System Architecture Overview
Overview
QueryPie has a web application architecture that operates in both cloud and on-premises environments.
QueryPie typically operates as a Docker container on Linux VMs and is recommended to be operated as a web application protected by TLS certificates. When customers install and operate QueryPie in a cloud environment, it is recommended to configure it with a load balancer and TLS certificates. Resources necessary for QueryPie operation, such as connection settings and user information, are stored in a MySQL database. Redis is utilized as temporary storage for fast response times.
QueryPie’s binary package is built as a Docker image and is prepared for deployment on Linux VMs or physical Linux servers in Azure, AWS, and GCP when the OS and Docker daemon are recent versions. It also natively supports Kubernetes, but is primarily recommended for customers with Kubernetes DevOps teams.
For customers who want to try out the product, we offer the Community Edition: QueryPie ACP Community Edition Community Edition users are provided with a license to use the product for one year, and they can continue using it by renewing the license even after one year.
Simple Configuration for Trial Evaluation
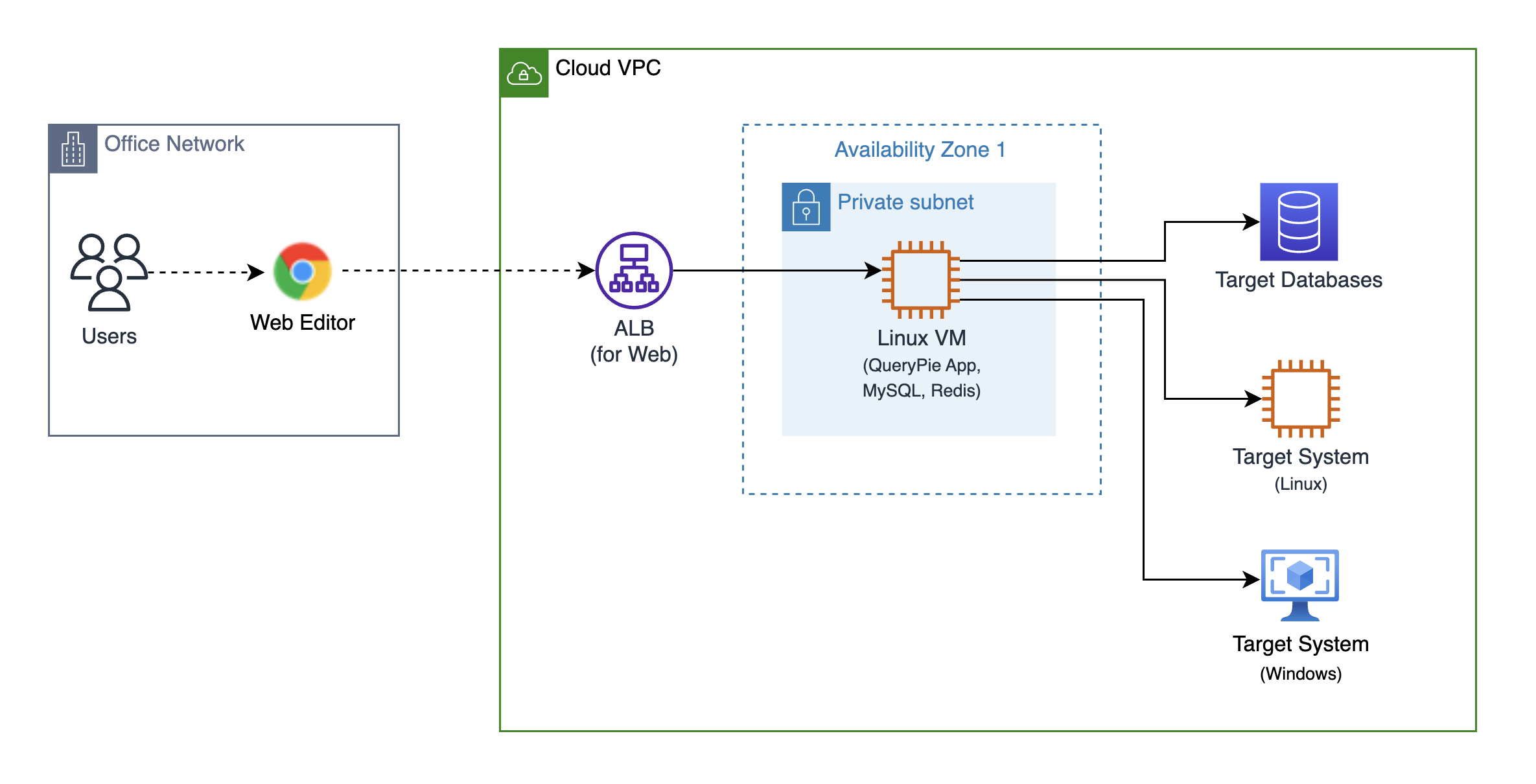
Simple System Configuration for Evaluation
The system structure above is a simple configuration example for trialing and evaluating the QueryPie product. Users access QueryPie through a web browser, and QueryPie is installed and operates on a single Linux VM connected to an Application Load Balancer. Inside the Linux VM, the QueryPie application runs in Docker container mode, and the MySQL database and Redis cache used by QueryPie also run in Docker container mode.
QueryPie will have a web service URL with TLS certificates applied, such as https://querypie-poc.customer.com/, and it is recommended to set up an Application Load Balancer with TLS certificates for this purpose.
Prerequisites for Trial Evaluation Configuration
The following preparations are necessary to install QueryPie for testing and evaluation purposes.
- Fully Qualified Domain Name (FQDN) for accessing the product
- You can freely choose your desired domain. Example) querypie-poc.customer.com
- Load balancer (LB) and TLS certificate for the above FQDN
- QueryPie technical support personnel do not need direct access to TLS certificate files.
- However, QueryPie requires a load balancer (LB) with TLS applied.
- For AWS, Application Load Balancer corresponds to this.
- For Azure, Application Gateway corresponds to this.
- For GCP, Application Load Balancer corresponds to this.
- Linux VM to run QueryPie
- For evaluation purposes, it is recommended to use 4 vCPUs and 16GiB memory.
- While applying a load balancer is essential, there is no need to configure 2 or more VM instances.
- Even if QueryPie is installed on a single VM, you can effectively test the product’s features.
- Please temporarily allow remote access to your company’s Linux VM environment.
- You can provide temporary Azure, AWS, GCP accounts for load balancer and TLS setup. Please configure a Linux VM instance to be accessible via SSH public key and provide the SSH public key (.pem file).
Summary of System Configuration for Real Use
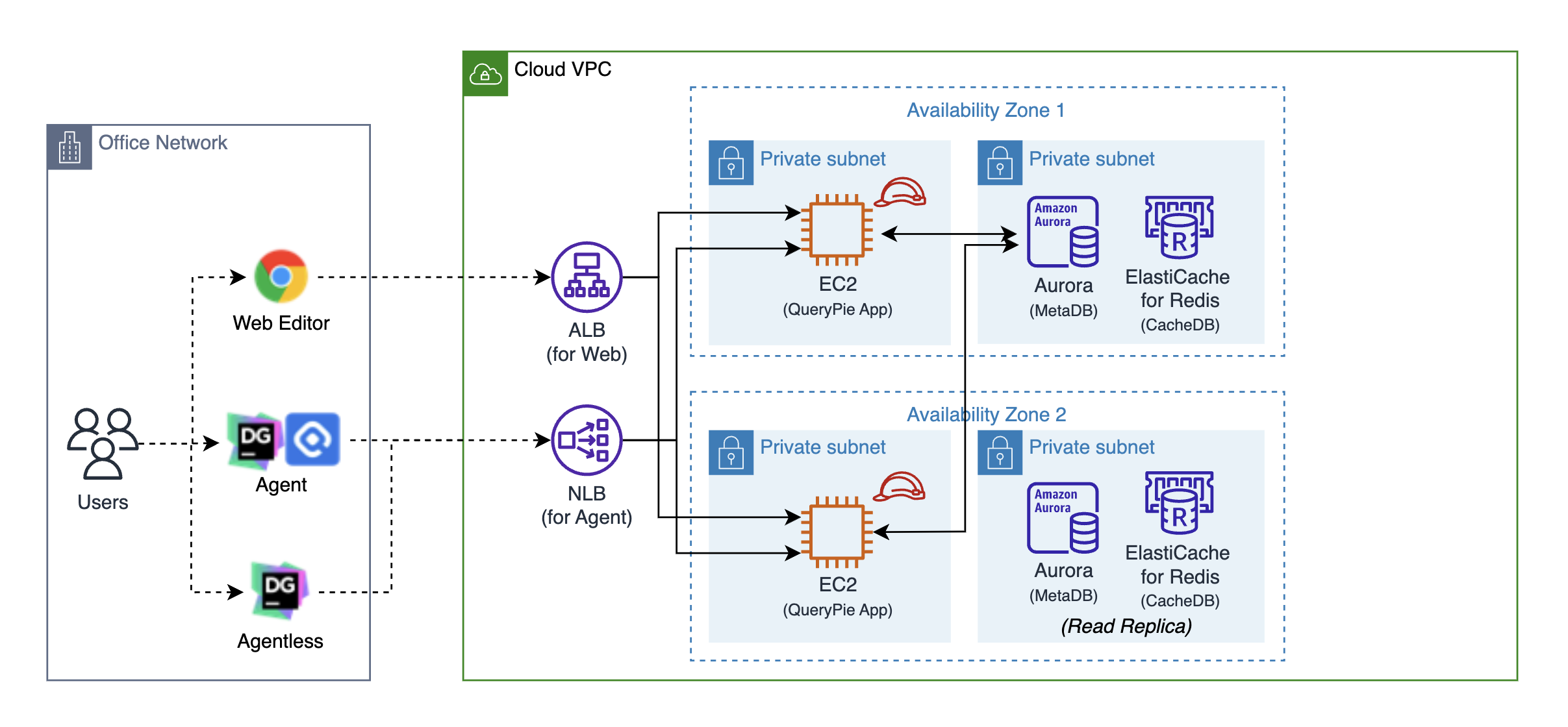
Summary of System Architecture for Real Use
The above configuration is a summarized diagram to help users understand, not a detailed system architecture.
The above configuration is an example that summarizes the main elements of the system configuration applied when using the actual QueryPie product. Users can connect to and use QueryPie through a web browser. Additionally, to access databases and systems using applications running on user PCs such as DataGrip, MySQL Workbench, iTerm, and PuTTY, you can install and use the QueryPie Agent on your PC.
The QueryPie server configured in a cloud environment has a redundant configuration to operate as a web application, and it is recommended to use MySQL and Redis in Managed Service mode provided by the cloud. The QueryPie Agent installed on PCs connects to the QueryPie server using a TCP-based proprietary protocol, and it is recommended to configure a Network Load Balancer for this purpose.