Overview
Innovative Access Control Solution, QueryPie Access Control Platform (ACP)
Due to the increasing frequency of data breaches caused by cyber threats and the growing number of privacy regulations, more and more companies are considering adopting security solutions. QueryPie Access Control Platform (ACP) offers an optimized solution not only for on-premises environments but also for various clouds, providing an integrated security platform that covers database, system, and container access control as well as auditing.
QueryPie ACP is a powerful security solution optimized for automating security operations and easy integration with various platforms—reducing time and cost while enhancing operational stability. It also offers user- and admin-friendly features that improve productivity. Manage your dispersed assets and permissions in one place with QueryPie ACP.
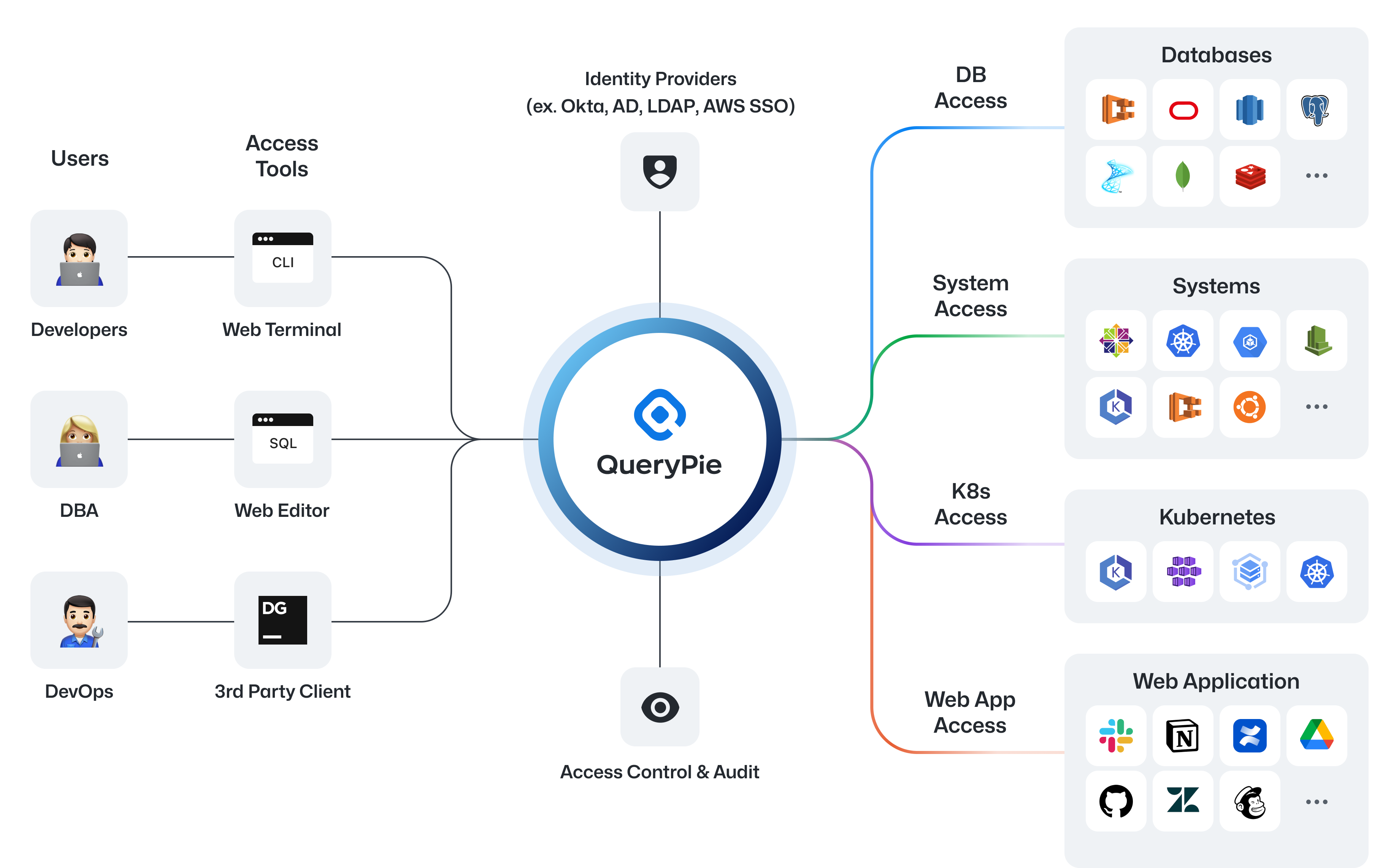
How QueryPie Access Control Platform Works
Using This Manual
QueryPie ACP continuously explores ways to securely protect sensitive data within enterprises, even in cloud environments. Currently, QueryPie ACP primarily provides database, system, and Kubernetes access control and auditing, along with access control for web applications.
This document provides guidance for security practitioners on installing QueryPie ACP after adoption, performing initial system configuration, registering and managing resources, configuring policies, and monitoring audit logs—so you can reliably establish access control and auditing within your organization using QueryPie ACP.
Key Features of QueryPie ACP
- Fine-grained access control: Control user permissions at the levels of network, database tables and columns, and system protocols to ensure users can access only the resources required for specific tasks.
- Unified interface: Manage multiple database and system platforms through an intuitive, single web-based interface. QueryPie integrates with multiple cloud providers to simplify the management of resources subject to access control.
- Real-time monitoring: Gain insight into user activities through real-time monitoring and auditing. Track anomalous access attempts, unnecessary query executions, data modification attempts, and potential security violations to maintain a strong security posture.
- Workflow integration: Streamline the process of requesting and approving access permissions with workflow features. Automate processes such as access requests and query execution requests to collaborate efficiently on tasks that require approval and auditing.
- Data masking: Protect personal and sensitive data by applying data masking policies. Even for authenticated users, you can require additional authentication for masked data or allow temporary exceptions via workflows (electronic approvals).
- Compliance: Comply with domestic and international regulatory requirements. Quickly identify personal data defined by regulations using predefined detection patterns and AI identifiers, and export audit logs as reports to support certification and audits.