Audit Log Export
Overview
QueryPie provides a feature to extract various audit logs and download them as CSV files. Even large files, such as those spanning long periods, can be extracted and downloaded stably. Once generated, log extraction files are available for download for 30 days. As of QueryPie v9.19.0, 18 types of logs are supported for extraction, including Query Audit and Workflow SQL Request.
With the addition of the Audit Log Export feature, the 'Excel File Download' button previously provided on each log screen has been discontinued starting from QueryPie v9.15.0.
Supported Log Types (as of QueryPie v9.19.0)
Query Audit [CSV]
Workflow SQL Request [CSV]
Workflow SQL Request for Query Details [CSV]
Workflow SQL Export Request [CSV]
Workflow DB Access Request [CSV]
Workflow Server Access Request [JSON]
User Access History [CSV]
Admin Role History [CSV]
DB Access History [CSV]
DB Account Lock History [CSV]
DB Access Control Logs [CSV]
Server Access History [JSON]
Command Audit [JSON]
Session Logs [JSON]
Server Access Control Logs [JSON]
Server Role History [JSON]
Activity Logs [JSON]
DML Snapshot [JSON]
Viewing the Audit Log Export List
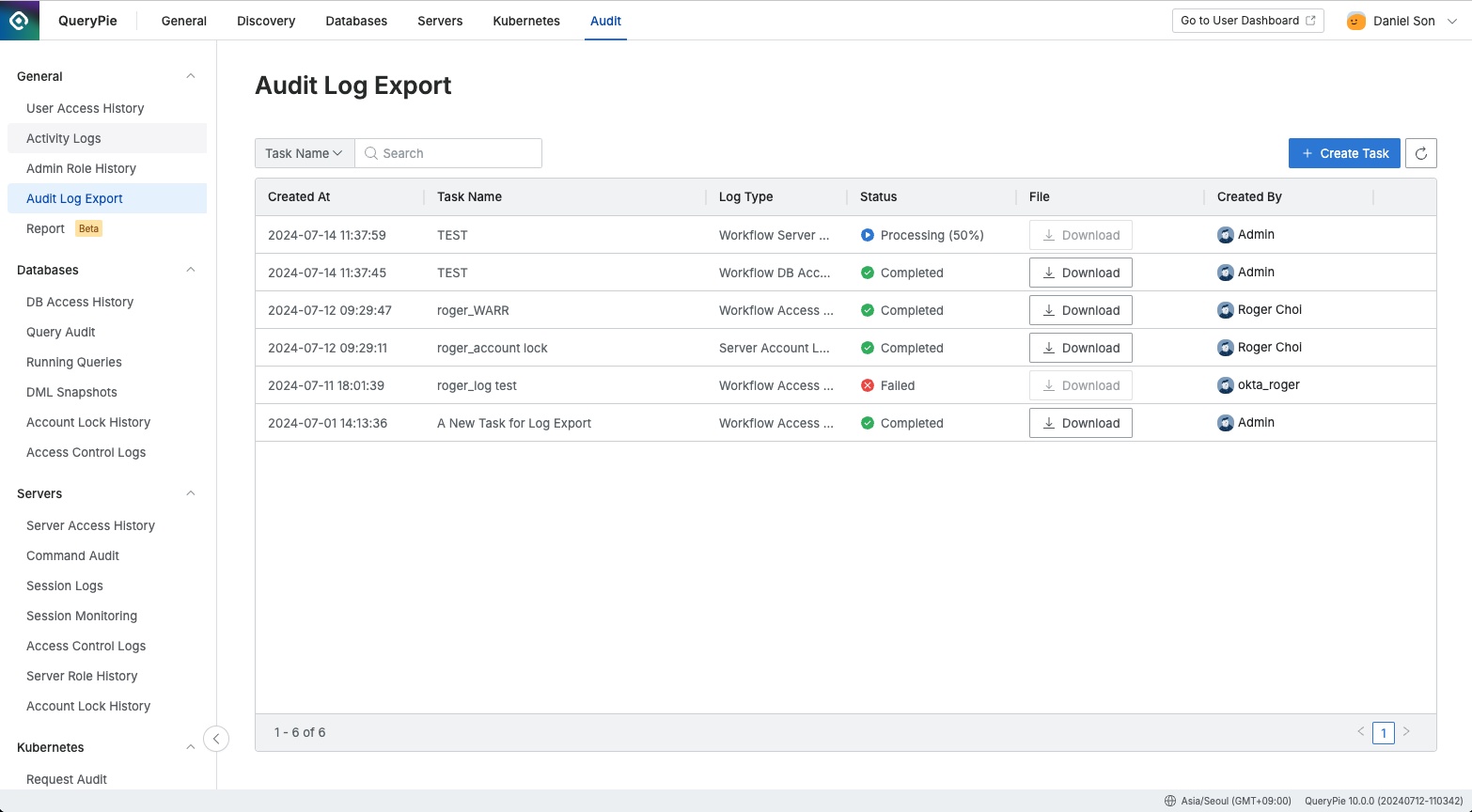
Administrator > Audit > General > Audit Log Export
Navigate to the Administrator > Audit > General > Audit Log Export menu.
View the list of generated audit log export tasks to date.
Check the status of tasks in the Status column:
Processing: The audit log extraction is in progress.
Completed: The audit log extraction is complete, and the file is available for download (files are available for 30 days after extraction).
Failed: The audit log extraction has failed. Please contact QueryPie Customer Support.
Creating a Log Extraction Task
Audit log extraction and download proceed through the following steps: (1) Access the relevant menu. → (2) Create a log extraction task. → (3) Wait for the extraction to complete. → (4) Download the file upon completion.
To start the audit log extraction, navigate to the Audit > General > Audit Log Export menu. Then, click the Create Task button at the top right. The following screen will appear:
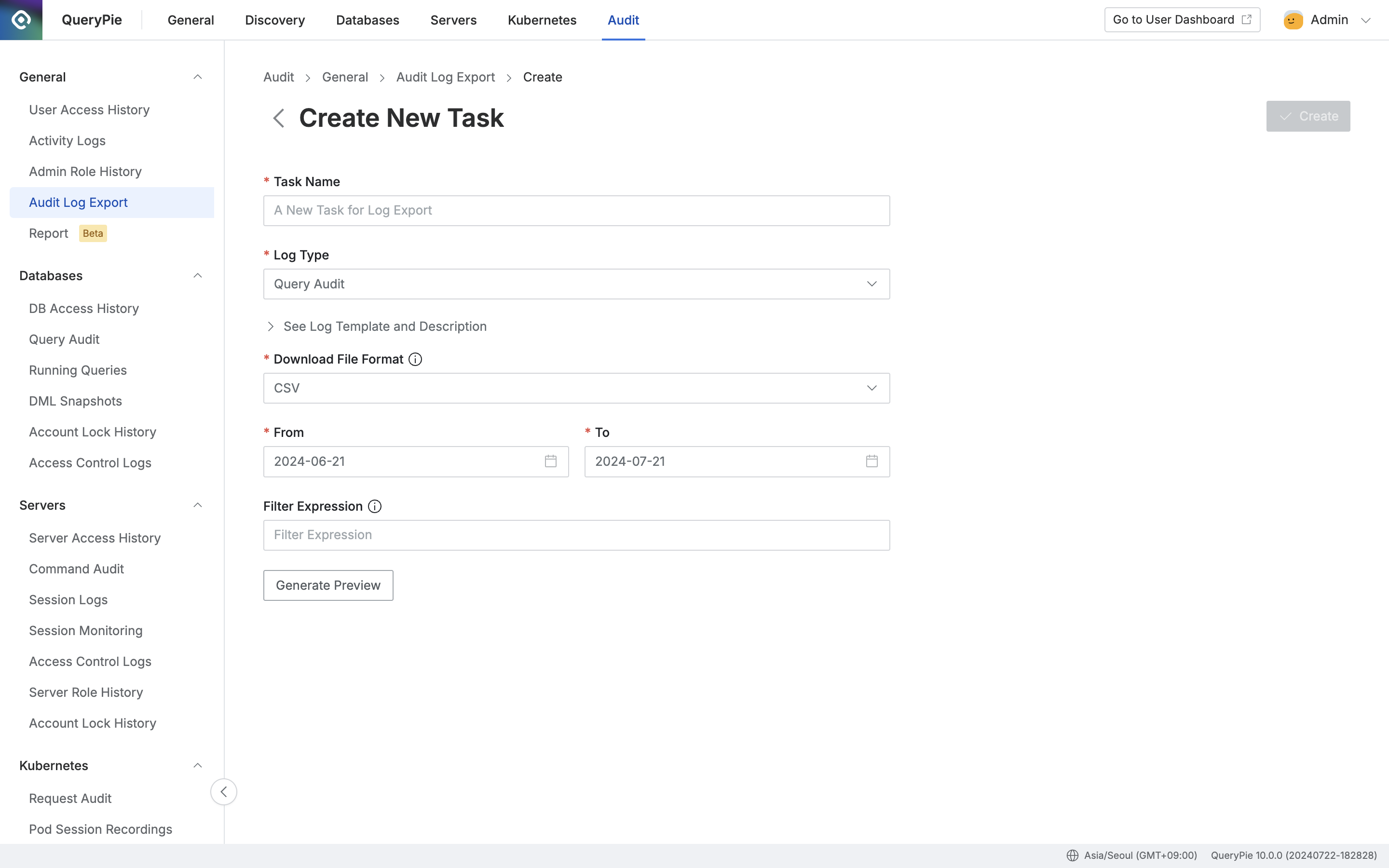
Administrator > Audit > General > Audit Log Export > Create New Task
Task Name: Enter the name of the log extraction task.
Log Type: Select the type of log to extract
Select the type of log to extract (e.g., Query Audit).
Click See Log Template and Description for detailed information about each log's keys and values.
Download File Format: Specify the output file format (as of v9.17.0, each log type has a single available format).
From: Specify the start date for the extraction period.
To: Specify the end date for the extraction period.
Filter Expression: Specify filter expressions.
See Filter Expressions below for examples.
Generate Preview:
This step is required.
Review the preview to proceed to the next step.
Create: Generate the log extraction task.
Filter expressions
(1) To utilize filter expressions, refer to 'See Log Template and Description' for the log-specific keys, their types, and included values.
(2) Filter expressions are categorized based on data type:
Number Type
Supported expressions :
>,<,<=,>=,==,!=e.g.
x > `10`,x == `10`
String Type
Supported expressions :
==(equals),!=(not equals),containse.g.
x == 'abc',x != 'abc',contains(x, 'ab')
Boolean Type
Supported expressions :
==(equals),!=(not equals),&&(and),||(or)e.g.
x == `true`,x && y,(x > `0`) && (y == `0`)
Array Type
Example:
x[? @ == 'value'],list[? @ > `10`]
(3) Use the following characters for multiple conditions :
AND Condition :
&&OR Condition :
||Compound condition :
( )
(4) Examples :
Extract only query execution logs during Query Audit :
actionType == 'SQL_EXECUTION'
Extract only query execution logs made to WebEditor during Query Audit :
actionType == 'SQL_EXECUTION' && executedFrom == 'WEB_EDITOR'
Extract logs for two specific databases from DB Access History :
connectionName == 'database1' || connectionName == 'database2'
Extract DB Access History for two specific databases with Replication Type as SINGLE :
(connectionName == 'database1' || connectionName == 'database2') && replicationType == 'SINGLE'
Criteria for specifying the Privilege Type of export files in Query Audit
The 'Privilege Type' column in the export file indicates the privileges required at runtime. It functions as follows:
Commands executed with default privileges (SET, SHOW, etc.) have a blank value in the corresponding column.
Logs executed with privileges such as INSERT specify the SQL Type.
For Redis, the command name is specified.
Downloading the Completed Extraction File
For short-term queries without additional filters, log extraction completes in a few minutes. For long-term logs or complex filtering conditions, extraction may take longer.
To download the completed log file:
From the list page: Click the
Downloadbutton.From the details page: Click a task to enter the details page, then click the
Downloadbutton at the top right.
Encrypt Log File
The downloadable file is a '*.zip' file that compresses the '*.csv' file.
To set a password for this compressed file, ensure that the "Export a file with Encryption" option is set to "Required" in the 'General Settings > Company Management > Security' menu.
Log File Retention Policy
Extracted log files are retained for 30 days from the task creation date. Within this period, you can download the files as many times as needed. After 30 days, the files expire. If you need expired log files, create a new log extraction task.
%201.png)