Activating Provisioning
Overview
QueryPie’s Provisioning functionality, which operates based on SCIM 2.0 protocol, supports user identity synchronization, providing a more secure integrated user authentication and management environment in addition to SSO that helps existing user authentication and access management. By supporting user lifecycle management, administrators can more conveniently manage new hires and departures within their organization in one place in the account system.
Prerequisites
- This functionality can be activated in the following QueryPie administrator privilege Roles:
- Owner
- System Admin
Activating QueryPie Provisioning
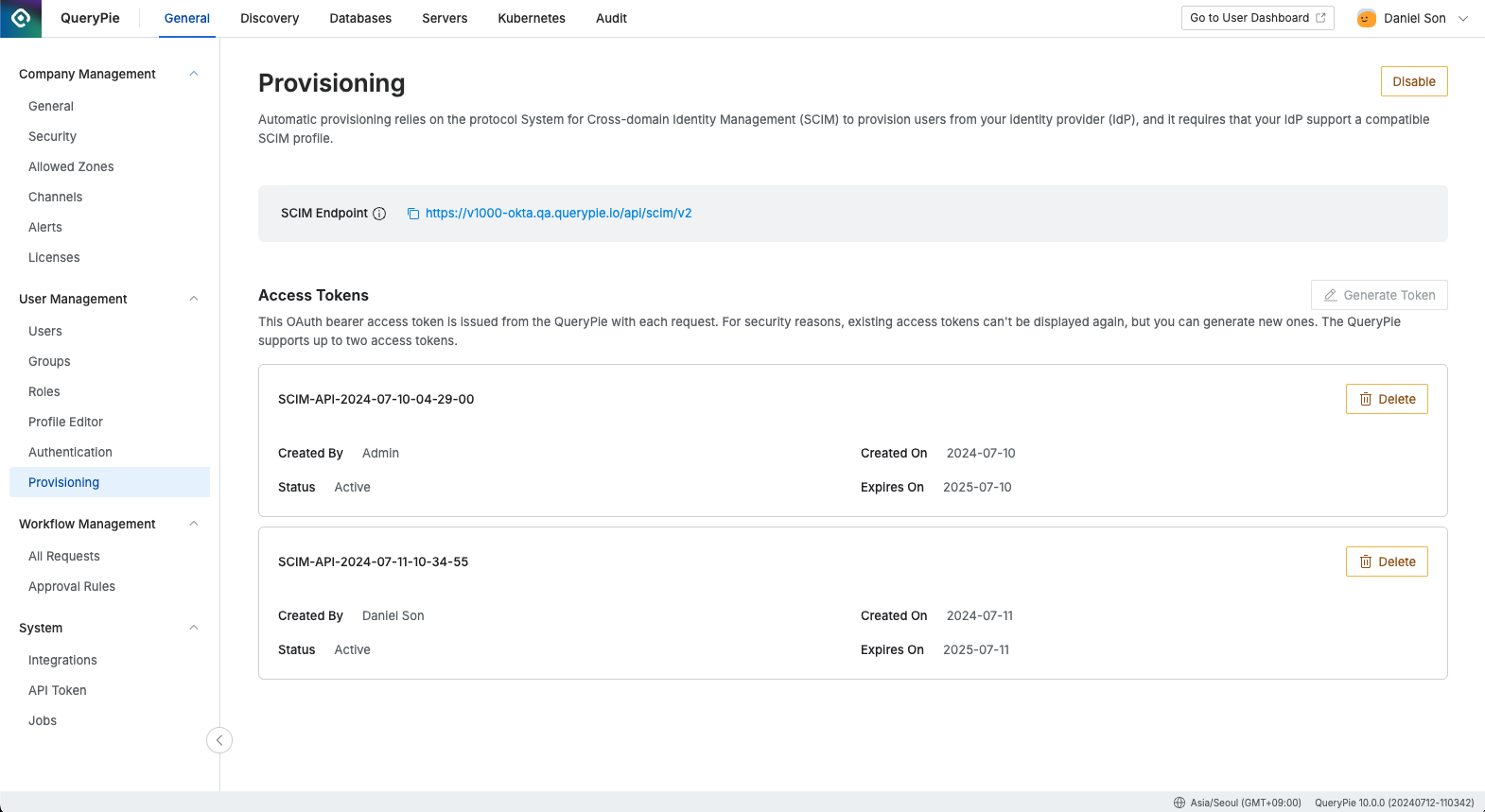
Administrator > General > User Management > Provisioning
- Navigate to Administrator > General > User Management > Provisioning path in the QueryPie app.
- Click the
Enablebutton on the right side of Provisioning to activate SCIM functionality. - Store the address value provided as SCIM Endpoint so it can be set as Base URL in the future.
- Click the
Generate Tokenbutton on the right to issue an Access Token. - When a popup window appears, copy the Access Token value to fill in the token information on the IdP side in the future.
- Since this token value is difficult to retrieve again, we recommend proceeding directly to the Identity Provider that will be the ledger without closing this window. (Refer to Okta-QueryPie Provisioning Integration step)
- If you lose the token value, please delete the existing token and issue a new one through step 4 again.
- Click the
Confirmbutton to close the window.
SCIM Dedicated Token Information
- Access Tokens can be generated through the Generate Token button, and up to 2 can be issued.
- Token values are exposed only once at the time of generation and are not exposed thereafter.
- Can only be used for SCIM API and cannot call endpoints other than /api/scim/v2.
- Newly generated tokens are valid for up to 1 year from the issue date yyyy-MM-dd.
- When the expiration date arrives, the token is processed as Expired and SCIM API cannot be used.
- Administrators must issue new tokens before the expiration date and change the tokens set in existing IdP.
- Tokens can be deleted by selecting the token and clicking the
DELETEbutton. - If an administrator disables Provisioning after issuing tokens and then re-enables it, all existing tokens are deleted at the time of deactivation, so the administrator must issue new valid tokens.
Last updated on