Proxy Management
Overview
QueryPie supports proxy connections when users access databases and systems. While providing access through its own developed web editor and terminal, it also supports access through proxy authentication information generated by QueryPie. When accessing through external clients, all access to resources can be controlled by routing through a proxy server, and all access without going through the proxy can be blocked.
QueryPie Proxy Introduction
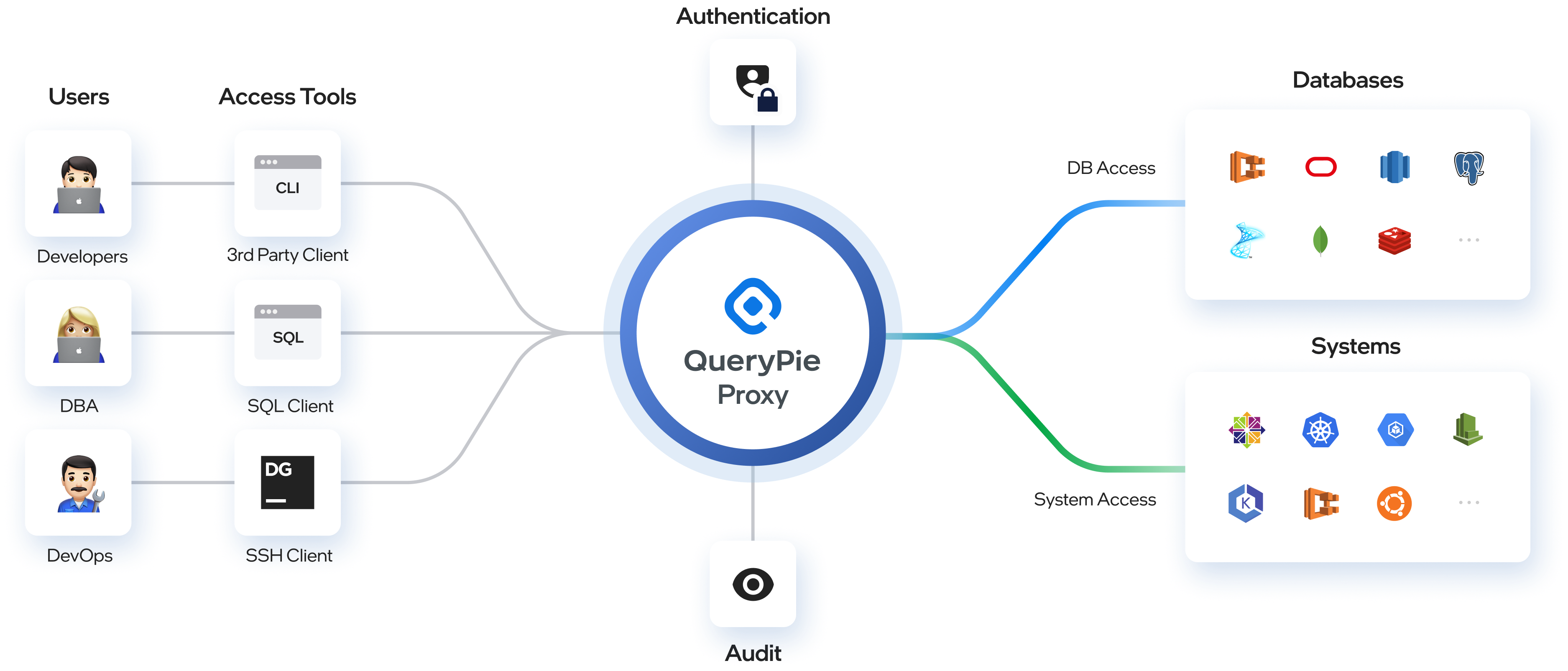
- Enhanced Security : The proxy function acts as a security intermediary between users and resources, adding a security layer against unauthorized access and potential security breaches.
- Centralized Control and Auditing : The proxy can record and audit all users’ resource access and activities. This centralized auditing function is essential for compliance and ensures accountability and transparency.
- Real-time Monitoring : Through real-time monitoring of user behavior and activities, anomalies and potential threats can be identified to effectively mitigate risks.
- Block Unauthorized Remote Access : Using a proxy enables secure remote access to databases and systems, eliminating the need for users to directly access sensitive resources and minimizing exposure of critical infrastructure to external threats.
How QueryPie Proxy Works
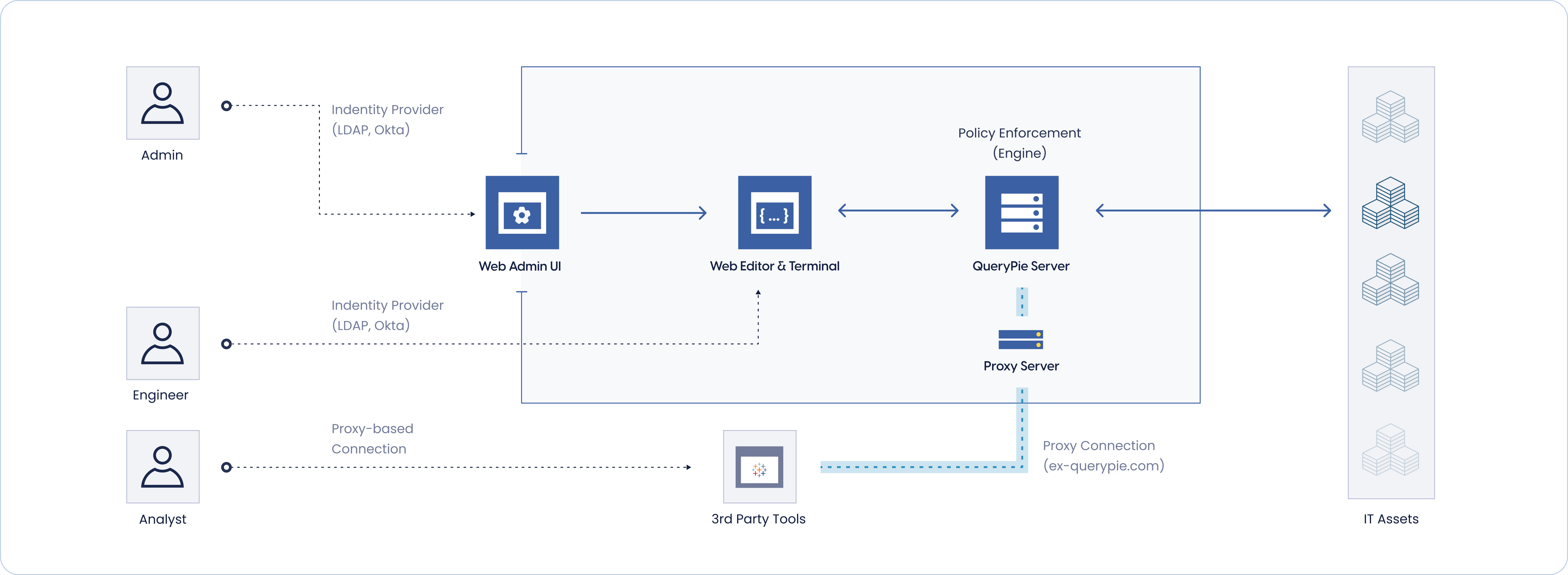
- Proxy Configuration : Administrators configure whether to use proxy for each resource within QueryPie’s interface.
- User Authentication: Users securely connect through QueryPie authentication. Before connecting to the proxy, user authentication information is verified to confirm that the user is an authorized user.
- Access Control: The proxy function checks pre-defined access permissions to ensure users can only connect to databases and systems they have access to.
- Privacy Protection : Even for proxy connections, data access and masking policies are applied to protect important data from users without explicit access permissions.
QueryPie’s proxy function redefines database access and security, providing a powerful protection layer that protects data, enhances access control, and minimizes vulnerabilities. The proxy helps organizations maintain privacy and compliance standards by restricting user resource access and applying security policies.
Last updated on