Kubernetes Policy UI Code Helper Guide
Overview
You can manage access policies (Policy) for Kubernetes clusters managed by the organization. Kubernetes policies are operated as Policy as a Code (PaC) and work based on YAML format. On the right side, a modal is provided as a Policy UI convenience feature to help users work with UI for content to be inserted into the code editor.
Using UI Code Helper
A code support modal for each field is provided on the right side of the code editor screen. The modal serves to help with code editing, and content inserted by the entire modal can be removed from the code editor.
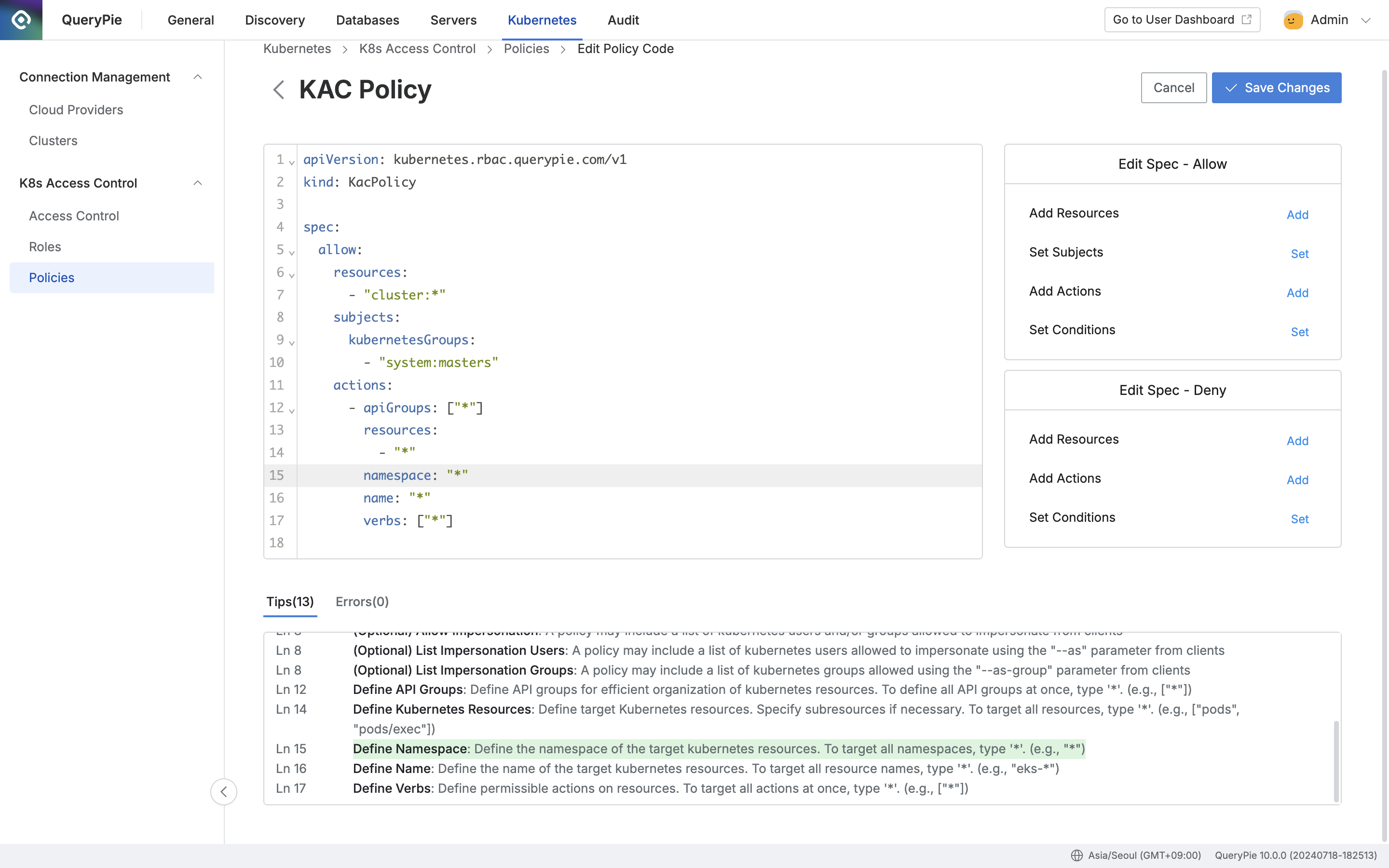
Administrator > Kubernetes > K8s Access Control > Policies > List Details > Go to Editor Mode
- Add Resources modal
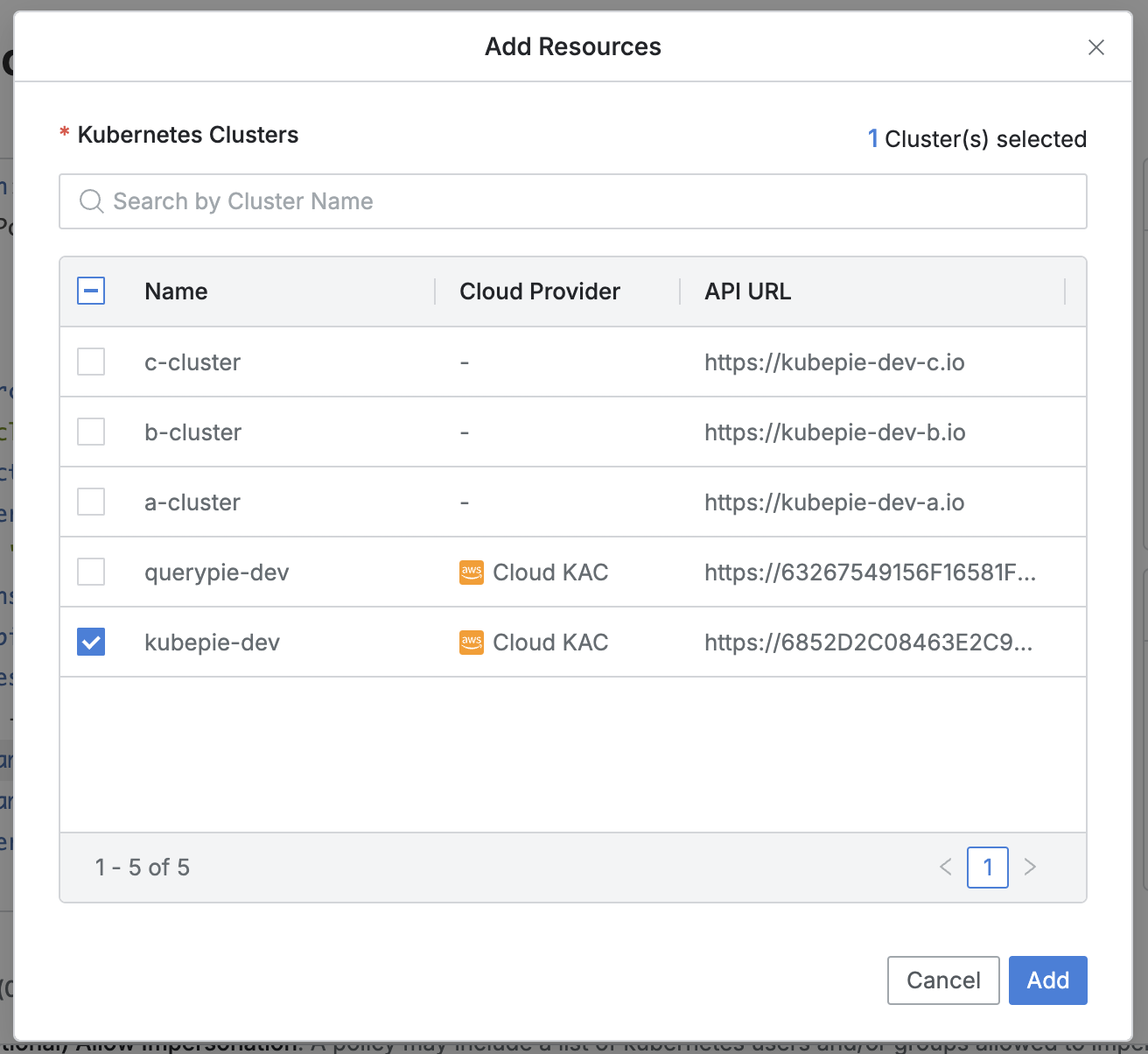
- Works the same in both Spec: Allow and Spec: Deny.
- You can search resources by cluster name.
- Click the
Addbutton to insert the checked resources into the code. - Set Subjects modal
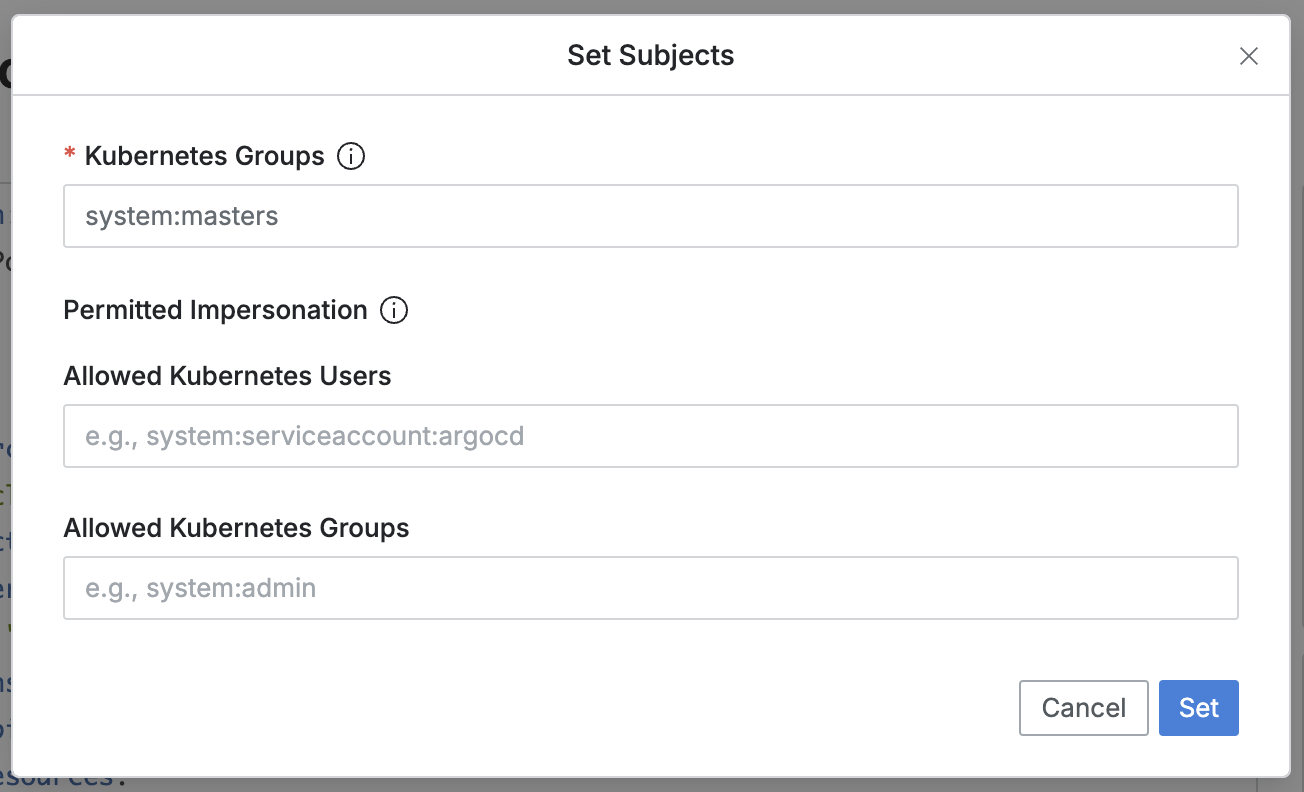
- Works only in Spec: Allow.
- Kubernetes Groups : (Required) Specifies the Kubernetes group that QueryPie Proxy will impersonate to perform API calls through this field.
- Permitted Impersonation : (Optional) Lists the Kubernetes users/groups that can be applied when users attempt impersonation through actual —as, —as-group through clients through this field.
- Allowed Kubernetes Users : Enter the kubernetes users to be allowed in QueryPie with the —as parameter.
- Allowed Kubernetes Groups : Enter the kubernetes groups to be allowed in QueryPie with the —as-group parameter.
- Multiple registration is possible through ’,’.
- The modal displays existing information based on the content in the editor, and when you press the
Setbutton, it overwrites the changes in the editor. - Add Actions modal
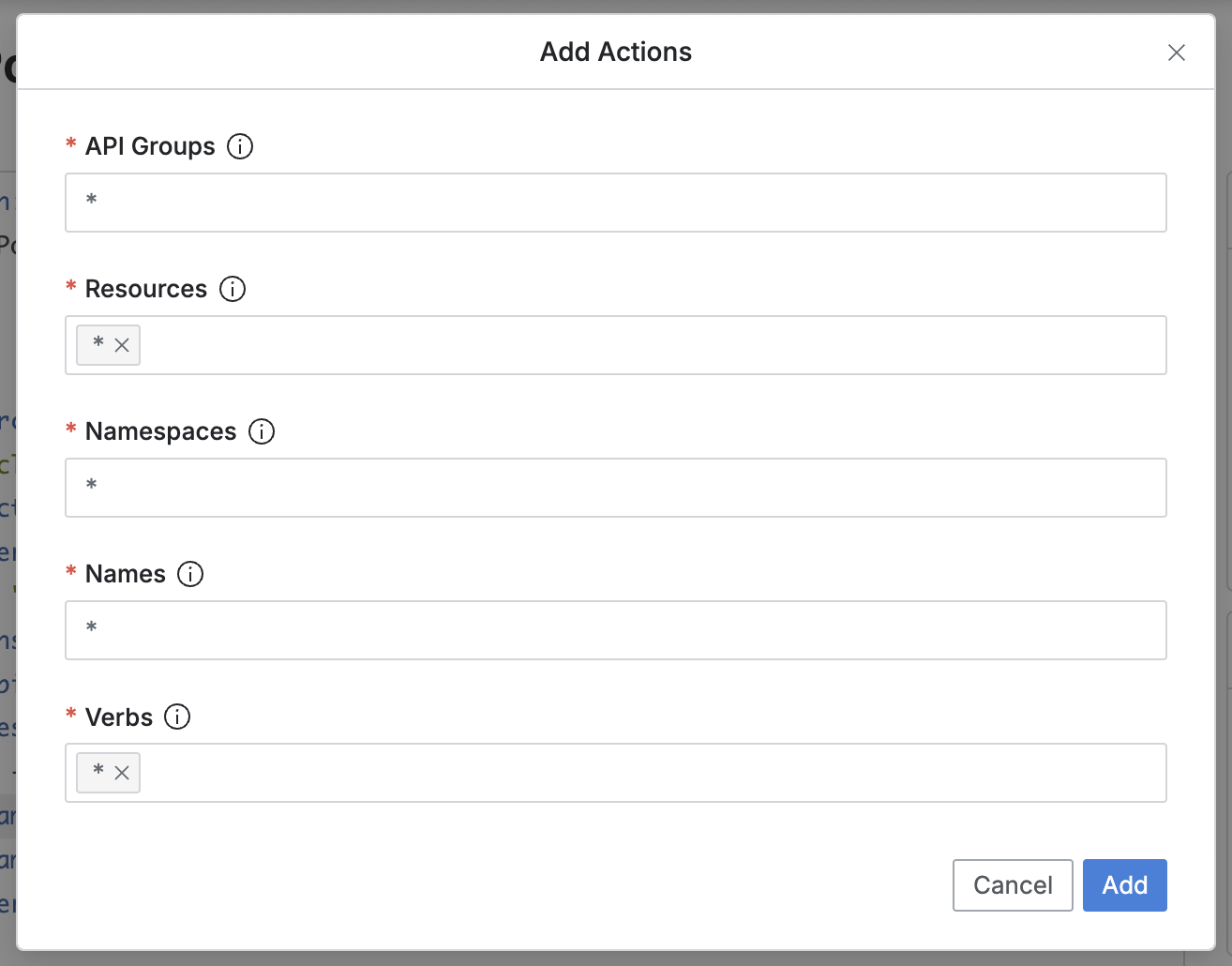
- Works the same in both Spec: Allow and Spec: Deny.
- API Groups : Provides ”*” by default; administrators can modify and enter multiple values with ’,’.
- Resources : Specifies Kubernetes resources.
- Provides ”*” by default; administrators can modify and enter multiple values.
- Commonly used resources are as follows, and you can easily select resources from the following list by placing the cursor in the field:
pods,pods/exec,pods/log,pods/portforward,services,ingresses,deployments,replicasets,statefulsets,daemonsets,configmaps,secrets,namespaces,nodes,persistentvolumes,persistentvolumeclaims,jobs,cronjobs,serviceaccounts,endpoints,roles,rolebindings,clusterroles,clusterrolebindings
- Resources not listed above can be specified by directly typing to specify resources outside the list (for custom resource support).
- When specified, it is displayed like an Item block and can be removed by pressing X.
- Namespace : Specifies namespaces to limit the scope of Kubernetes resources.
- Provides ”*” by default; administrators can modify and wildcards and regular expressions are accepted.
- For Resources outside the Namespace scope, the value of the field is not affected by any value that comes in.
- Out-of-scope resources:
persistentvolumes,persistentvolumeclaims,serviceaccounts,customresourcedefinitions,endpoints,nodes,clusterroles,clusterrolebindings
- Out-of-scope resources:
- Name : Enter the resource name to be targeted among Kubernetes resources.
- Provides ”*” by default; administrators can modify and wildcards and regular expressions are accepted.
- Verbs : Multiple Kubernetes API methods can be set.
- Provides ”*” by default; when specified, it is displayed like an Item block and can be removed by pressing X.
- Commonly called Verbs are as follows, and you can easily select Verbs from the following list by placing the cursor in the field:
get,list,watch,create,update,patch,delete,deletecollection
- Users can directly type to specify other verb names for custom resources outside the list.
- Click the
Addbutton to define one action set among the actions list. - In terms of code, it corresponds to the append part, so new additions are possible without initializing previously added actions.
- Set Conditions modal
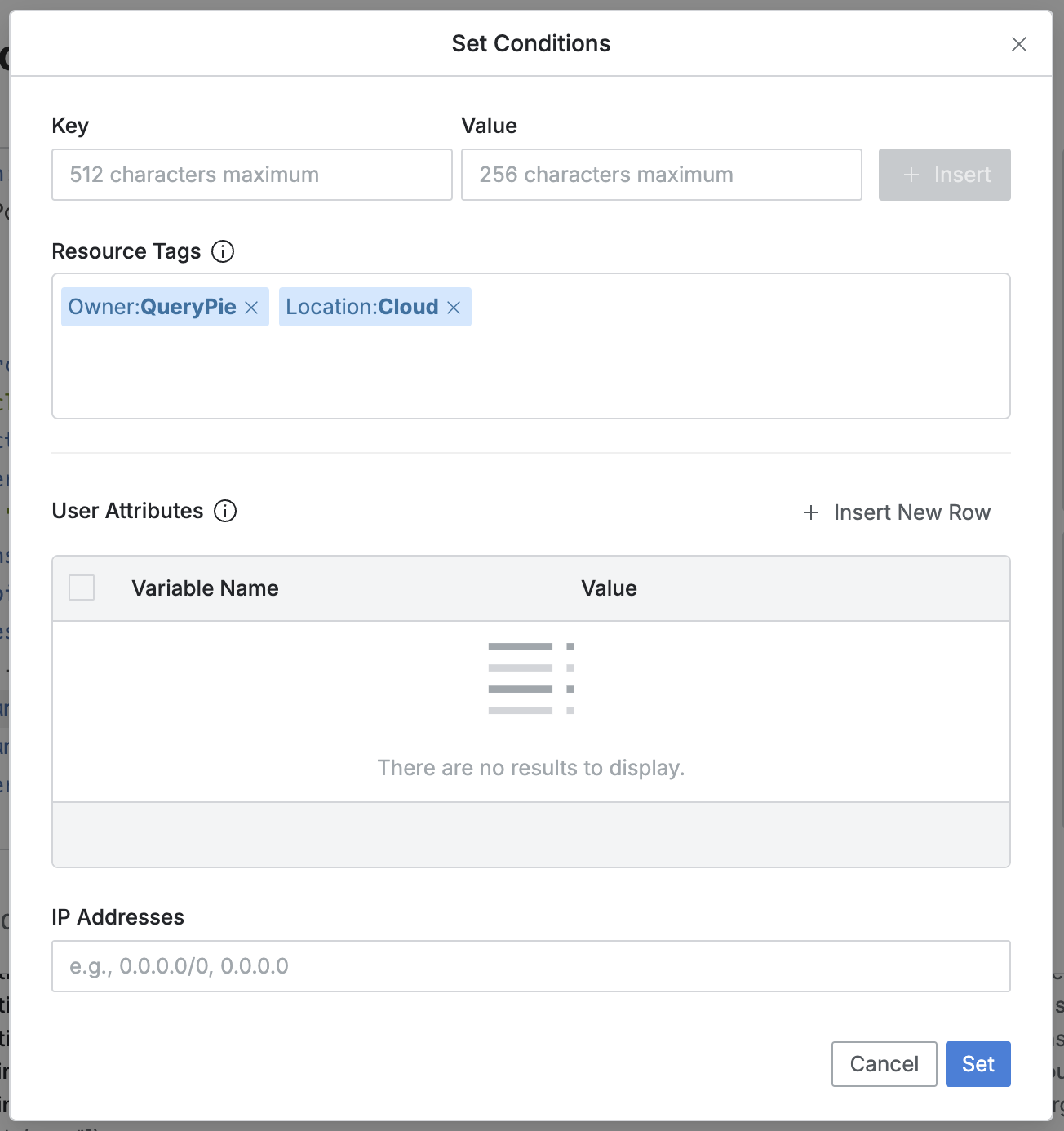
- All items are optional.
- The modal displays existing information based on the content in the editor, and when you press the
Setbutton, it overwrites the changes in the editor. - Resource Tags (Optional)
- You can reduce the policy application scope based on tags attached to QueryPie resources.
- Each row operates as an AND condition; OR operation with ’,’ in Value.
- You can create a new row by pressing the Insert button.
- When specified, it is displayed like a tag block and can be removed by pressing X.
- Entry items:
- Key : Tag key (regex, glob not supported)
- Value : Tag value entry (both regex and glob supported, multiple input supported)
- User Attributes (Optional)
- You can reduce the target scope of policy application based on QueryPie user attributes.
- If all attribute values do not match, the user cannot use the policy even if it was assigned until the attribute values match.
- Each row operates as an AND condition; OR operation with ’,’ in Value.
- The dropdown list suggests currently supported Attributes in Variable Name.
- loginId, firstName, lastName, middleName, honorificPrefix, honorificSuffix, email, title, displayName, nickName, profileUrl, secondEmail, mobilePhone, primaryPhone, streetAddress, city, state, zipCode, countryCode, postalAddress, preferredLanguage, locale
timezone, userType, employeeNumber, costCenter, organization, division, department, managerId, manager, endpoints, staticIp, macAddress
- loginId, firstName, lastName, middleName, honorificPrefix, honorificSuffix, email, title, displayName, nickName, profileUrl, secondEmail, mobilePhone, primaryPhone, streetAddress, city, state, zipCode, countryCode, postalAddress, preferredLanguage, locale
- IP Addresses (Optional)
- Administrators specify IP ranges that can or cannot access the resource.
- Both single IP and CIDR are accepted with ’,’ as separator.
Last updated on