Security
Overview
On the Security page, you can manage security settings across the entire QueryPie platform. This document provides detailed descriptions of each security setting.
Web Console Login Settings
Manage security settings related to logging into the QueryPie Web Console.
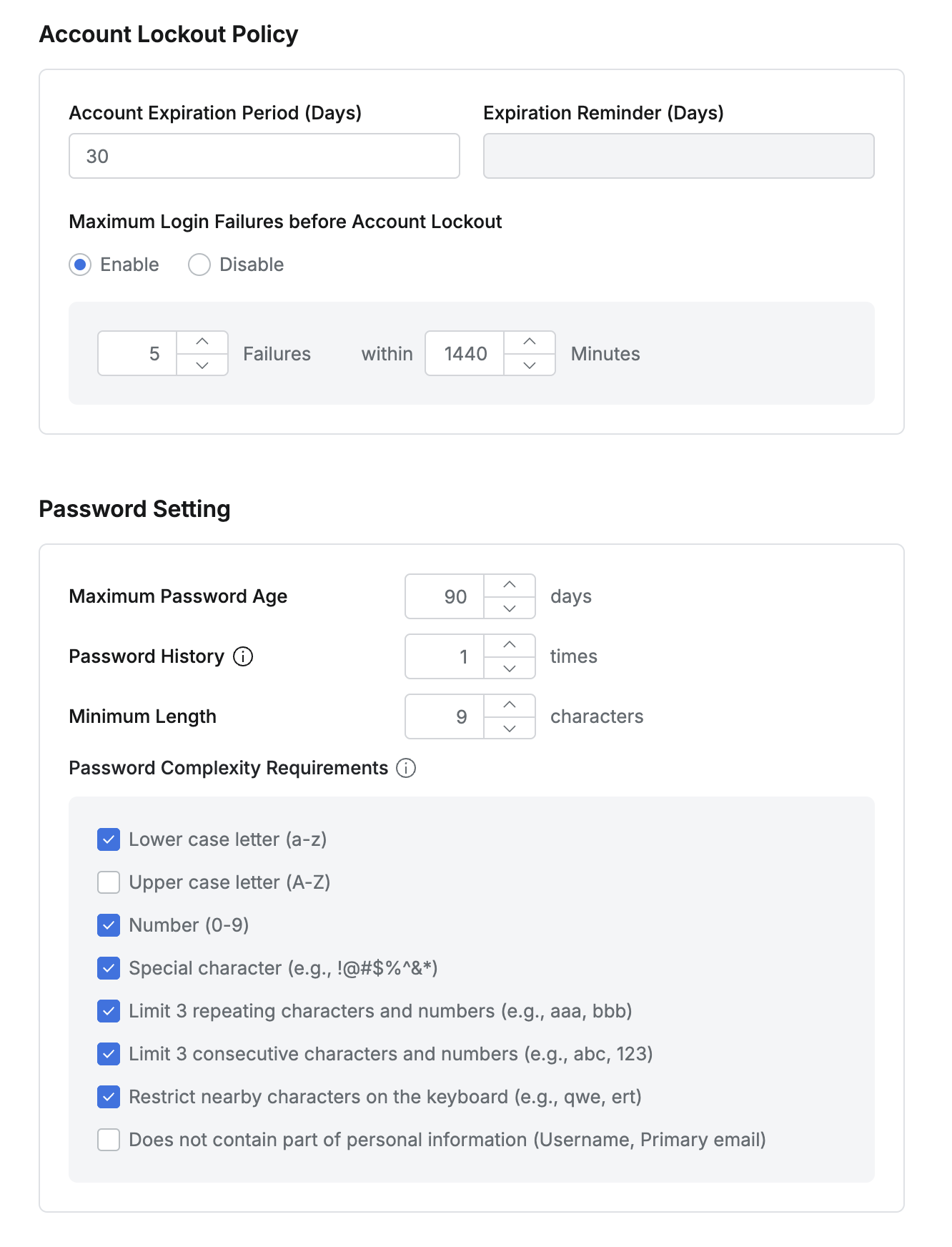
Account Lockout Policy : Policy for account lockout
Account Expiration Period (Days) : Specifies the period of inactivity after which an account will be marked as expired.
Expiration Reminder (Days) DEPRECATED : Defines the period before expiration when a reminder would be sent.
Maximum Login Failures before Account Lockout : Sets the maximum number of failed login attempts before the account is locked.
Default: Account locks for 60 minutes after 5 failed login attempts.
When enabled, additional settings allow customization of the failure count and time (e.g., account locks after 5 failures within 1,440 minutes).
Password Setting : Set password
Maximum Password Age : Defines the password expiration period. (Default is 90 days)
Password History : Specifies the number of past passwords to store, preventing reuse.
The system stores this number of previous passwords, and users cannot reuse them when setting a new password.
Minimum Length : Minimum password length (Default: 9 characters)
Password Complexity Requirements : Password complexity settings
Lower case letter (a-z) : Lowercase letter required
Upper case letter (A-Z) : Uppercase letter required
Number (0-9) : Number required
Special character (e.g., !@#$%^&*) : Special character required
Limit 3 repeating characters and numbers (e.g., aaa, bbb) : Limit repeating characters or numbers of 3 or more
Limit 3 consecutive characters and numbers (e.g., abc, 123) : Limit consecutive characters or numbers of 3 or more
Restrict nearby characters on the keyboard (e.g., qwe, ert) : Limit strings with characters that are adjacent on the keyboard
Does not contain part of personal information (Username, Primary email) : Restrict the use of personal information (Username, Primary email) in the password
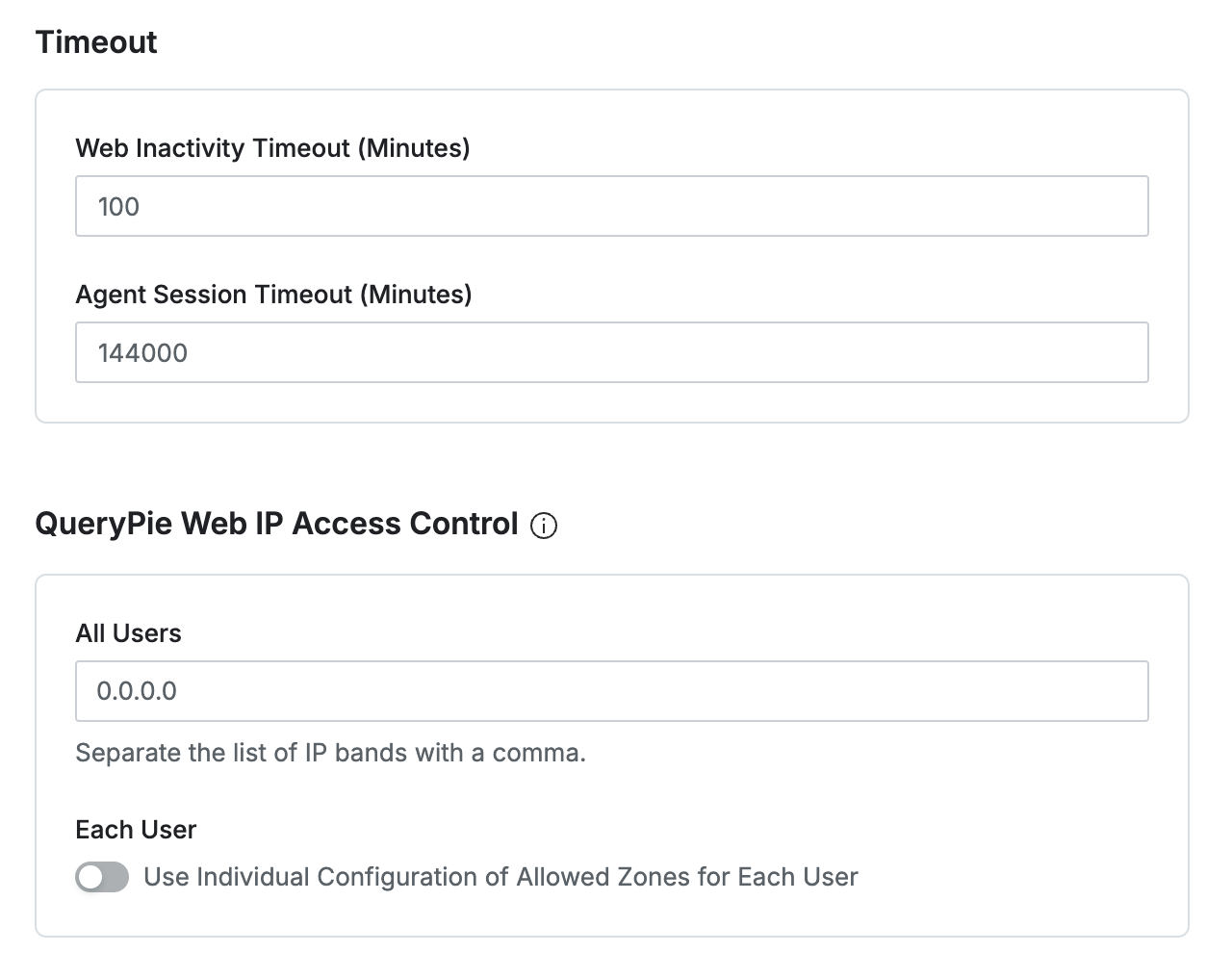
Timeout : Connection Timeout Policy
Web Inactivity Timeout (Minutes) : Sets the timeout period for the web console due to inactivity. The default is 60 minutes.
After this period of inactivity, the session will time out.
Agent Session Timeout (Minutes) : Defines the timeout period for agent sessions. The default is 1,440 minutes.
The agent app login will be maintained for this duration, after which the user will be logged out.
QueryPie Web IP Access Control : IP Restrictions for Accessing QueryPie
All User : Applies IP restrictions to all users. Default allows access from any IP (0.0.0.0/0)
Each User : When toggled on, allows setting an Allowed Zone for each user.
Instructions for configuring Allowed Zones for specific users can be found in the User Profile.
Q. What happens if a user attempts to access the QueryPie web console from an unauthorized IP?
A. If a user attempts to access the QueryPie web console from an unauthorized IP, they will be blocked from accessing any page within the console. These users will see the message screen below. If the default value (0.0.0.0/0) is set for All Users but a specific Allowed Zone is configured for an individual user, they can reach the login page but cannot log in.
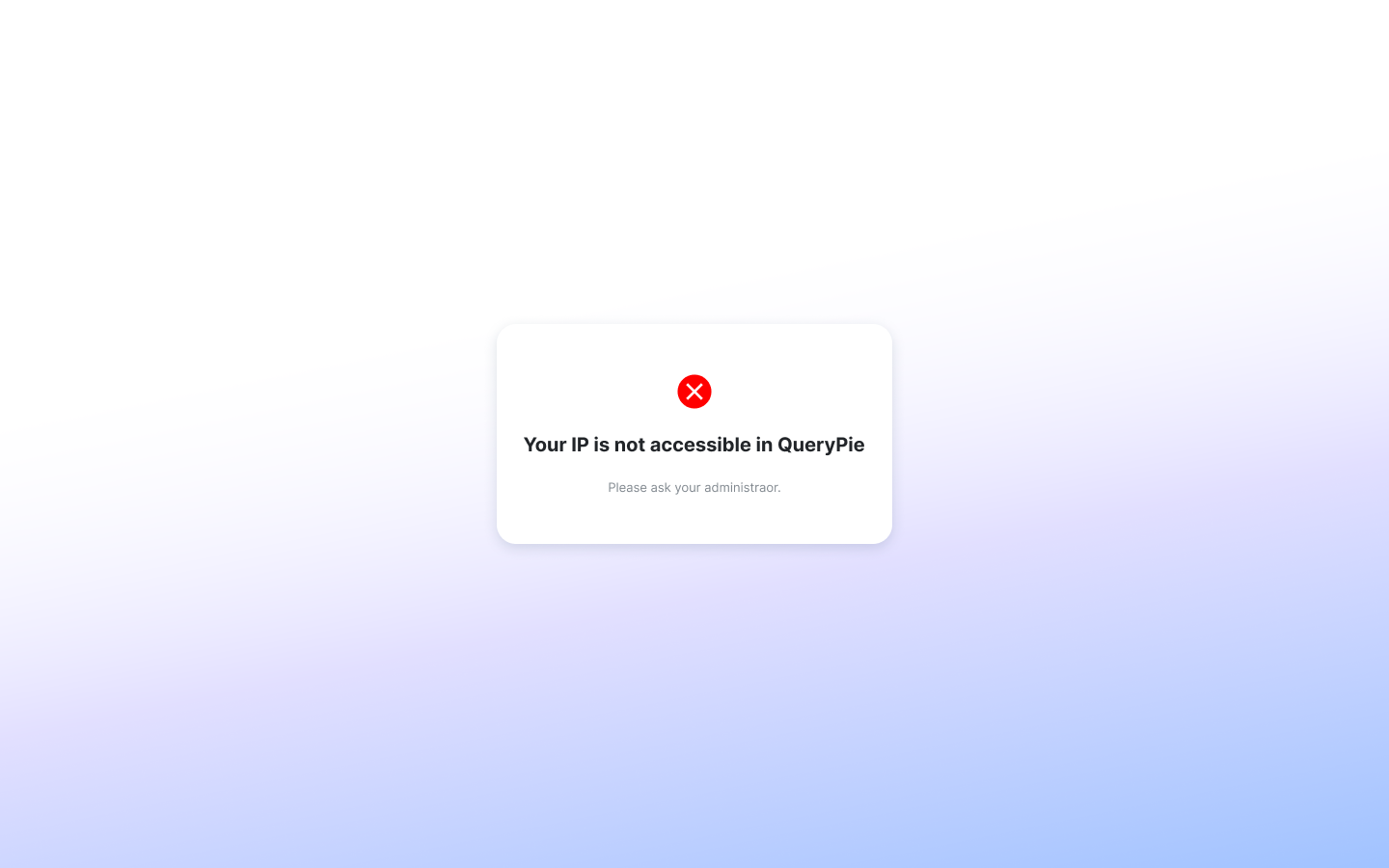
General > Security > QueryPie Web Access Control > All Users Case when the IP is in discord with registered IP.
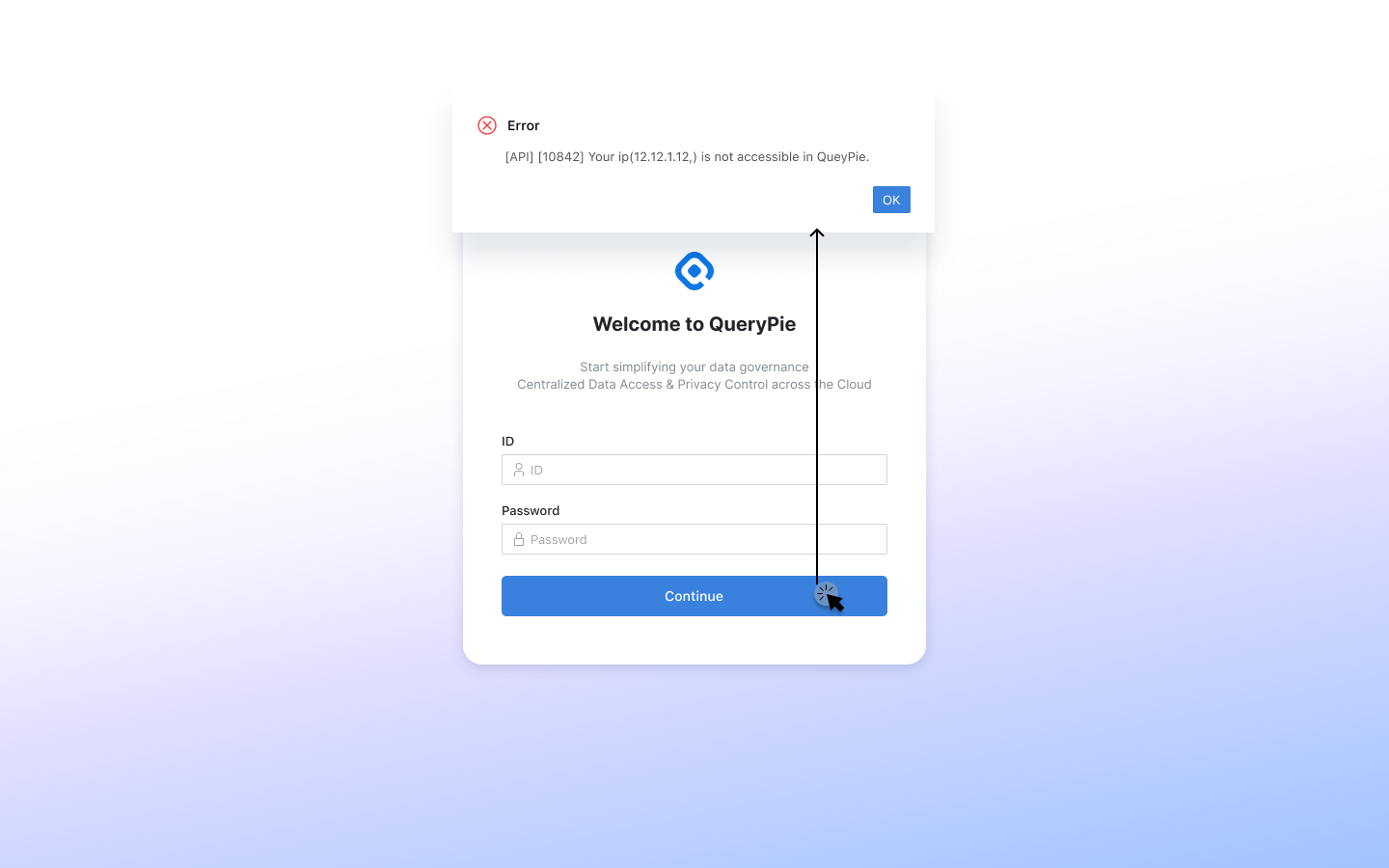
Users > Update User Case when different from registered Allowed Zone
IP Restriction Settings Notice
Settings on the Security page are applied immediately upon saving. Therefore, if the entered IP does not match the administrator’s IP when configuring this option, even the administrator will be logged out immediately after saving. Please proceed with caution when applying these settings.
DB Connection Security Settings
Manage security settings that apply to database access control.
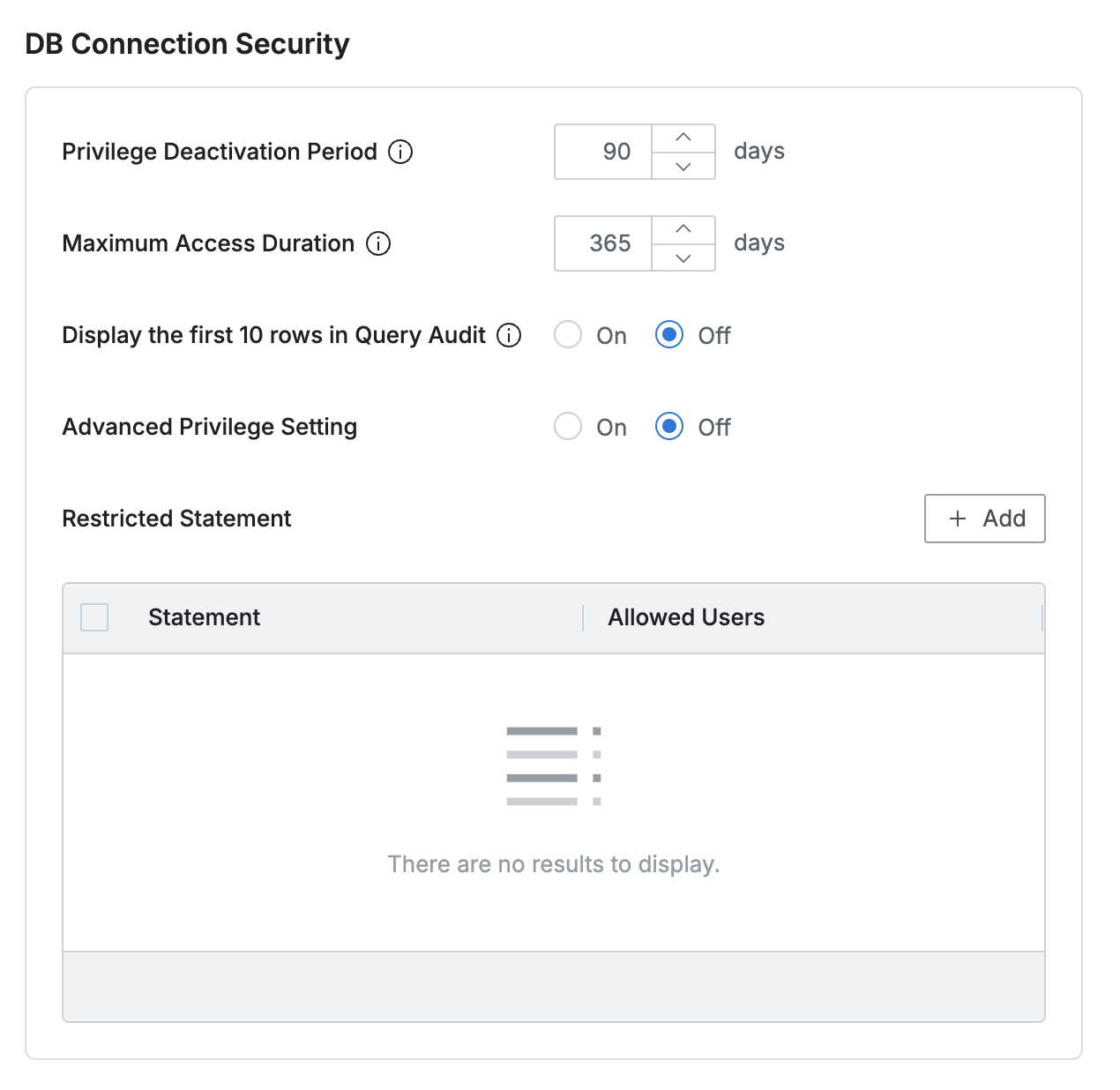
Privilege Deactivation Period : Specifies the period of inactivity after which database privileges will expire. The default is 90 days.
Maximum Access Duration : Defines the maximum duration for which a privilege can be requested or assigned.
When submitting a DB Access Request, the expiration date cannot exceed the specified period.
Display the first 10 rows in Query Audit : Configures how SELECT query results are displayed in Query Audit. The default setting is Off. If turned On, only the first 10 rows of the query result will be displayed, instead of the entire result.
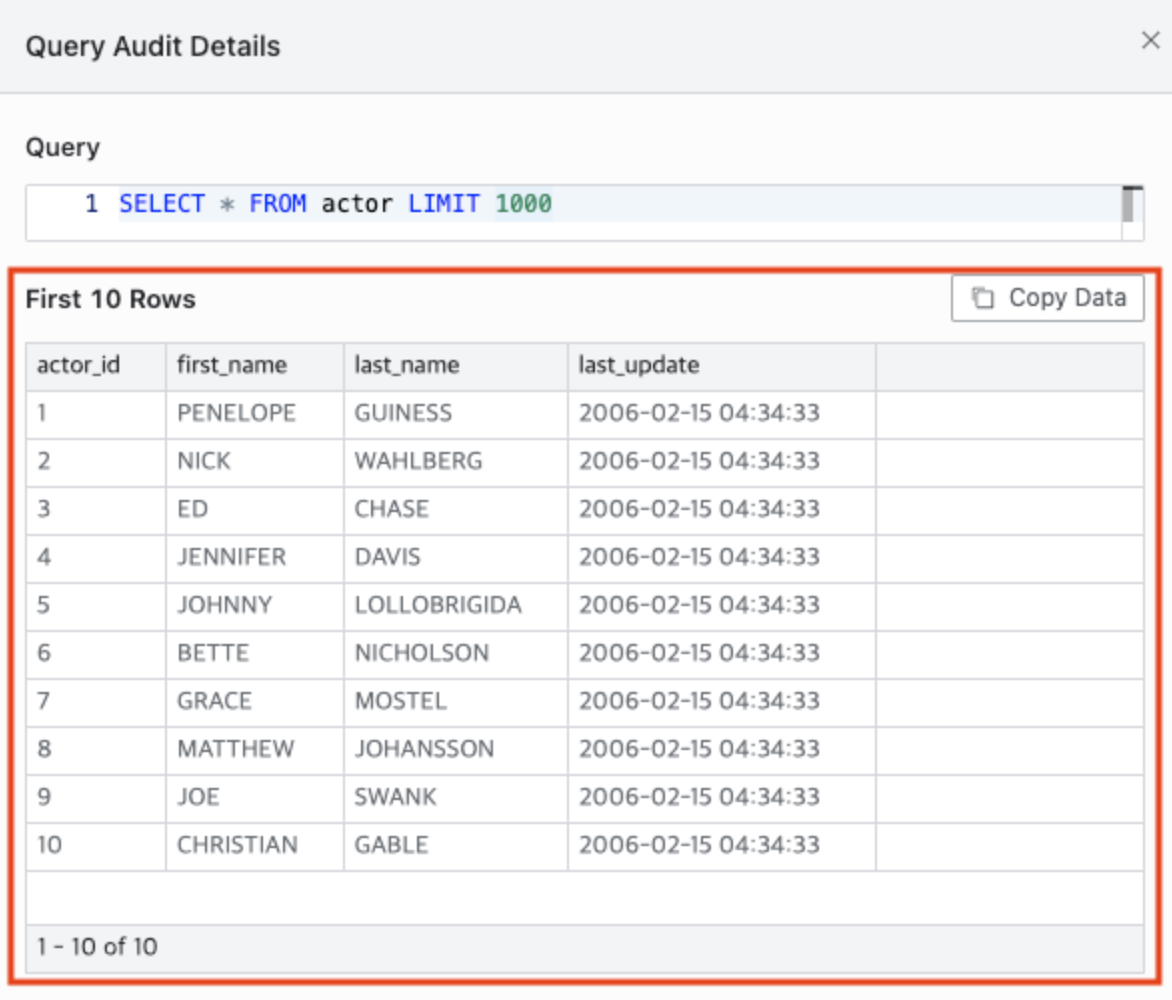
Query Audit Detail
Advanced Privilege Setting : Controls account restrictions based on privilege types. The default setting is Off.
When enabled, a Privilege Settings tab will appear at the bottom of the Connection Details page.
For more information, refer to the Privilege Setting under DB Connections.
Restricted Statement : Usage Restrictions Query
Statement : Specify strings that should be restricted from execution when included in a query (case-insensitive).
Allowed User : Designate users who are permitted to execute queries containing the Restricted Statement (multiple users can be selected, but group selection is not allowed).
Any query containing a Restricted Statement will be blocked from execution unless performed by an allowed user.
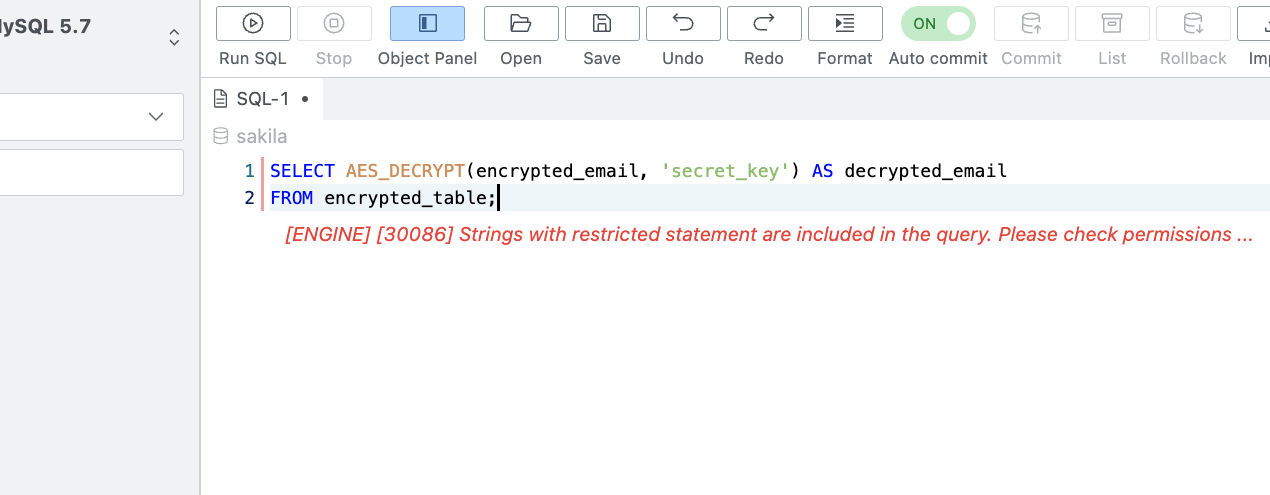
Queries blocked by the Restricted Statement policy will remain blocked, even if approved through an SQL Request. Users should ensure that queries requiring execution are not inadvertently included as restricted statements.
Mandatory Reason Input for DB Operations
Starting from version 9.17.0, this feature has been moved to the connection-specific settings. For detailed configuration instructions, please refer to the Additional Configuration section under DB Connections document.
Server Connection Security Settings
Manage security settings that apply to server access control.
General Settings
Manage basic security settings.
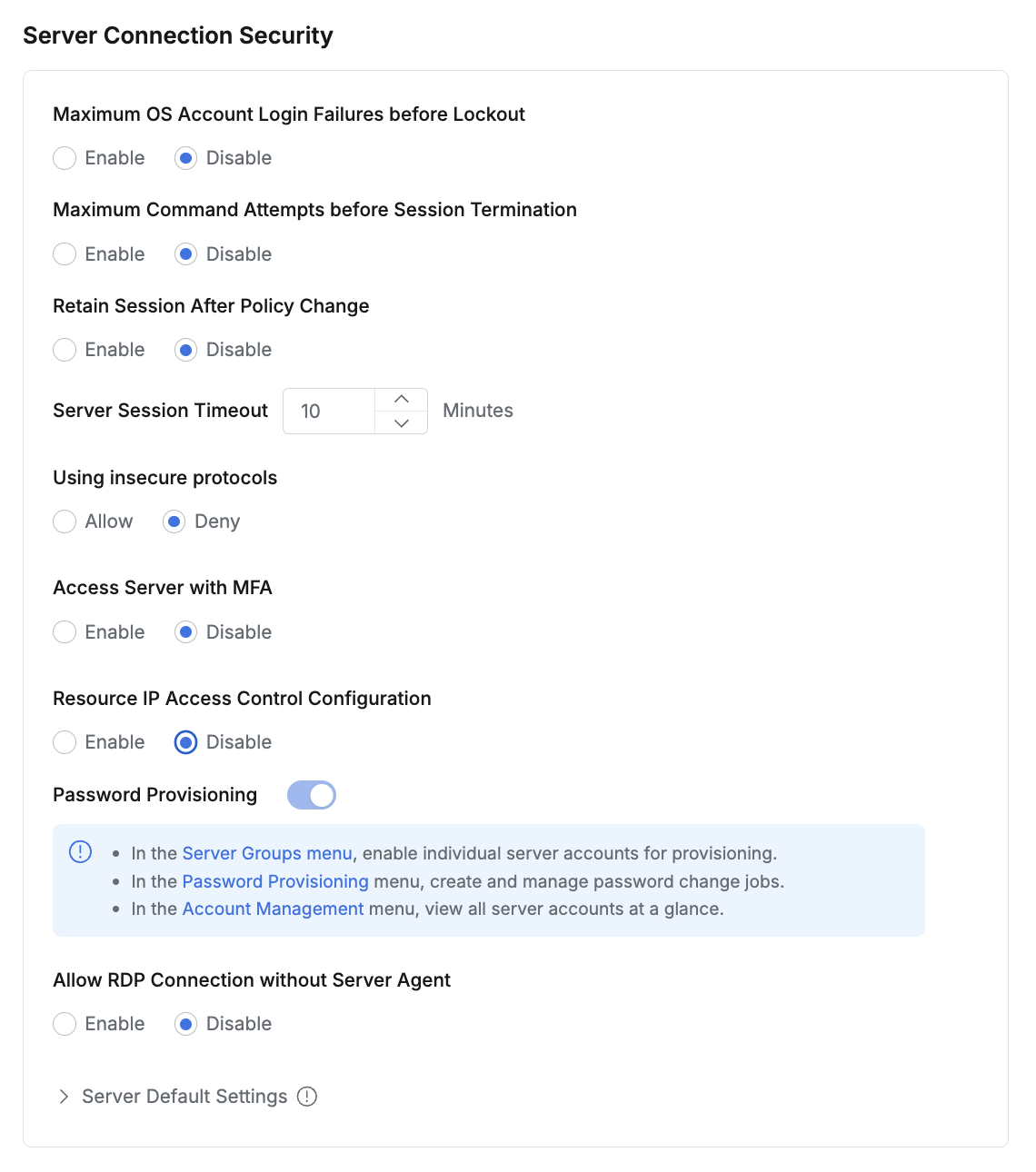
Maximum OS Account Login Failures before Lockout : Account Lockout Policy on Login Failure
Define the maximum number of failed login attempts before the OS account is locked.
When enabled, additional settings allow customization of the failure count and time (e.g., account locks after 2 failures within 11 minutes).
Maximum Command Attempts before Session Termination : Specify the maximum number of attempts to execute a prohibited command before the session is terminated.
When enabled, additional settings allow customization of the attempt count and time (e.g., session terminates after 10 attempts within 10 minutes).
Retain Session After Policy Change : Configures whether to retain active sessions when server access policies are changed.
When "Enable" is selected, the active session will be retained even if the policy is changed, without terminating the connection.
The changed policy will apply to sessions established after the policy update.
Server Session Timeout : Set the timeout period (in minutes) for a server session due to inactivity.
The session times out if no command is executed after the specified duration.
If no individual policy specifies a timeout, this setting applies.
If a timeout is specified in either an individual policy or Server Default Settings, the shorter duration will take precedence.
Using insecure protocols : Enable the server insecure access protocols.
TELNET or FTP
Access Server with MFA : Control whether MFA (Multi-Factor Authentication) is required when accessing servers. The default is Disabled.
Currently supports Google OTP. When enabled, you can specify which servers require MFA based on tags.
Tag input method: Enter a key → Press Enter → Enter a value → Press Enter
The tags will be displayed as
key = value. Servers matching any of the specified tags will require MFA for access.
Resource IP Access Control Configuration : Configure allowed IP access for server connections.
Configures IP access control for servers based on tags.
This takes precedence over Roles or Direct Permissions assigned to Users/Groups.
To add a configuration, click the
Add Configurationbutton, fill out the required details, and clickAdd. (The changes will not apply until you clickSave Changesin the top right.)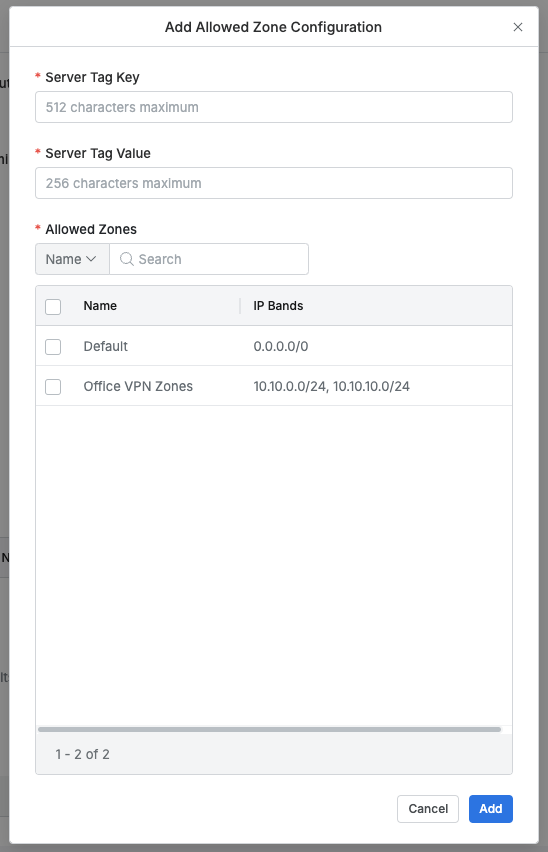
Server Tag Key : Enter the server tag key (required, one at a time).
Server Tag Value : Enter the server tag value (required, one at a time).
Allowed Zones : Choose at least one Allowed Zone from the list in General > Company Management > Allowed Zones (required).
Password Provisioning : Configures whether to enable password provisioning for server accounts.
Periodically changes the passwords of registered server accounts.
When enabled, the following changes occur:
Adds an option to select accounts for password provisioning in the Server Groups.
Activates the Password Provisioning menu and allows the registration of password change jobs.
Activates the Account Management menu, providing a view of the list of server accounts managed by QueryPie.
Allow RDP Connection without Server Agent : Configures whether to allow connections to Windows Server without the RDP Server Agent installed.
Connect to Windows Server via QueryPie using the RDP protocol.
When connecting to a Windows Server without the RDP Server Agent installed, the following limitations apply:
The account used for server access cannot be controlled.
Only server access history is recorded, and the server account used for the Windows login is not logged.
Command audits and session recordings are not recorded.
It is recommended to install the RDP Server Agent for these purposes. After installing the agent, audit and recording features will function normally starting from the point of the next remote connection.
Default Server Access Policy Settings
Manage the server access policies that apply when Direct Permissions are assigned through Workflow requests.
Warning
The policies in effect at the time of Workflow request creation will be applied. Any changes to access policies made after a request has been approved will not be retroactively applied to previously approved requests.
Users can obtain Direct Permission to access servers through a Server Access Request. For more details, please refer to the Server Access Request.
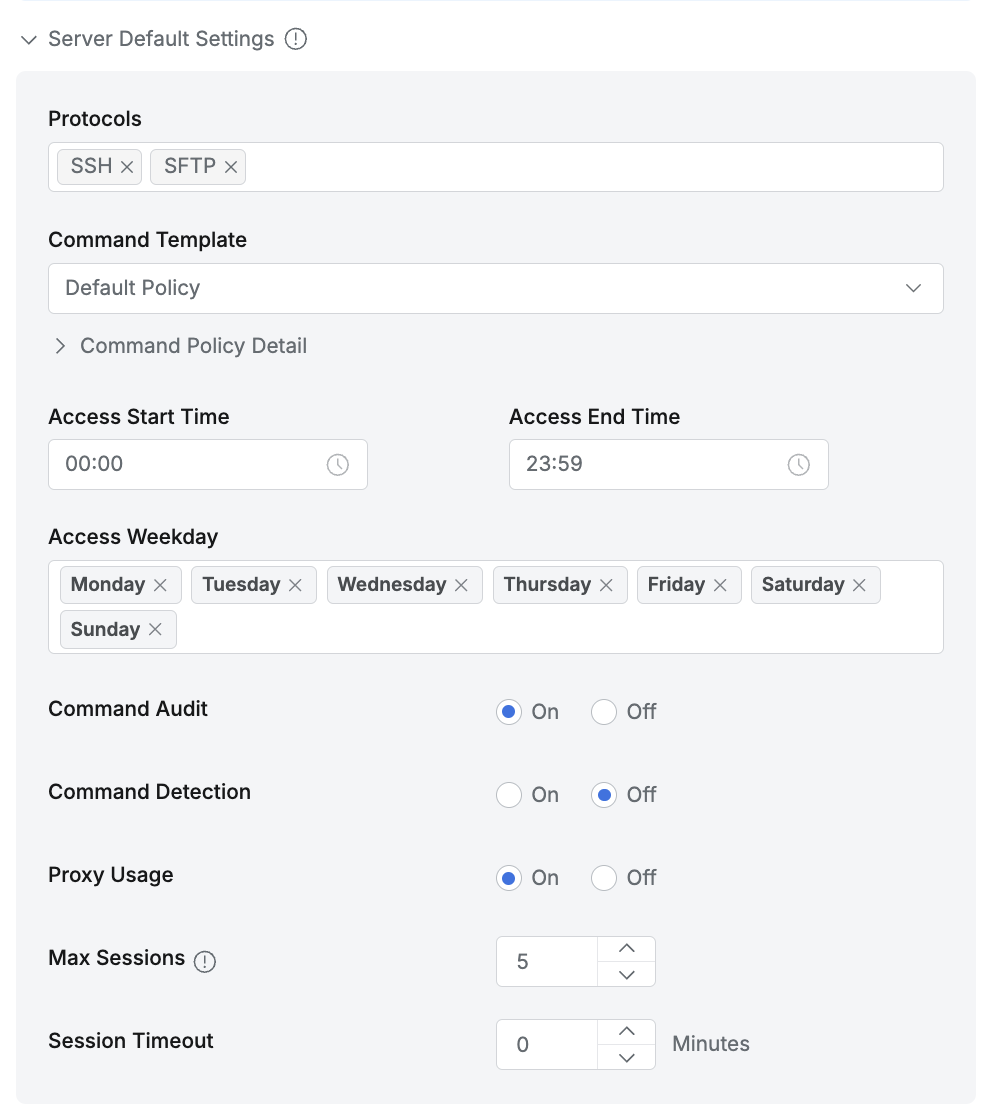
Protocols : Specifies the allowed protocols (as of version 10.0, SSH, SFTP, and RDP are supported).
Command Template : Defines the command-blocking template to be applied during connection.
You can view the details of the selected Command Template by expanding the Command Policy Detail accordion.
For information on creating and managing command-blocking templates, refer to the Command Templates.
Access Start Time : The start time when access is permitted.
Access End Time : The end time when access is permitted.
Access Weekday : Specifies the days of the week when access is allowed.
Command Audit : Determines whether command auditing is enforced during the session.
Command Detection : Detects whether prohibited commands are present within scripts/aliases after connection.
Proxy Usage : Indicates whether proxy access through an agent is allowed.
Max Sessions : Sets the maximum number of simultaneous sessions allowed per server.
Session Timeout : Defines the session timeout duration (in minutes) for server connections.
Kubernetes Access Control Settings
Manage the settings that apply to access control for Kubernetes environments.
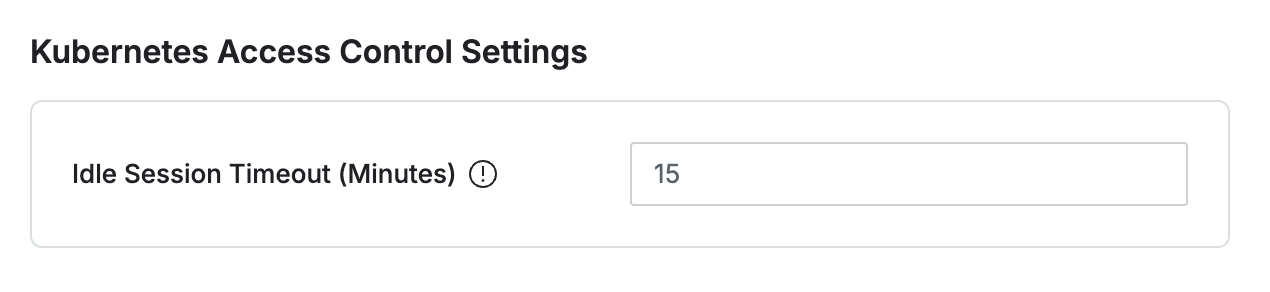
Idle Session Timeout (Minutes) : Pod Session Timeout. The default is 15.
Specifies idle time for session connections through exec, port-forward, and attach.
Secret Store Settings
Configure whether to use the Secret Store. Currently, HashiCorp Vault is supported.
Navigate to the General > Integrations menu for Vault registration.
Q. I want to disable the Secret Store, but the toggle is grayed out. What should I do?
A. Navigate to the Administrator > General > Integrations > HashiCorp Vault menu to check if there are registered Vaults. The toggle can only be deactivated after all registered Vaults have been removed.
Once the Secret Store is activated and Vault registration is complete, you will be able to select the authentication information storage option on the DB Connection Details page or the Server Group Details page.
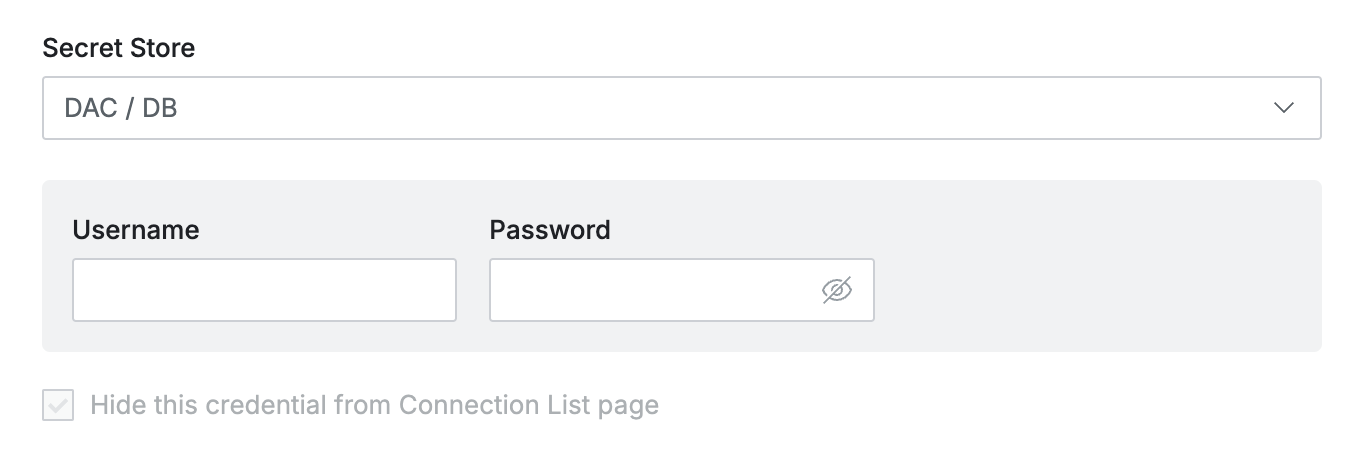
Navigate to the Connection Information > Secret Store under DB Connection page to select Secret Store
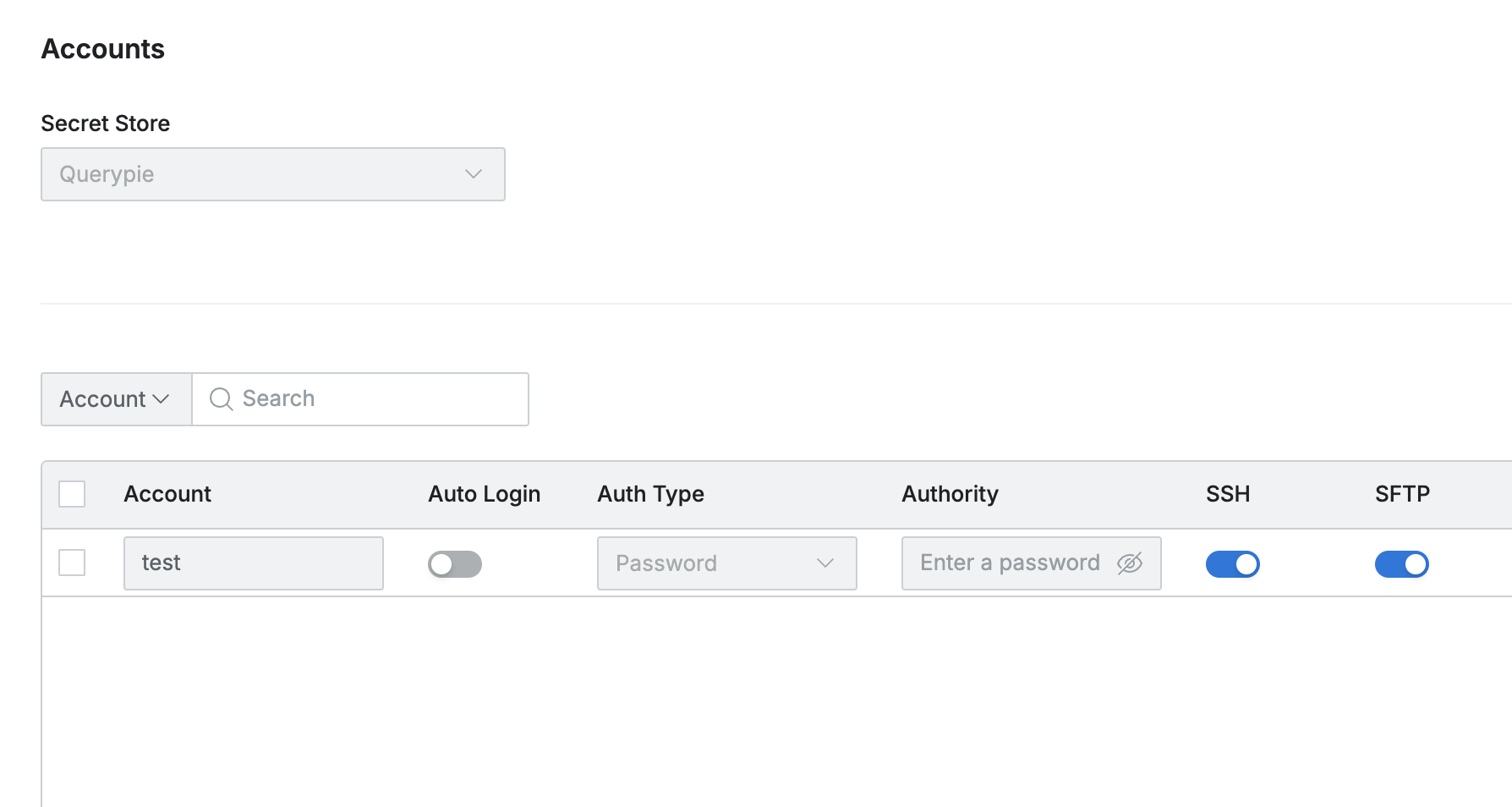
Navigate to the Accounts > Secret Store under Server Group to select Secret Store
Others
Manage additional security settings.
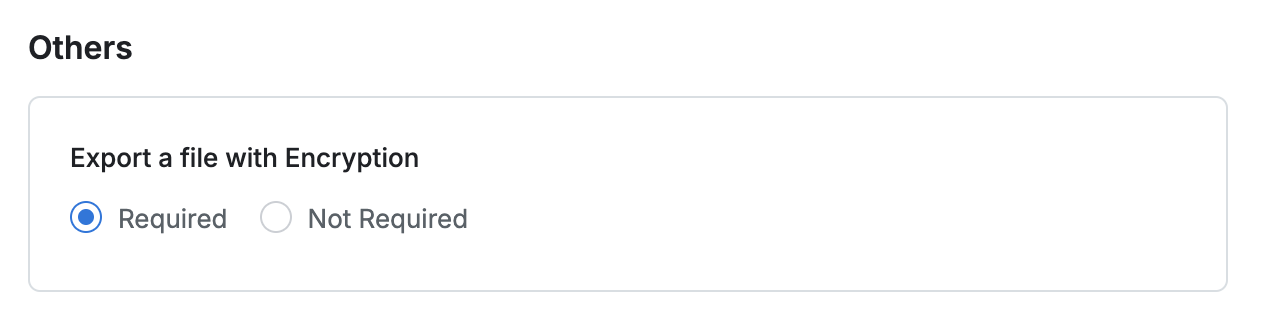
Export a file with Encryption : Determines whether a password is required when downloading files.
If Required is selected, a password must be specified when downloading the file.