Setting Kubernetes Roles
Overview
Apply role-based access control (Role-Based Access Control, RBAC) based on Kubernetes roles within the organization to allow or restrict user access to Kubernetes. You can grant set Roles to users or user groups. Roles are used to define multiple policies as a single role.
Assigning Role Policies
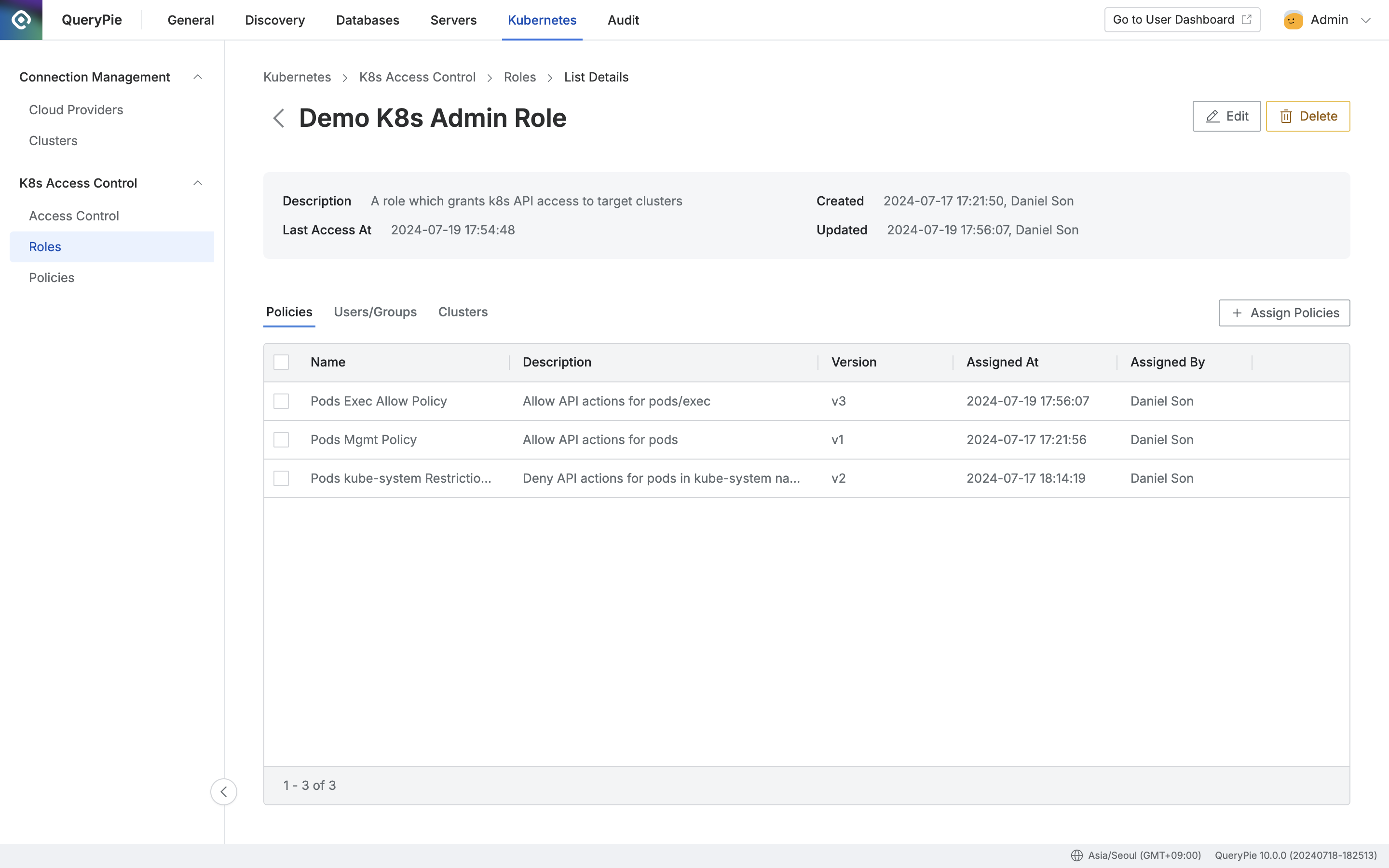
Administrator > Kubernetes > K8s Access Control > Roles > List Details
- Navigate to Administrator > Kubernetes > K8s Access Control > Roles menu.
- Click on the target Role row from the Roles list to move to the detailed page.
- Click the
+ Assign Policiesbutton on the right of the Policies tab. - Review the policies to assign, then check the checkbox on the left.
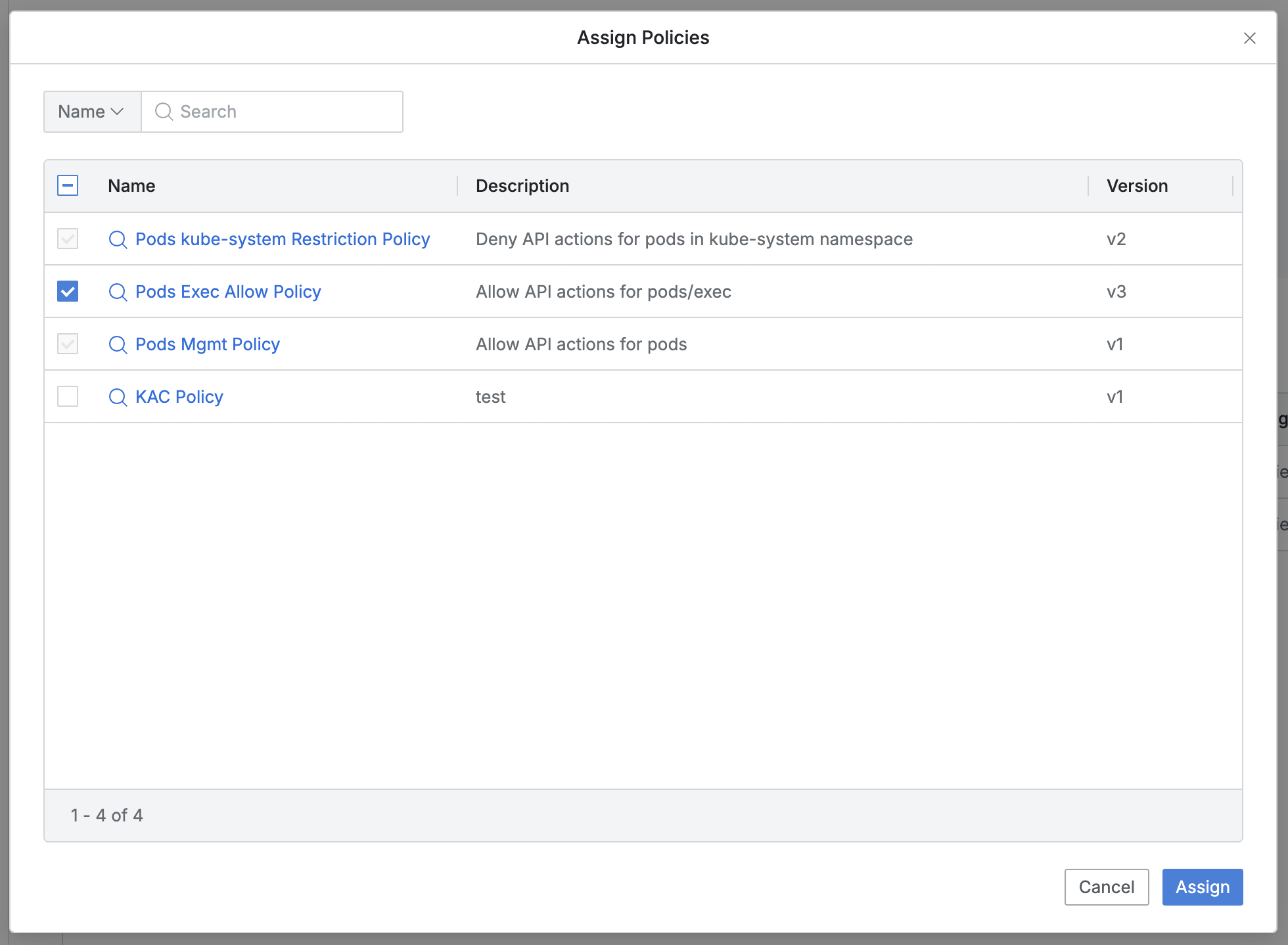
- You can search by policy name.
- Already assigned policies have disabled checkboxes.
- The list exposes the following information for each policy:
- Name : Policy name
- Provides a modal link to view policy information.
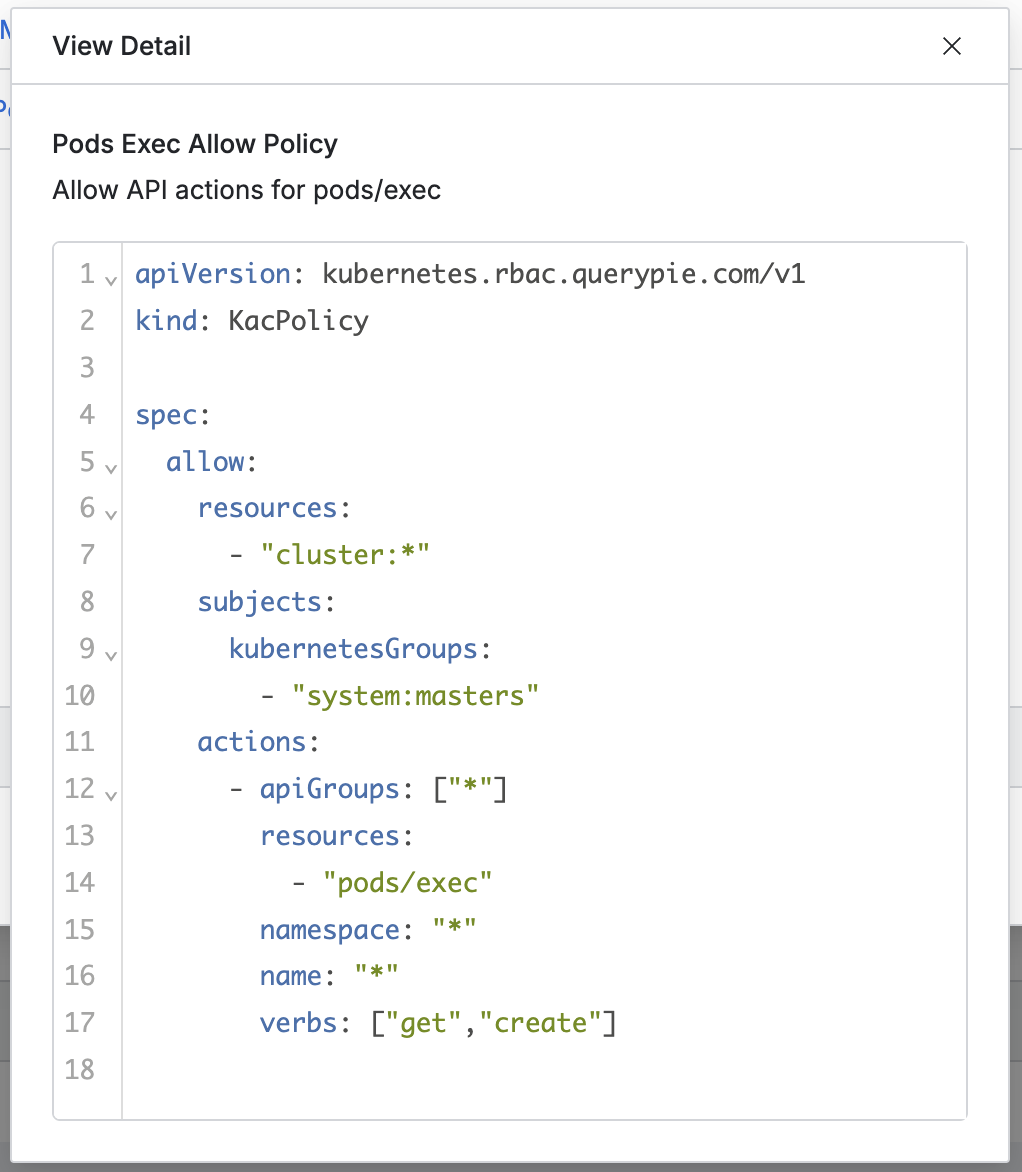
- Provides a modal link to view policy information.
- Name : Policy name
- Press the
Assignbutton to assign the checked target policies. - (Pressing the
Cancelbutton closes the modal without changes.)
Unassigning Role Policies
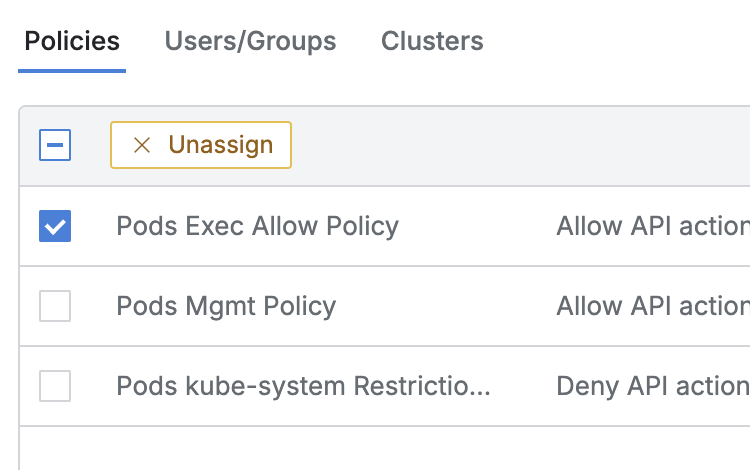
- Navigate to Administrator > Kubernetes > K8s Access Control > Roles menu.
- Click on the target Role row from the Roles list to move to the detailed page.
- In the Policies tab, click the
Unassignbutton exposed in the column bar when checking the select all or individual selection box.
- When clicking the
Unassignbutton in the confirmation window, the selected items are unassigned and disappear from the list. - (Clicking the
Cancelbutton only closes the confirmation window.)
When unassigning a Policy, all access permissions that were granted to users and groups through that policy are revoked.
Last updated on