Granting and Revoking Kubernetes Roles
Overview
Administrators can grant or revoke roles with Kubernetes API access permissions to users or user groups.
Granting Kubernetes Roles
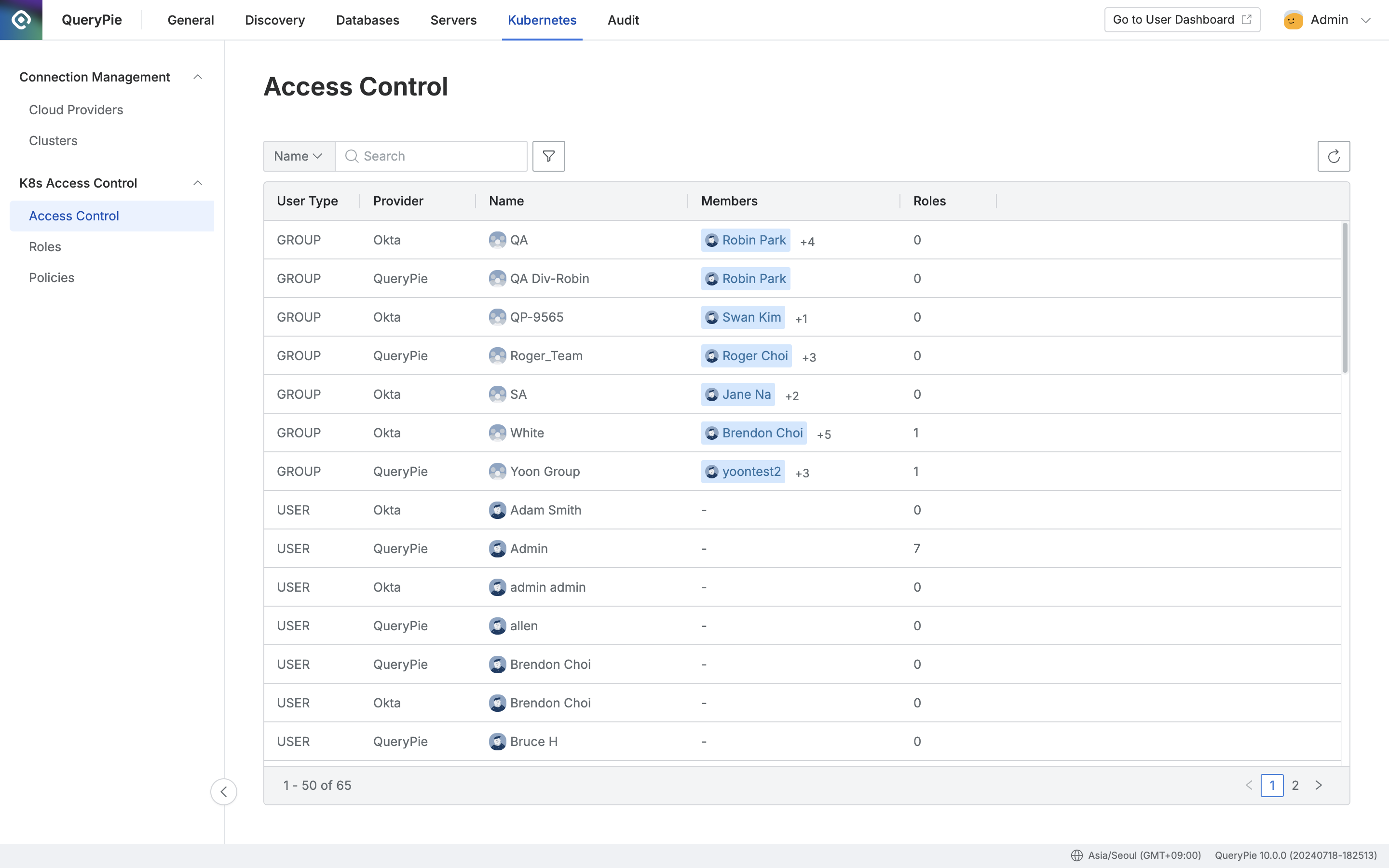
Administrator > Kubernetes > K8s Access Control > Access Control
- Navigate to Administrator > Kubernetes > K8s Access Control > Access Control menu.
- Select the user or user group to grant permissions to and move to the detailed page.
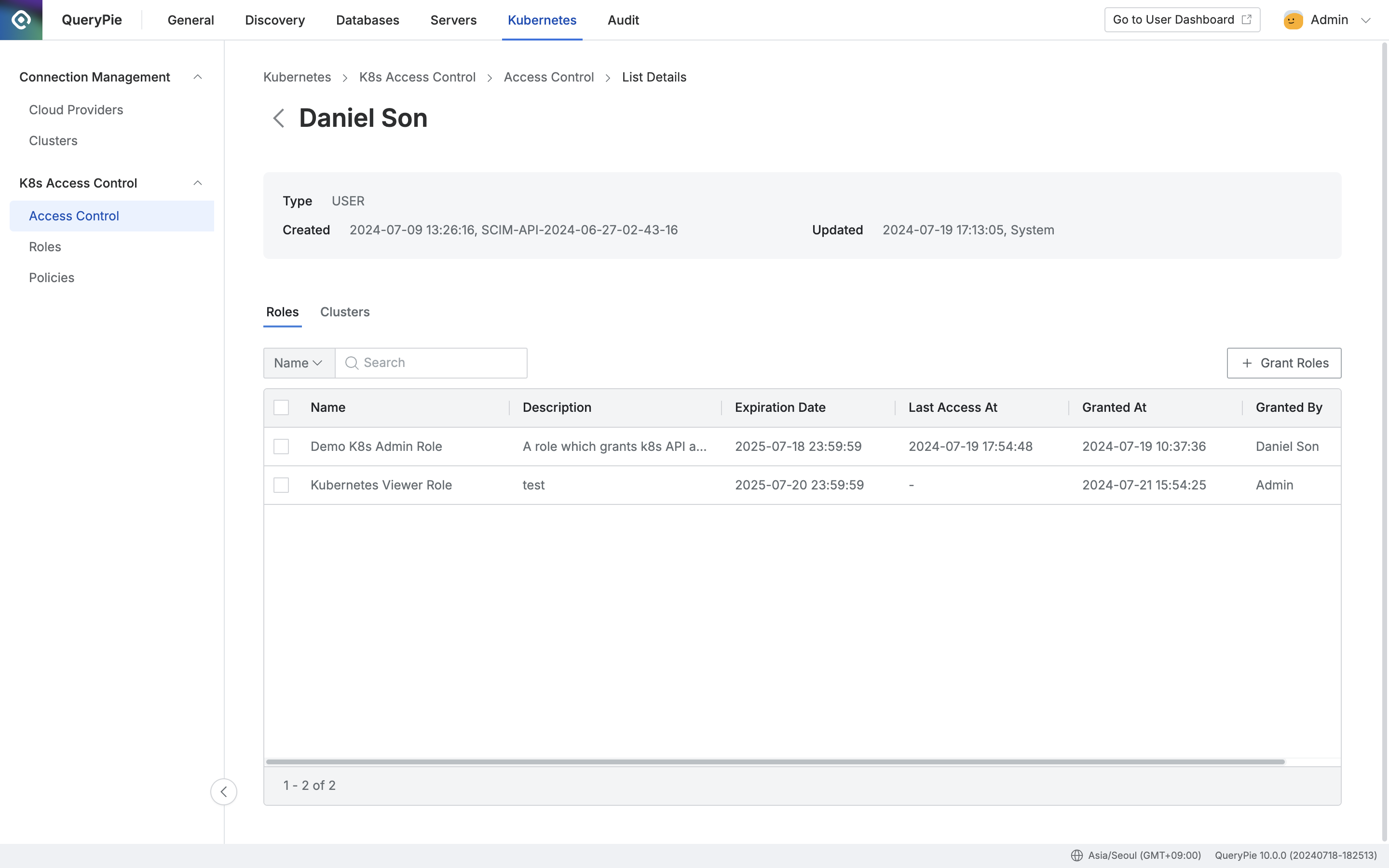
Administrator > Kubernetes > K8s Access Control > Access Control > List Details
- Click the
+ Grant Rolesbutton on the right of the Roles tab, check the checkbox on the left of the Role to grant, and specify the expiration date.
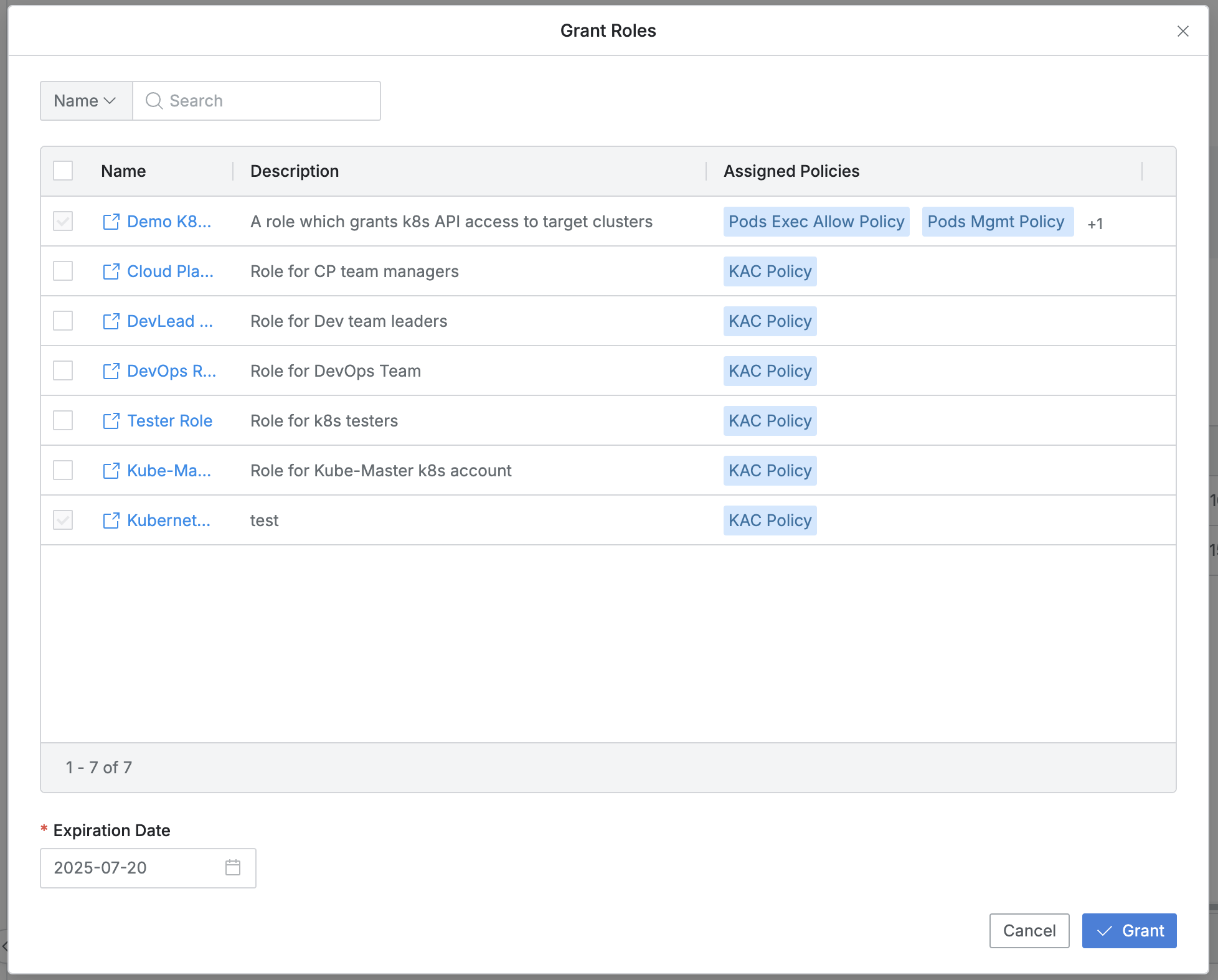
- You can search by Role name.
- Already assigned roles have disabled checkboxes.
- The list exposes the following information for each policy:
- Name : Role name
- Provides a new window link to view role information.
- Description : Role detailed description
- Assigned Policies : Lists assigned policy list
- Name : Role name
- Expiration Date : Expiration date must be specified as required.
- When set as default, it is set to one year from the current point, and can be set up to a maximum of one year.
- Click the
Grantbutton to assign the checked target Role. - (Clicking the
Cancelbutton closes the modal without changes.)
Revoking Kubernetes Roles
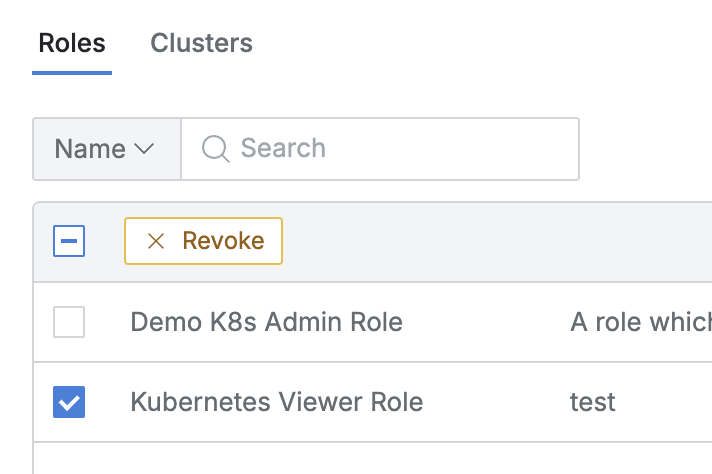
- Navigate to Administrator > Kubernetes > K8s Access Control > Access Control menu.
- Select the user or user group to revoke permissions from and move to the detailed page.
- In the Roles tab, click the
Revokebutton exposed in the column bar when checking the select all or individual selection box.
- When clicking the
Revokebutton in the confirmation window, the selected role permissions are revoked from the user/group and disappear from the list. - (Clicking the
Cancelbutton only closes the confirmation window.)
When revoking a Role, all access permissions that were granted to users and groups through that role are revoked.
Last updated on