Kubernetes Policy Action Configuration Reference Guide
Overview
In QueryPie KAC, you configure access control policies for k8s using YAML-based policies. This guide explains how to set Actions to avoid difficulties using client tools such as kubectl, Lens, and k9s due to misconfigured policies.
API Groups Configuration Guide
Commonly used resources like pods belong to the core group and thus use an empty string "" for apiGroups, whereas deployments and replicasets belong to "apps", and ingresses belong to "networking.k8s.io".
Of course, if resources have the same name, you may need to separate them via apiGroups, but that is not a common situation.
Therefore, unless you have a specific mission to manage Kubernetes API Groups, it is generally recommended to set apiGroups to "*" and control access via resources.
Resources Configuration Guide
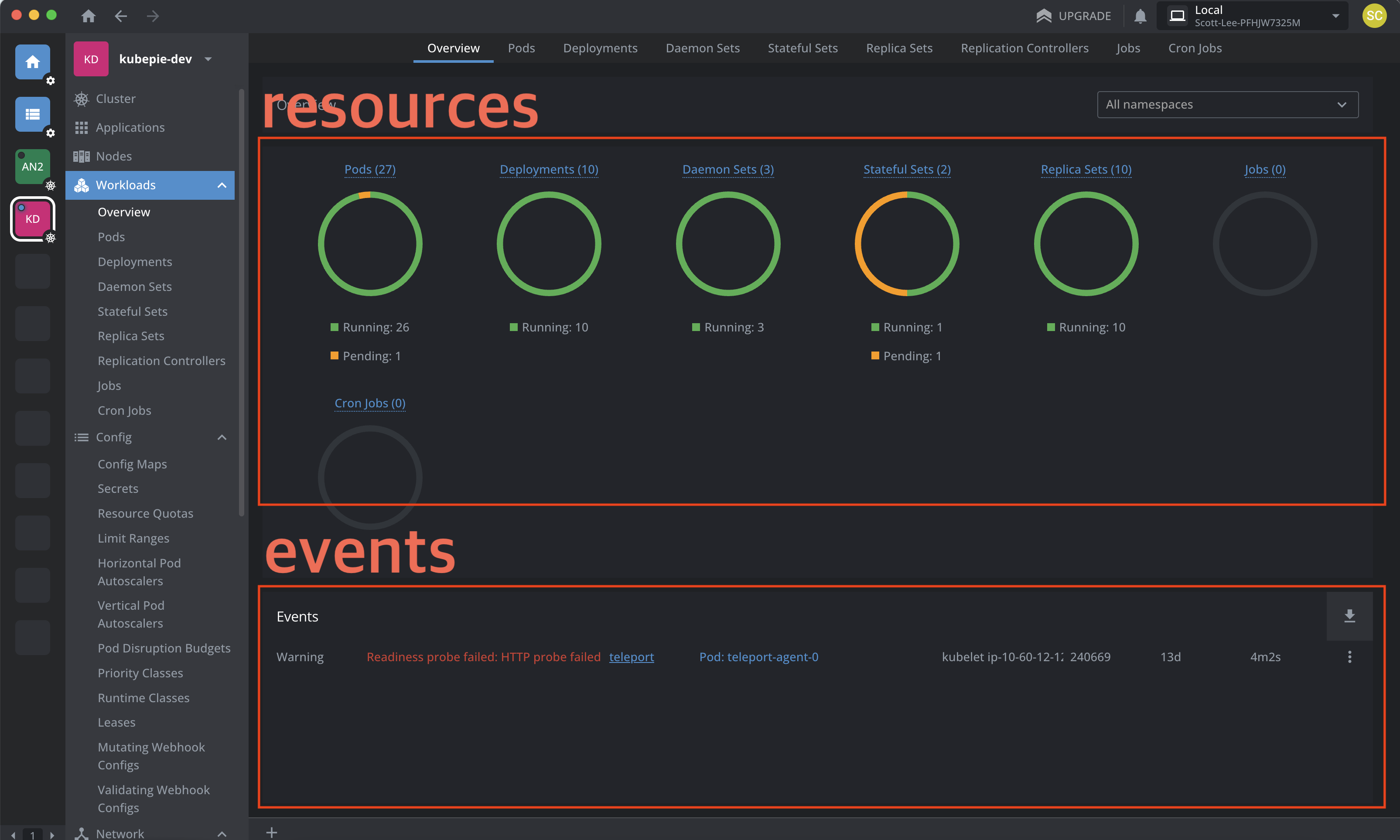
3rd Party Client Tool - Lens screen
When using 3rd-party client tools, you can monitor status within the permitted resource scope.
- Resources section
- In the screen above, only resources for which you have permissions are displayed.
- So if you only have permission for
pods, only the graph forpodsis shown, and ifpodsare filtered so you can only view some, only some are displayed. - Other resources work the same way.
- Recommended spec
allow: actions:
When allowing only Pods
- apiGroups: [""]
resources: [“pods”]
namespace: ""
name: ”*”
verbs: [“get”, “list”, “watch”]
- Events section
- The events section below is displayed based on permissions for the
eventsresource, and like the resources section above, it is filtered and displayed by namespace and name. - However, having permission for
podsdoes not meaneventsrelated topodsare displayed, so to view that screen, you must explicitly grant permission for theeventsresource. - The
eventsresource andpodsresource are separate resources. Therefore, if you only grant permission forpodswhile having permission for theeventsresource, it does not mean only the history ofeventsrelated topodsis retrieved. - Recommended spec
- The events section below is displayed based on permissions for the
allow: actions:
When allowing Events output together
- apiGroups: [""]
resources: [“pods”, “events”]
namespace: ""
name: ”*”
verbs: [“get”, “list”, “watch”]
Verbs Configuration Guide
The part that most affects 3rd-party client tool usage is verbs. Administrators specify the scope of resources users can access through apiGroups, resources, namespace, and name, and specify which APIs can be called via verbs, but even if you set the resource scope well, if you do not properly configure the verb groupings, tool usage becomes difficult.
- View permissions
- For users who only get View permissions, grant
get,list, andwatchall together. - Using kubectl is not too difficult with just
getandlist, but withoutwatch, tools like Lens that support live monitoring are difficult to use. - Recommended spec
- For users who only get View permissions, grant
allow: actions:
- apiGroups: [""]
resources: [""]
namespace: ""
name: ""
verbs: [“get”, “list”, “watch”]
- Edit permissions
- For users who also get Edit permissions, you must also grant View permissions (at minimum,
getandlist). This is because kubectl first performs a read before issuing a modification request for a given resource. - In tools like Lens, without View permissions there is no way to reach the Edit screen.
- For Edit, group the verbs by role: create (
create), modify (patch,update), delete (delete,deletecollection). - Although
deletecollectionis not commonly used, in KAC, even when adeletecollectionrequest is made, only resources for which the user has permissions are selected and deleted, so it can be useful. - Recommended spec
- For users who also get Edit permissions, you must also grant View permissions (at minimum,
allow: actions:
Create permissions
- apiGroups: [""] resources: [""] namespace: "" name: "" verbs: [“get”, “list”, “create”]
Update permissions
- apiGroups: [""] resources: [""] namespace: "" name: "" verbs: [“get”, “list”, “patch”, “update”]
Delete permissions
- apiGroups: [""]
resources: [""]
namespace: ""
name: ""
verbs: [“get”, “list”, “delete”, “deletecollection”]
Other recommended configuration examples
Example) Restrict permissions for resources in the prod namespace
allow:
actions:
- apiGroups: ["*"]
resources: ["*"]
namespace: "dev"
name: "*"
verbs: ["*"]
- apiGroups: ["*"]
resources: ["*"]
namespace: "prod"
name: "*"
verbs: ["get", "list", "watch"]Example) Restrict access to secrets in the prod namespace
deny:
actions:
- apiGroups: ["*"]
resources: ["secrets"]
namespace: "prod"
name: "*"
verbs: ["*"]