Inventory
Overview
QueryPie provides a categorized list of the resources where access control is managed. In the detailed view, paths containing sensitive information and their associated tags can be viewed, and custom tags can be assigned.
Administrator > Discovery > Discovery Management > Inventory
Key Features of Inventory
Once an administrator has reviewed and confirmed the discovered sensitive information, the tags are finalized and reflected in the data path within the Inventory. The data path refers to the location where sensitive information resides, based on connections registered in QueryPie for database access control, system access control, and Kubernetes access control. (In version 10.0.0, only RDBMS connections under database access control are supported for sensitive information discovery, so Inventory management is limited to these DB connections.)
Types of Tags Used in QueryPie
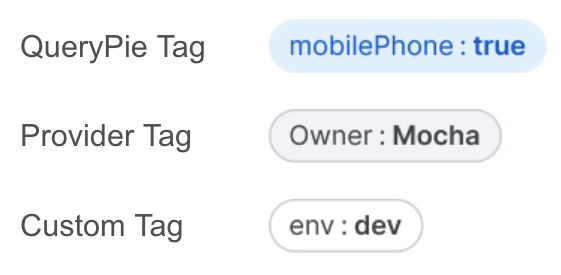
QueryPie Tag (System Tag) : These are system-assigned tags that cannot be modified or added by users.
Provider Tag (Cloud sync tag) : Tags synchronized from the cloud. These tags are managed by the cloud service and cannot be modified, added, or deleted in QueryPie by users.
Custom Tag : Tags that users can freely assign within QueryPie.
Resource Tag : Each connection can have both Provider tags from the cloud and Custom tags assigned by the user. These are collectively referred to as Resource Tags.
< Tag Samples >
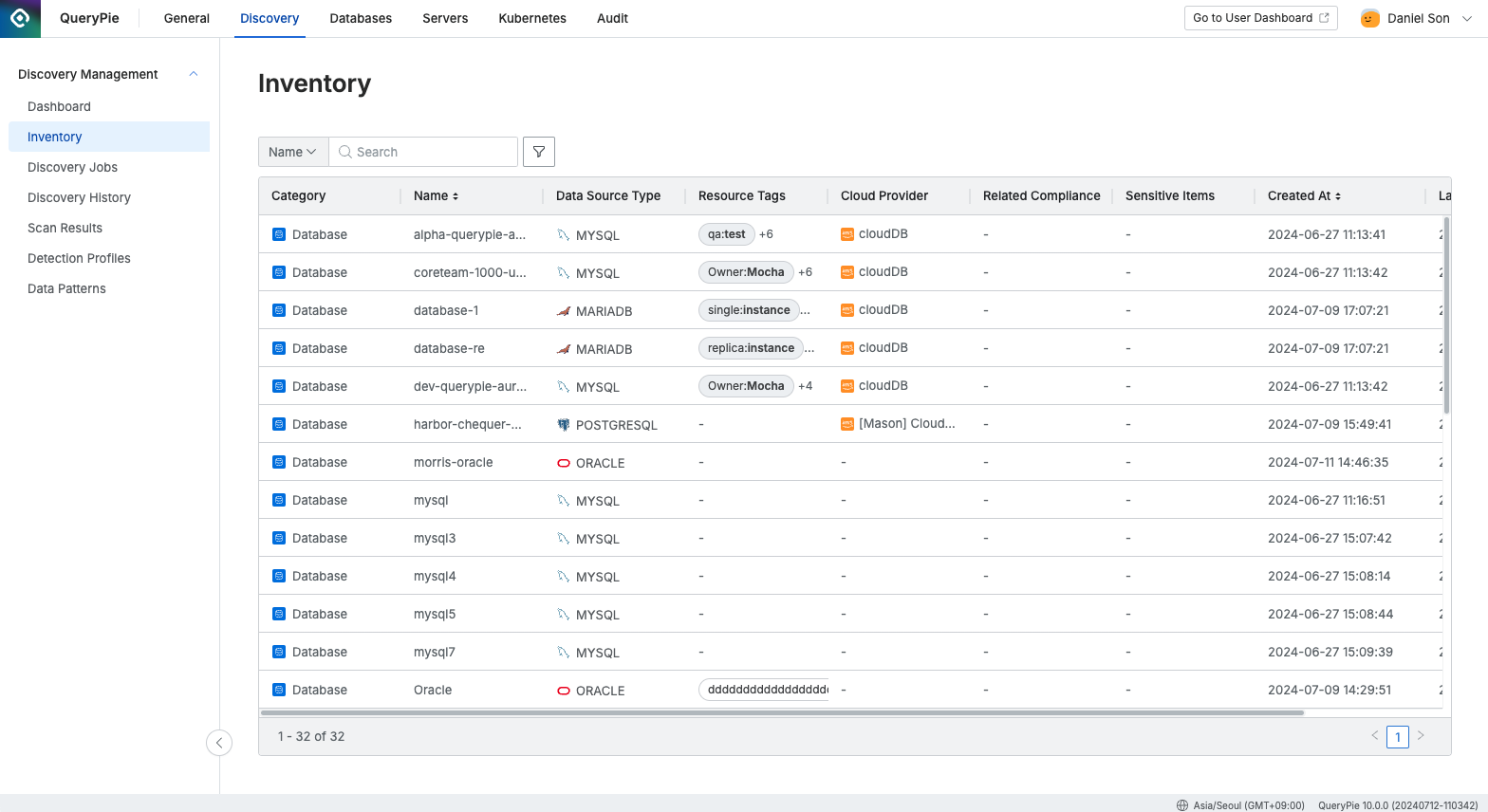
Inventory List
Category : Displays the classification by QueryPie services, including Database, System, and Kubernetes for each access control system.
Name : The name of the connection in use by each access control system. If no connections exist (e.g., immediately after QueryPie is installed), there will be no data to display in the list, so connections must first be created in the access control system.
Data Source Type : The type of data source (e.g., MySQL, Oracle, etc.).
Resource Tags : Tags assigned to the connection, including both Provider tags from the cloud and Custom tags created by the user.
Cloud Provider : The name of the cloud provider if the resource is located in the cloud (e.g., AWS, Azure, GCP).
Related Compliance : If the connection includes a path where sensitive information was found, the related compliance information is displayed.
Sensitive Items : Displays tags related to the discovered sensitive information.
Created At : The timestamp when the connection was created.
Last Updated At : The last time the connection information was updated.
Clicking on each row in the list provides detailed information about the connection and its associated paths.
Managing Connection Information and Resource Tags
In the detailed view, the basic information of the connection and the assigned tags can be reviewed and managed.
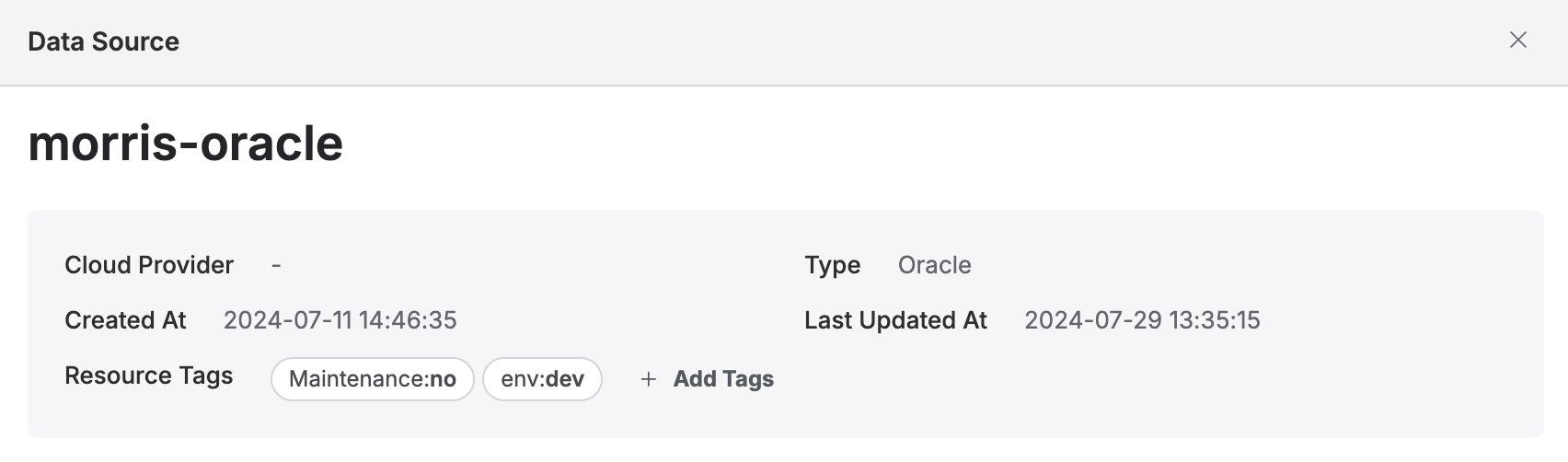
Resource Tags display the tags assigned to the connection (both Provider tags and Custom tags). Tags can be managed by clicking the + Add Tags button.
Data Paths Associated with the Connection
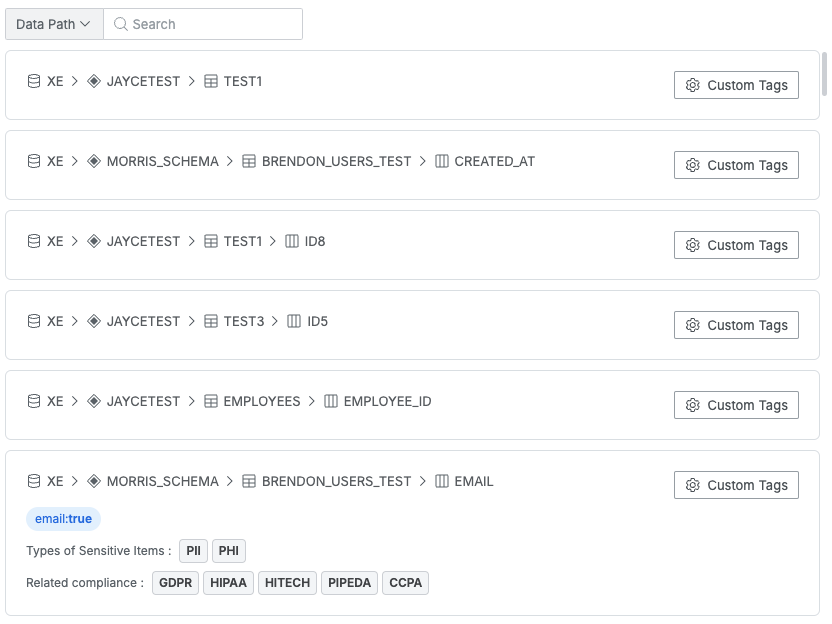
Connections that have successfully completed at least one scan will display the path down to the columns of the target database. The path is structured as follows:![]()
If a column within the path contains confirmed sensitive information based on the Scan Results, the sensitive information tag, its type, and related compliance information can also be viewed.
Assigning Tags to Columns
Custom tags can be assigned to specific columns using the Custom Tags button in each data path.
Known Limitations
Paths for databases that are not supported will not be displayed since the data path can only be collected after a successful scan. (Supported Targets for Discovery: MySQL, MariaDB, Oracle, PostgreSQL, MS SQL Server, Azure SQL.)
At least one successful scan must be completed for the connection specified in the Discovery job to view the target path in Inventory. Otherwise, only the connection itself will be visible.
In Inventory, only custom tags can be assigned to targets. Sensitive information tags are system tags used by QueryPie and must be managed on the Scan Results page.
%201.png)