Kubernetes Policy UI Code Helpers
Overview
You can manage access policies for Kubernetes clusters within your organization. Kubernetes policies operate as Policy as Code (PaC) and are based on YAML format.
On the right side, there are Policy UI Code Helpers that provide modals for users to easily insert content into the code editor.
Using the UI Code Helper
On the right side of the code editor screen, a modal is available to assist with code entry for each field. This modal aids in code editing, and any content inserted via the modal can be removed directly from the code editor.
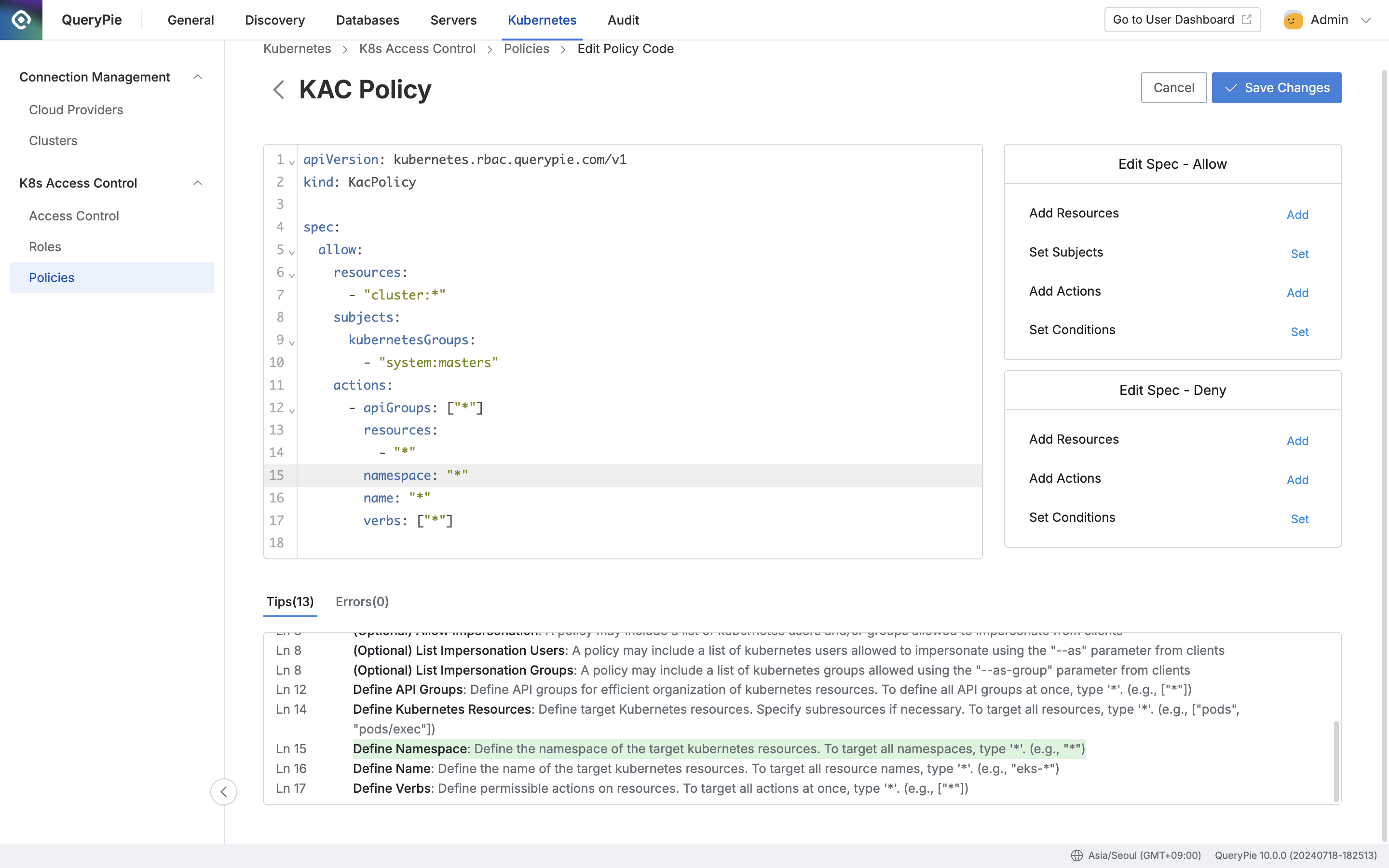
Add Resources
It operates in the same manner in both the Spec: Allow and Spec: Deny sections.
You can search for resources by cluster name.
To insert a resource into the code, check the checkbox next to the desired resource and click the
Addbutton.
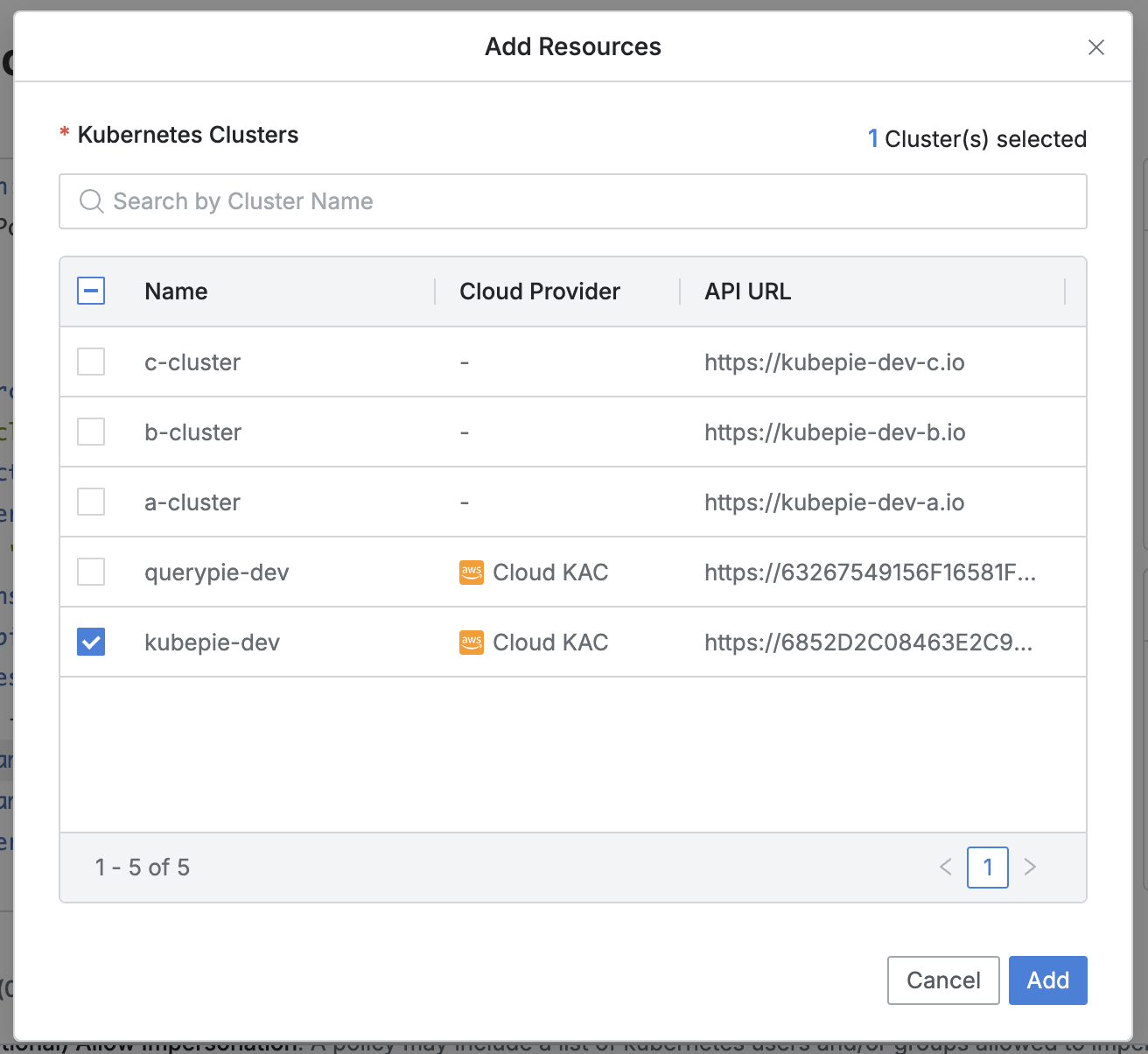
Set Subjects
It operates only in the Spec: Allow section.
Kubernetes Groups : (Required) Use this field to specify the Kubernetes groups that the KubePie Proxy will impersonate to perform API calls.
Permitted Impersonation : (Optional) Use this field to list the Kubernetes users/groups that can be impersonated when a user attempts impersonation through the client using the
--asand--as-groupparameters.Allowed Kubernetes Users: ist the Kubernetes users that are permitted for impersonation using the
--asparameter.Allowed Kubernetes Users: List the Kubernetes groups that are permitted for impersonation using the
--as-groupparameter.Multiple entries can be registered using a comma (
,) as a separator.
The modal displays existing information from the editor. Clicking the
Setbutton will overwrite the editor's content with the changes.
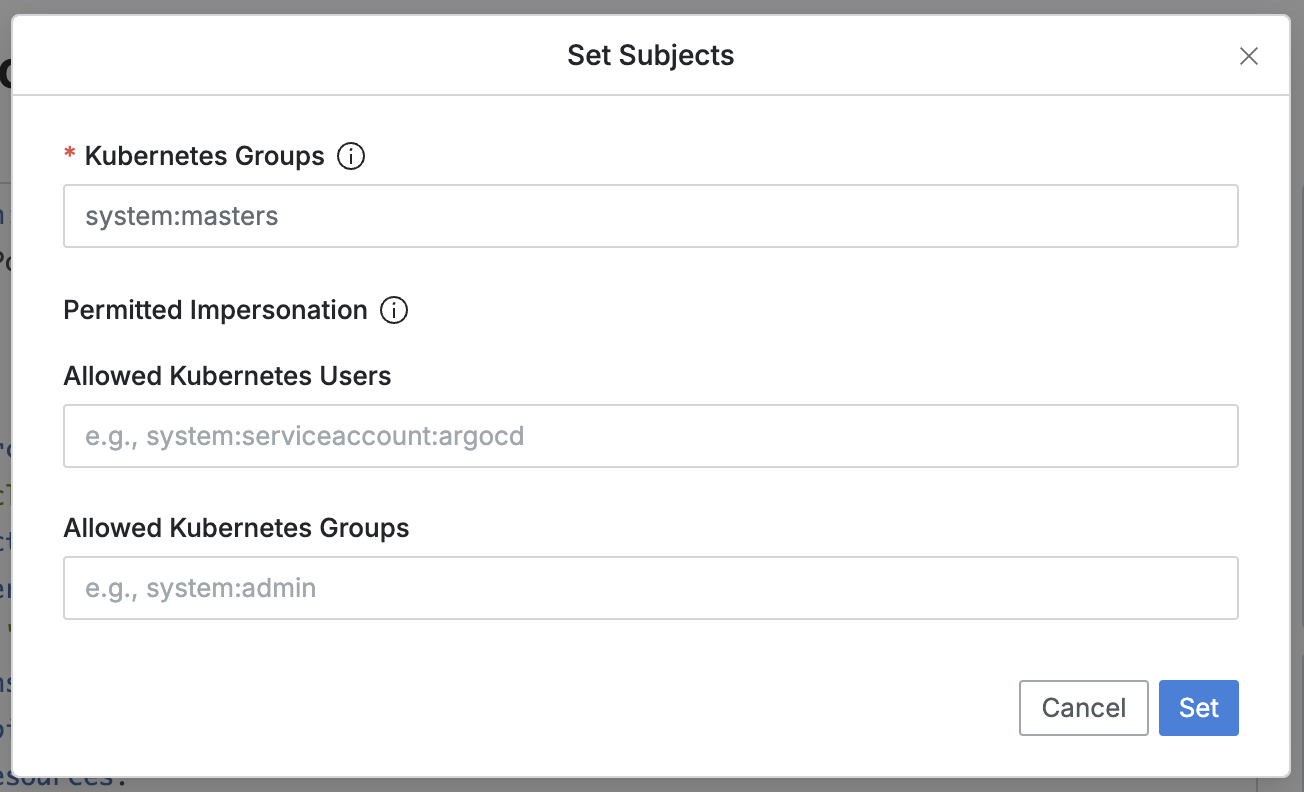
Add Actions
It operates in the same manner in both the Spec: Allow and Spec: Deny sections.
API Groups: Defaults to "*", but can be modified by the administrator. Multiple entries can be added using a comma (
,).Resources: Specify the Kubernetes resources.
Defaults to "*", but can be modified by the administrator. Multiple entries can be added.
Commonly used resources include:
pods,pods/exec,pods/log,pods/portforward,services,ingresses,deployments,replicasets,statefulsets,daemonsets,configmaps,secrets,namespaces,nodes,persistentvolumes,persistentvolumeclaims,jobs,cronjobs,serviceaccounts,endpoints,roles,rolebindings,clusterroles,clusterrolebindings
For resources not listed above, you can type directly to specify custom resources.
Once specified, items are displayed as blocks and can be removed by clicking the "X".
Namespace: Specify the namespace to limit the scope of Kubernetes resources.
Defaults to "*", but can be modified by the administrator. Supports wildcards and regular expressions.
For resources outside the namespace scope, the value in this field will not affect them.
non-namespaced resources: e.g.,
persistentvolumes,persistentvolumeclaims,serviceaccounts,customresourcedefinitions,endpoints,nodes,clusterroles,clusterrolebindings
Name: Specify the name of the Kubernetes resource to target.
Defaults to "*", but can be modified by the administrator. Supports wildcards and regular expressions.
Verbs: Specify multiple Kubernetes API methods.
Defaults to "*". Once specified, items are displayed as blocks and can be removed by clicking the "X".
Commonly used verbs include:
get,list,watch,create,update,patch,delete,deletecollection
You can type directly to specify other verbs for custom resources.
Click the
Addbutton to define an action set within the actions list.This functions as an append operation in the code, allowing new actions to be added without resetting previously added actions.
Set Conditions
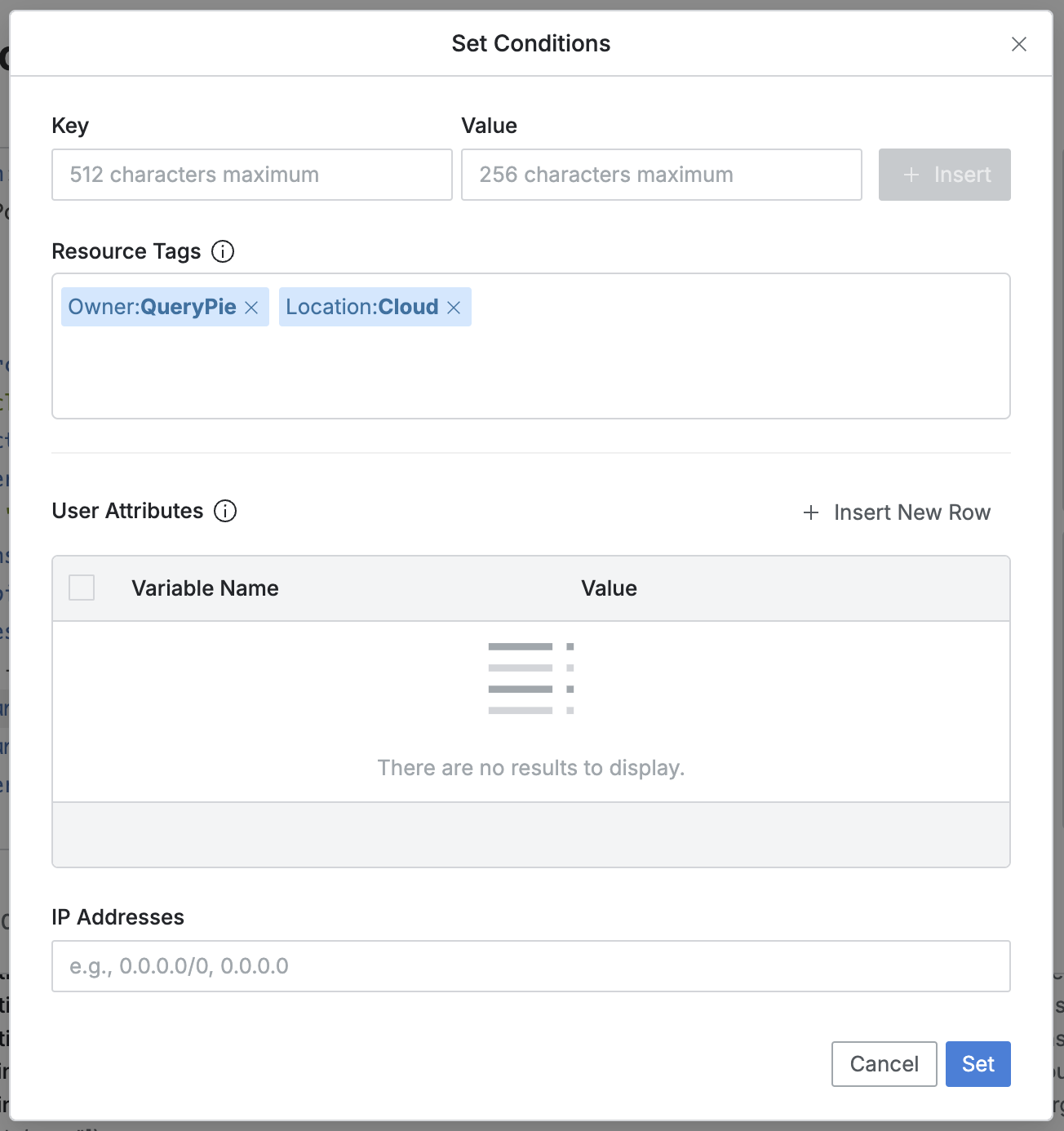
All of the following items are optional.
The modal displays existing information from the editor, and clicking the
Setbutton will overwrite the editor's content with the changes.Resource Tags (Optional)
You can restrict the scope of target Kubernetes clusters based on their attached tags.
Each row operates as an AND condition; values within a row operate as OR conditions separated by commas (
,).Click the
Insertbutton to create a new row.Once specified, tags are displayed as blocks and can be removed by clicking the "X".
Fields:
Key : Tag key (does not support regex or glob)
Value : Tag value (supports regex, glob, and multiple inputs)
User Attributes (Optional)
You can limit the scope of target users based on their user attributes.
Users must match all specified attribute values to use the policy.
Each row operates as an AND condition; values within a row operate as OR conditions separated by commas (
,).The Variable Name field suggests currently supported attributes, including:
loginId,firstName,lastName,middleName,honorificPrefix,honorificSuffix,email,title,displayName,nickName,profileUrl,secondEmail,mobilePhone,primaryPhone,streetAddress,city,state,zipCode,countryCode,postalAddress,preferredLanguage,locale,timezone,userType,employeeNumber,costCenter,organization,division,department,managerId,manager,endpoints,staticIp,macAddress
IP Addresses (Optional)
The administrator can specify IP ranges that are allowed or denied access to the resource.
Supports both single IPs and CIDR notation, separated by commas (
,).
%201.png)