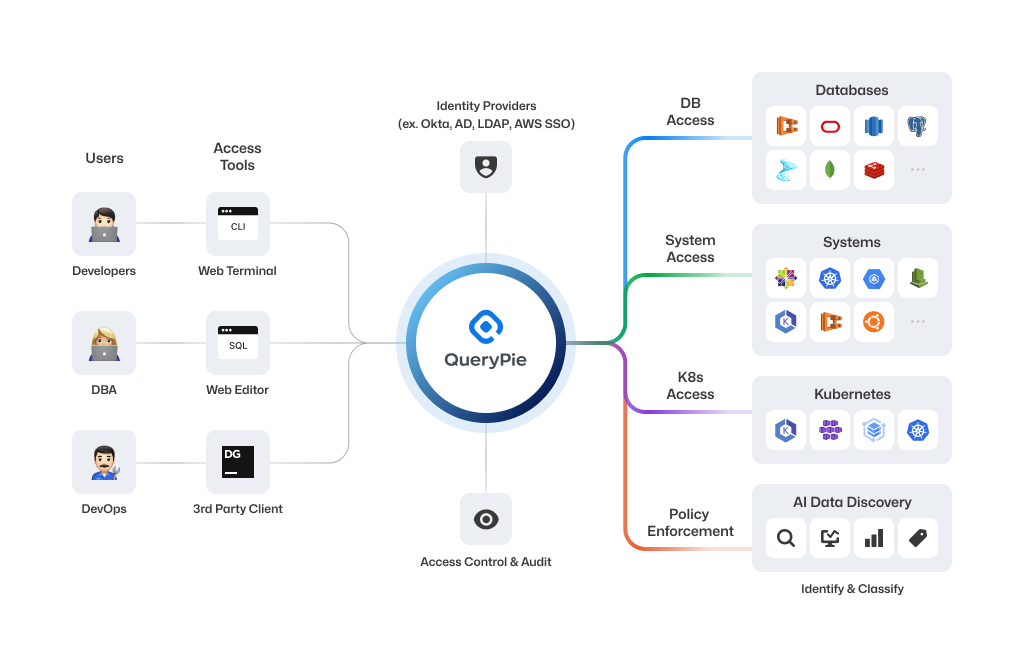
How QueryPie Works
Manual Guideline
QueryPie is constantly focused on finding ways to securely protect sensitive data within enterprises, even in cloud environments. Currently, QueryPie provides core features such as database, system, and Kubernetes access control and auditing capabilities, along with AI data discovery, which automatically identifies and classifies sensitive data based on database assets.
This document serves as a guide for security professionals to reliably implement access control and auditing functions within their companies using QueryPie. It covers everything from installation and initial system setup to resource registration and management, policy configuration, and audit log monitoring.
Key Features of QueryPie
Granular Access Control: Access permissions for users are detailed down to the level of networks, database tables and columns, and system protocols, ensuring users can access only the resources necessary for specific tasks.
Unified Interface: Manage multiple databases and system platforms through an intuitive single interface provided via a web browser. QueryPie supports integration with various cloud providers, simplifying resource management for access control.
Real-time Monitoring: Gain insights into user activity through real-time monitoring and auditing. Track abnormal access attempts, unnecessary query executions, data modification attempts, and potential security violations to maintain a robust security posture.
Workflow Integration: Streamline the process of requesting and approving access permissions with workflow features. Automate processes such as access requests and query execution requests to collaborate efficiently on tasks requiring approval and auditing.
Data Masking: Protect personal data by applying data masking policies. Even authenticated users may require additional verification or exceptions to access sensitive information.
Compliance Adherence: Comply with domestic and international compliance requirements. Quickly identify personal information regulated by compliance standards using predefined detection patterns, and extract audit logs in report form to facilitate certification and auditing responses.
%201.png)