SAC General Configurations
Starting from version 10.3.0, SAC-related configuration items that were previously under Administrator > General > Security have been moved to General > Configurations under each service menu. From 11.5.0, email notification functionality has been added to notify users before permission expiration (Permission Expiration, Privilege Expiration, Role Expiration).
Overview
The Configurations page is a settings page in QueryPie where you can manage server access and security policies. You can configure core elements of server connection security such as login failure threshold settings, session timeouts, and insecure protocol controls. This allows administrators to configure server environments according to their organization’s security requirements and protect systems from potential threats.
Server Connection Security Settings
Manage security settings applied to server access control.
General Settings
Manage basic security settings.
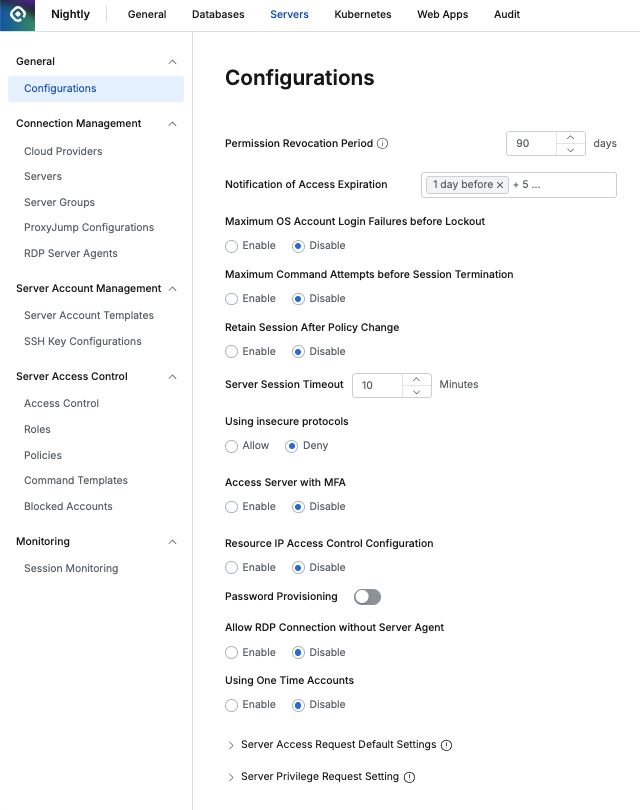
- Permission Revocation Period : Automatic revocation of server permissions for long-term inactive users
- When Enable is selected, server access permissions granted to users are automatically revoked if they do not access the server for the specified period (days).
- Important Notes
- This only applies to Direct Permissions or Role permissions with expiration dates that are directly granted to users.
- Permissions inherited from groups or permanent permissions without specified expiration dates are not affected by this feature.
- If a user has never accessed the server after being granted permission, the period is calculated from the time the permission was granted.
- Notification of Access Expiration : Enables email notifications before permission expiration (Permission Expiration, Privilege Expiration, Role Expiration).
- Maximum OS Account Login Failures before Lockout : Account lockout policy for login failures
- Specify the maximum number of server login failures allowed
- When Enable is selected, additional input is possible based on count and time range criteria (e.g., account lockout after 2 failures within 11 minutes)
- Maximum Command Attempts before Session Termination : Maximum execution count for prohibited commands
- When Enable is selected, additional input is possible based on count and time range criteria (e.g., session termination after 10 attempts within 10 minutes)
- Retain Session After Policy Change : Setting for maintaining connected sessions when server access policies are changed
- Enable selection:
- Active sessions are maintained and not terminated even in the following cases:
- Direct permission grant or revocation
- Policy updates
- User role changes
- However, sessions for related resources are terminated if the user’s role or permissions are completely removed
- Session reconnection is required to apply changed policies
- Active sessions are maintained and not terminated even in the following cases:
- Disable selection:
- All connected sessions are automatically terminated when policies are changed
- Changed policies are applied to newly connected sessions
- Enable selection:
- Server Session Timeout : Server session timeout criteria (minutes)
- Timeout when no commands are executed after server access for the specified time
- This setting applies when no timeout is specified in individual policies
- If timeout policies are specified in individual policies or Server Default Settings, the shorter one is applied
- Using insecure protocols : Setting for using server access protocols that are not recommended
- Set whether to use TELNET or FTP
- Access Server with MFA : MFA authentication when accessing servers (Default : Disabled)
- Currently supports Google OTP, and when this option is selected, servers to apply MFA authentication are specified by tag criteria
- Tag input method: key input → Enter key input → value input → Enter input
- Input tags are displayed in
key = valueformat, and servers with at least one tag matching the input tags can be accessed after MFA authentication
- Currently supports Google OTP, and when this option is selected, servers to apply MFA authentication are specified by tag criteria
- Resource IP Access Control Configuration : Server access allowed IP access control settings
- Specify servers to apply IP access control by tag criteria
- Applied with priority over Roles or Direct Permissions granted to Users/Groups
- When the
Add Configurationbutton is clicked, a modal is created and the following information is entered to click theAddbutton (not reflected until theSave Changesbutton in the top right is clicked)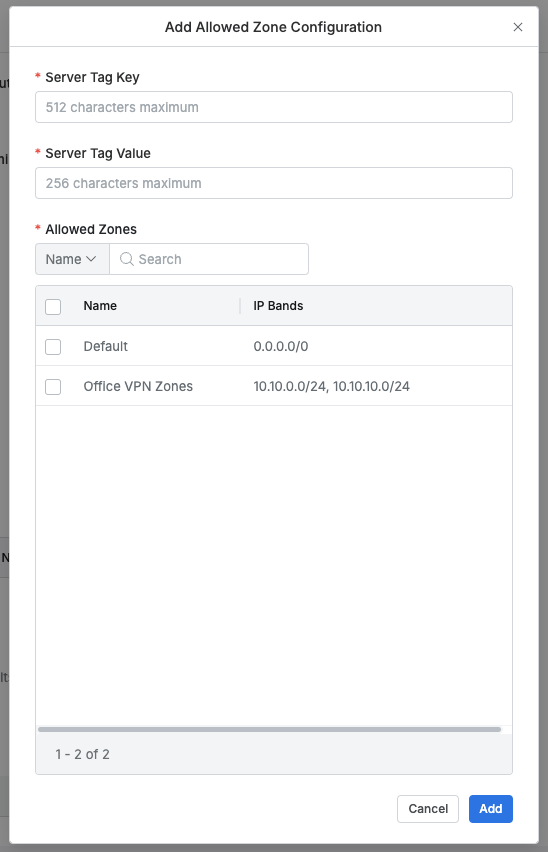
- Server Tag Key : Enter the server tag key, only one can be applied at a time (required when used)
- Server Tag Value : Enter the server tag value, only one can be applied at a time (required when used)
- Allowed Zones : Loads the list from General > Company Management > Allowed Zones, minimum 1 selection required when used
- When this feature is activated, the IP ranges of Allowed Zones set here are displayed when users access servers.
Important Notes Allowed Zones represent broad ranges of allowed IP addresses. Therefore, even if you are within the displayed IP range, final access may be denied if administrators have set additional IP restrictions through data policies (DP/Policy), etc.
- Password Provisioning : Setting for using password provisioning
- Periodically change passwords for server accounts of registered servers
- When set to On, the following changes occur:
- In Managing Servers as Groups | 3.-Registering-Accounts, account selection options for password provisioning are added
- Password Provisioning menu is activated and Password change Jobs can be registered
- Account Management menu is activated and provides account list lookup functionality for servers managed by QueryPie
- Allow RDP Connection without Server Agent : Setting for allowing access to Windows Servers without RDP Server Agent installed
- Access Windows Servers via RDP protocol through QueryPie
When accessing Windows Servers without RDP Server Agent installed, the following limitations apply:
- Server accounts used for server access cannot be controlled.
- Only Server Access History is recorded, and the server account used for Windows access is not recorded.
- Command Audit and Session Recording are not recorded.
- It is recommended to use this only for the purpose of installing RDP Server Agent, and Audit and recording work normally from the point when remote connection is restarted after RDP Server Agent installation.
- Using One Time Accounts : Setting for using temporary login accounts
- Sets whether to use the feature that creates unique temporary accounts for each server session.
- When Enable is selected, it works as follows:
- QueryPie - One Time Account is added as an Account category in Server Groups menu settings.
- Provisioning accounts and One Time Accounts can be registered in the system.
- When accessing servers, the system automatically creates temporary accounts on the server.
Default Policy Settings for Server Permission Requests
Manage server access policies applied when assigning Direct Permissions through Workflow requests.
Warning Policy content is reflected based on the Workflow request creation time. Even if access policies are changed after the request is approved, they are not retroactively applied to previously approved requests.
Users can be assigned Direct Permissions for servers through Server Access Request. For more details, please refer to Requesting Server Access Request.
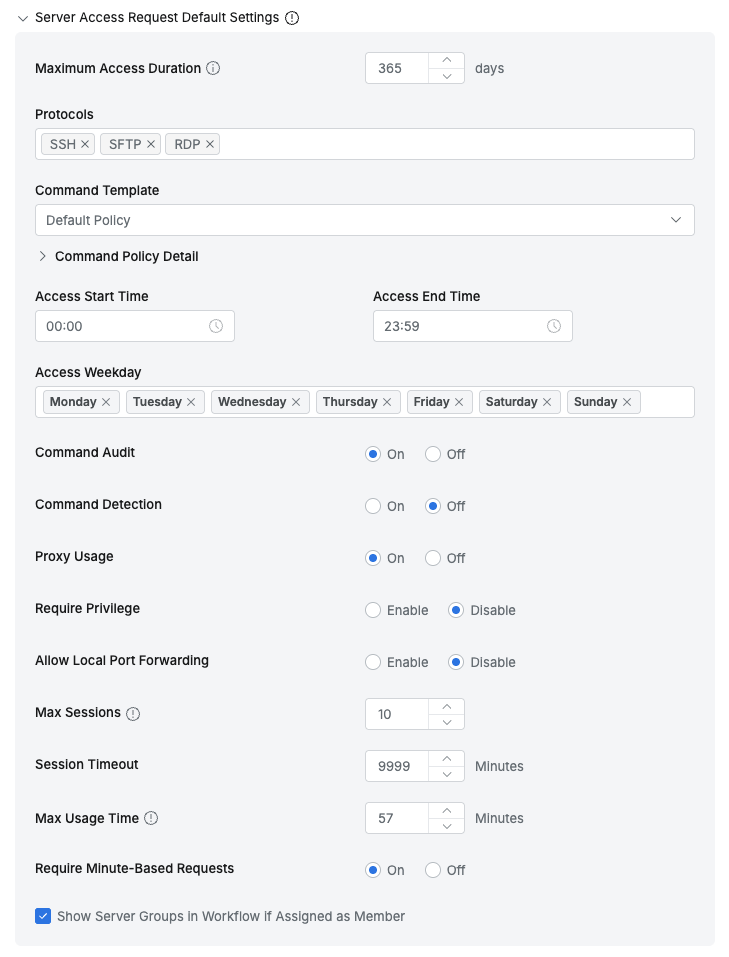
- Maximum Access Duration : Set the maximum usage period for server access permissions
- Protocols : Allowed protocols (Supported protocols: SSH, SFTP, TELNET, FTP, RDP, VNC)
- Command Template : Blocked command template to apply when accessing
- The content of the selected Command Template can be checked by expanding the
Command Policy Detailaccordion - For creating and managing blocked command templates, refer to Command Templates
- The content of the selected Command Template can be checked by expanding the
- Access Start Time : Allowed access start time
- Access End Time : Allowed access end time
- Access Weekday : Allowed access days of the week
- Command Audit : Whether to apply command auditing when accessing
- Command Detection : Whether to detect prohibited commands within Script/Alias after access
- Proxy Usage : Whether to allow proxy access through Agent for this permission
- Allow Local Port Forwarding : Whether to allow Port Forwarding from Client
- Used when using Port Forwarding such as VSCode
- Max Sessions : Maximum concurrent connections per server
- Session Timeout : Server session timeout criteria time (minutes)
- Show Server Groups in Workflow if Assigned as Member : When checked, only server groups assigned as Server Group Members are displayed when users apply for Server Access Request
- Require Minute-Based Requests : Allow minute-based requests for server-related permission requests in Workflow. If not set, permissions are requested in days. When checked, server access permission requests are made in minutes
Server Privilege Request Policy Settings
Set policies applied when users request server privileges (Server Privilege).
Warning Policy content is reflected based on the Workflow request creation time. Even if access policies are changed after the request is approved, they are not retroactively applied to previously approved requests.
Users can be assigned server privileges through Server Privilege Request. For more details, please refer to Requesting Server Privilege Request.
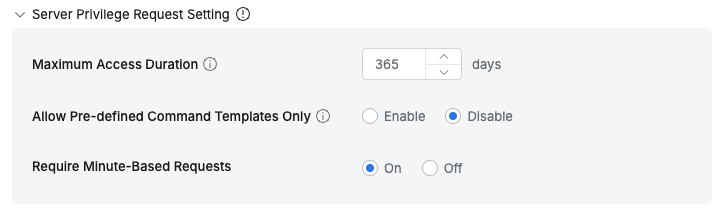
- Maximum Access Duration : Set the maximum duration for privilege usage
- Allow Pre-defined Command Templates Only : Control command input methods when requesting server privileges
- Enable : Requesters can only select from command templates pre-defined and allowed by administrators, and cannot input commands directly
- Disable : Requesters can input allowed commands directly as before
- Require Minute-Based Requests : Allow minute-based requests for server-related permission requests in Workflow. If not set, permissions are requested in days. When checked, server privilege requests are made in minutes