Access DB & Server via Proxy
Overview
QueryPie supports proxy connections, allowing users to access databases and systems. Besides providing access through its own web editors and terminals, QueryPie also supports access via proxy credentials generated by the platform. By requiring access through a proxy server, you can control all access to your resources, even when accessed via external clients. Additionally, you can set it up to block any access that does not go through the proxy.
Introduction to QueryPie Proxy
Enhanced security: The proxy feature serves as a secure intermediary between users and resources, adding an extra layer of security against unauthorized access and potential security breaches.
Centralized auditing: Proxies record and audit resource access and actions by all users. This centralized auditing capability is essential for compliance, ensuring accountability, and transparency.
Real-time monitoring: Real-time monitoring of user behavior and activity enables you to identify anomalies and potential threats, allowing for effective risk mitigation.
Block unauthorized remote access: Proxies facilitate secure remote access to databases and systems, eliminating the need for users to directly access sensitive resources. This helps minimizing the exposure of critical infrastructure to external threats.
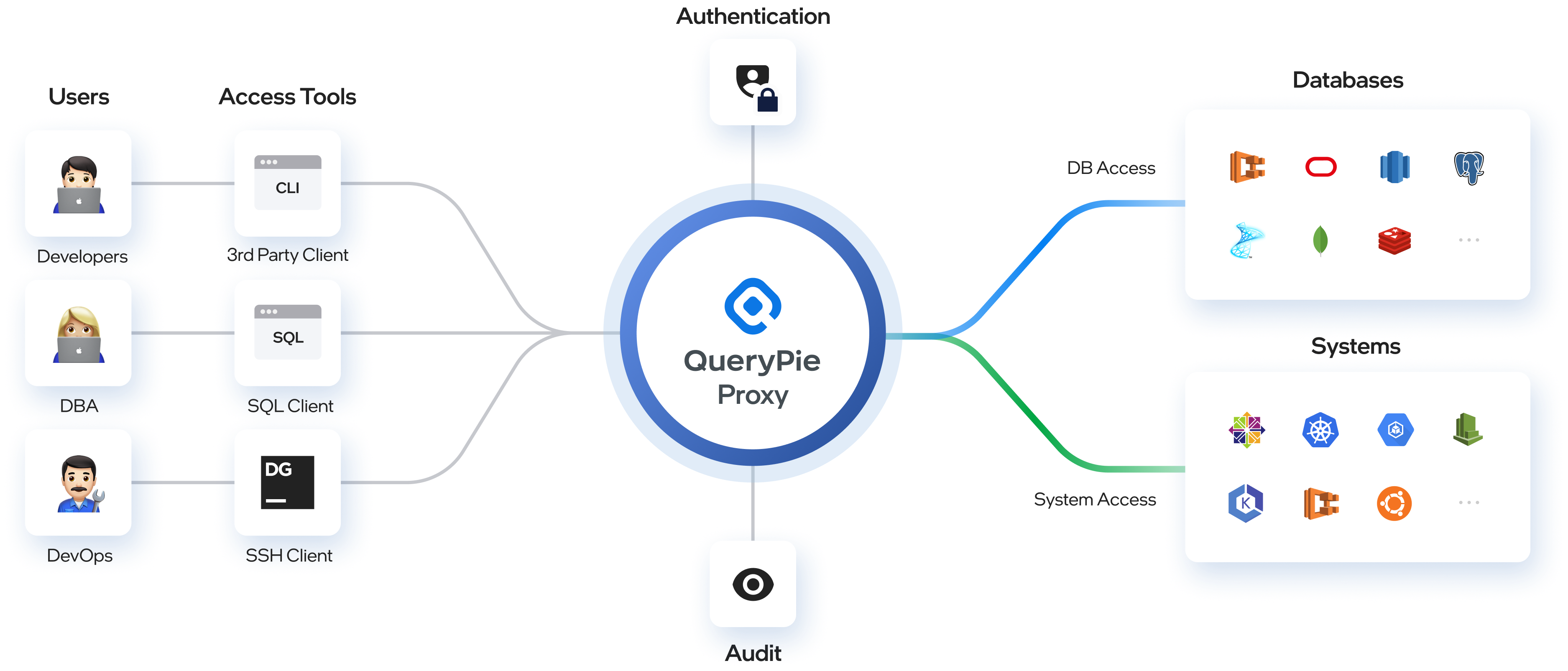
How the QueryPie Proxy Works
.png?inst-v=70c405b3-5d8d-4ec6-9c81-bbcc5b3d4797)
Proxy settings: Administrators can configure proxy usage for each resource individually within QueryPie's interface.
User authentication: Users securely connect with QueryPie using their authentication credentials. Before connecting to the proxy, credentials are verified to ensure that the user is authorized.
Access control: The proxy feature enforces predefined access permissions, ensuring that users can only connect to databases and systems they have authorization to access.
Privacy: Proxy connections enforce data access and masking policies, safeguarding sensitive data from unauthorized users.
QueryPie's proxy feature significantly enhances database access security, offering robust protection to safeguard data, enforce access controls, and mitigate vulnerabilities. By restricting user resource access and enforcing stringent security policies, proxies play a crucial role in helping organizations maintain privacy and compliance standards.
The following guide will help you enable and manage your proxy settings.
Enable System Proxy (Coming Soon)
Related Topics
%201.png)