Server Alert Policies
Overview
It offers alerts regarding system access, detecting instances of server access behavior or the execution of prohibited commands, and delivering real-time alerts. By pre-configuring notification targets (Connections), trigger conditions, and other parameters for each notification type, users can promptly receive notifications for all access behaviors and violations. These alerts can be received through designated channels like Slack, webhooks, and others.
Before subscribing to notifications, we recommend registering the channels you wish to receive notifications in the menu below
Settings > General Settings > Company Management > Channels
QueryPie SAC offers the following six notification types:
Server Connection Attempt: Detects server access behavior and sends notifications regarding whether the connection succeeds or fails.
Restrict Command: Sends a notification when a predefined restrict command is executed from the server or server group.
Specific Command: Sends a notification when a defined specific command is executed.
File Transfer (SFTP): Sends a notification when file transfer behavior is detected via SFTP.
New Request: Sends an alert when a new approval request is registered.
Unusual Login Attempt: Sends a notification when a user login attempt is detected based on the IP band.
Set Up Alert Policies
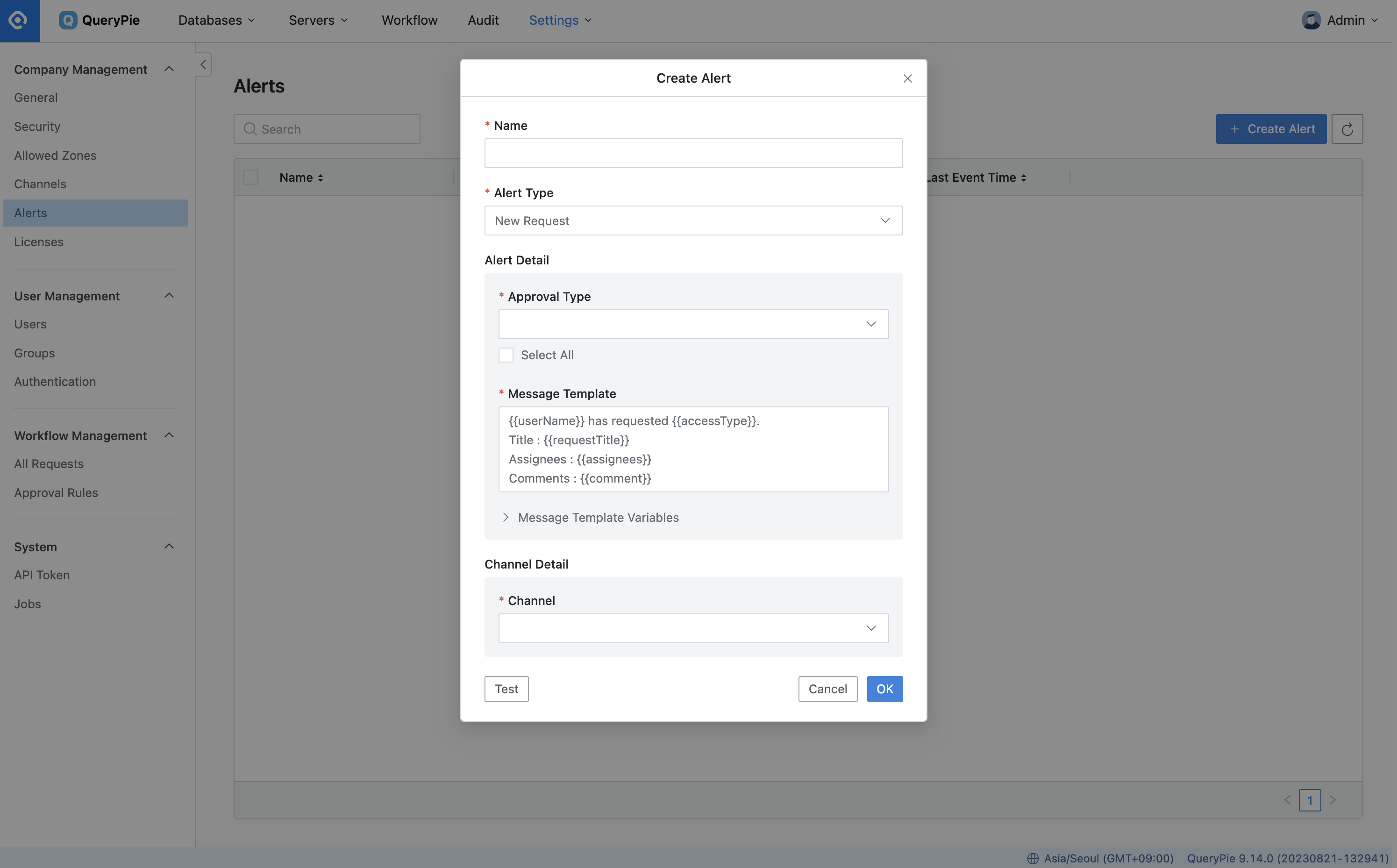
General Settings > Company Management > Alerts > Create Alert
Navigate to General Settings > Company Management > Alerts menu.
Click the
Create Alertbutton in the upper right corner.Enter the following information to create an alert:
Name : Provide a name to identify the alert on the screen.
Alert Type : Select the type of alert you wish to create.
Alert Detail : Specify the conditions for the alert to occur. Different trigger conditions can be set for each type.
Alert Trigger Condition : This option is only applicable for Server Connection Attempt and File Transfer (SFTP) types. It enables you to set the conditions for the alert to activate.
Connection : Select a server or server group to receive notifications. Notifications will be dispatched when the specified triggers occur on the selected server or server group. Multiple servers can be selected. If both a specific server and the server group it belongs to are chosen, duplicates will be removed from the notification list.
Command : This setting is exclusively available for the Specific Command type. It allows notifications to be triggered when the specified command is executed. Commands can be entered as keywords or regular expressions.
Message Template : Customize the message content that administrators will receive with the notification. While each type has a default template, you can personalize it using Message Template Variables as needed.
Channel: Select the channel to which notifications should be sent when an event is triggered by the defined condition.
Save your settings by clicking the
Okbutton.
You will then observe that a new alert has been registered. Henceforth, whenever the trigger conditions defined in the alert are met, a notification will be dispatched to the designated channel.
Alert Policy Example
You can configure alerts to be sent when predefined actions occur, such as server access and command execution. On the Create Alert screen, set up an alert policy with the following conditions:
Alert when a user attempts to connect to your server and fails:
Alert Type : Server Connection Attempt
Alert Trigger Condition : Failure Check Only
Alert when users execute certain predefined commands:
Alert Type : Specific Command
Command : Specify the commands (e.g.,
rm,ls)
Alert when a user downloads a file via SFTP:
Alert Type : File Transfer (SFTP)
Alert Trigger Condition : File Download Only
Alert for unusual login attempts (e.g., 3 failed authentication attempts in 5 minutes):
Alert Type : Unusual Login Attempt
Action Count : 3
Specific Time Interval (Minutes) : 5
Alert Logs
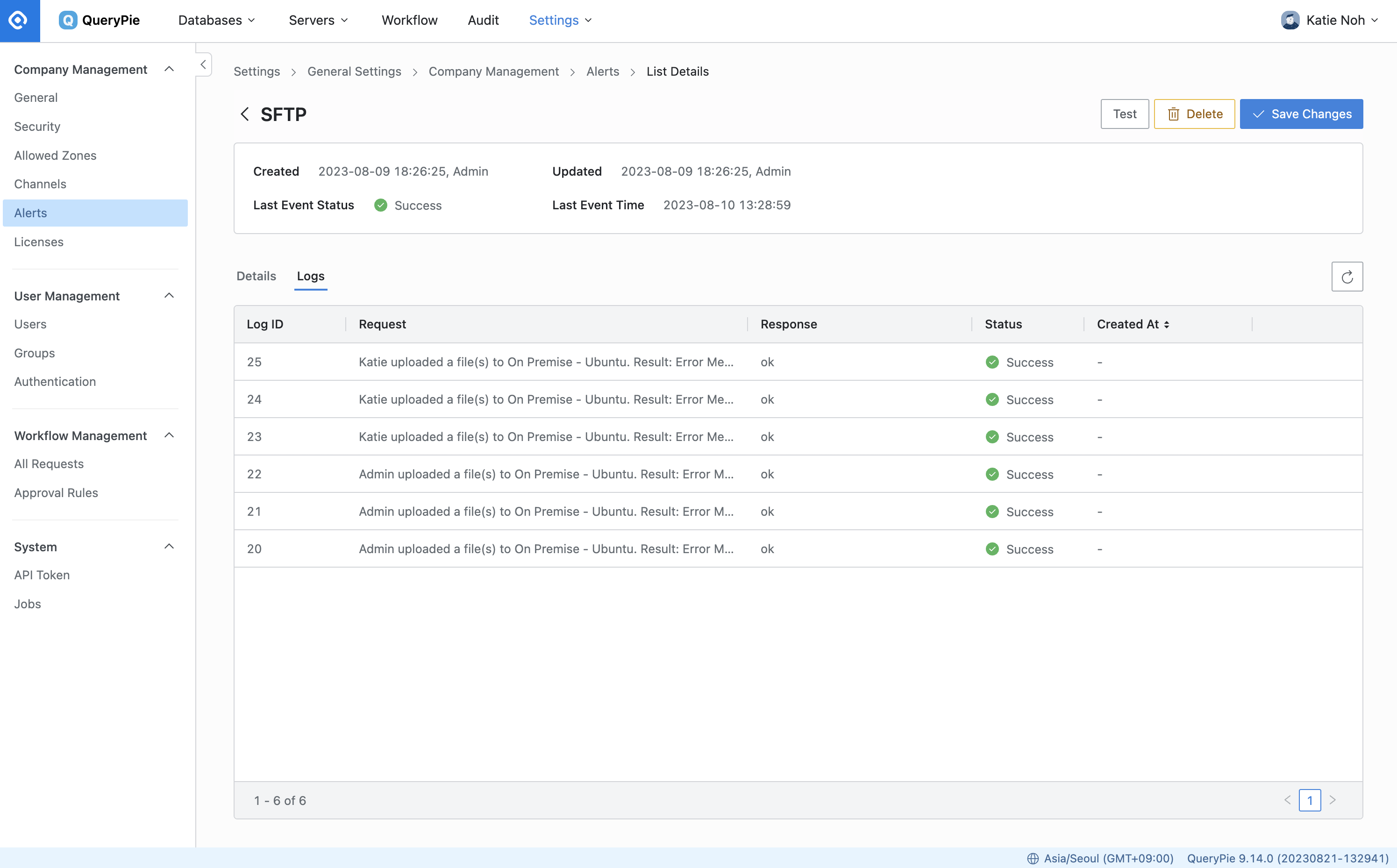
General Settings > Company Management > Alerts > Logs
From the Settings menu, navigate to General Settings > Company Management > Alerts menu.
Select the specific alert for which you want to view the history of sent alerts.
Navigate to the Details tab to access the alert history.
Alternatively, you can check the Logs tab to review the history of alerts sent.
Related Topics